kestrel-lang v1.8 releases: provides an abstraction for threat hunters
Kestrel Threat Hunting Language
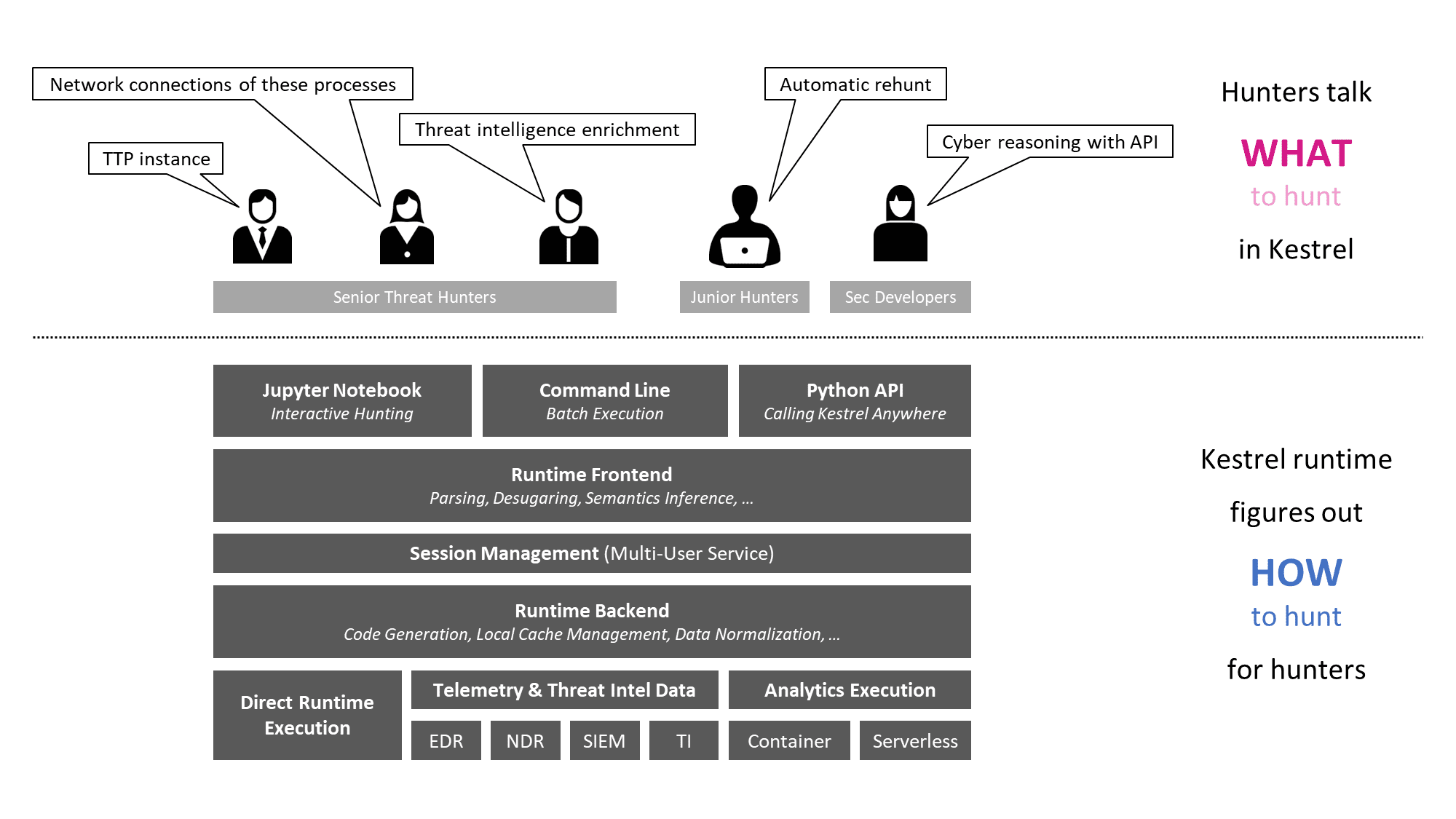
Kestrel threat hunting language provides an abstraction for threat hunters to focus on what to hunt instead of how to hunt. The abstraction makes it possible to codify reusable hunting knowledge in a composable and sharable manner. And Kestrel runtime figures out how to hunt for hunters to make cyber threat hunting less tedious and more efficient.

- Kestrel language: a threat hunting language for a human to express what to hunt.
- expressing the knowledge of what in patterns, analytics, and hunt flows.
- composing reusable hunting flows from individual hunting steps.
- reasoning with human-friendly entity-based data representation abstraction.
- thinking across heterogeneous data and threat intelligence sources.
- applying existing public and proprietary detection logic as analytics.
- reusing and sharing individual hunting steps and entire hunt books.
- Kestrel runtime: a machine interpreter that deals with how to hunt.
- compiling the what against specific hunting platform instructions.
- executing the compiled code locally and remotely.
- assembling raw logs and records into entities for entity-based reasoning.
- caching intermediate data and related records for fast response.
- prefetching related logs and records for link construction between entities.
- defining extensible interfaces for data sources and analytics execution.
Changelog v1.8
- Split Kestrel Python packages and creates version 1.8.0 for all Kestrel packages
- Merge kestrel-jupyter into the kestrel-lang repo
- Establish the new practice to release Kestrel (updated packages grouped by date)
- Update installation document to use
kestrel-jupyteras the umbrella package to install the latest Kestrel packages - Add a small feature to hide credentials in debug log




