Kimsuky APT Group Targets University Researchers in Espionage Campaign
The North Korean state-backed hacking group known as Kimsuky is at it again, this time setting its sights on university researchers and professors in an ongoing espionage campaign. A recent report from Resilience Threat Intelligence reveals that Kimsuky is using phishing attacks and compromised email accounts to gain access to university networks and steal valuable research data.
Universities have long been a treasure trove of intellectual property and cutting-edge research. Kimsuky’s interest in these institutions is a logical extension of their mission: to gather intelligence that aligns with the interests of the North Korean government. The group’s latest campaign, which began in the Spring of 2024, is particularly concerning due to its precision and sophistication.
The campaign leverages targeted phishing attacks, a hallmark of Kimsuky’s operations. The group establishes trust with its victims through email correspondence before sending malicious attachments that, once opened, give them access to university networks. From there, Kimsuky can siphon off valuable research, which the North Korean government uses to bolster its scientific community—a sector in which the country is significantly lacking.
In late July 2024, Resilience analysts observed a rare Operational Security (OPSEC) mistake made by Kimsuky operators. This error provided analysts with unprecedented access to the group’s inner workings. The data haul included source code, login credentials, traffic logs, and internal notes, all pointing to a focused campaign against university researchers.
The documents revealed that Kimsuky is phishing university staff, researchers, and professors, aiming to infiltrate university networks. The implications of these actions are significant, as the stolen research can range from nuclear weapons technology to healthcare and pharmaceutical advancements. In addition, Kimsuky has been linked to financially motivated cybercrimes, which are believed to fund their espionage activities.
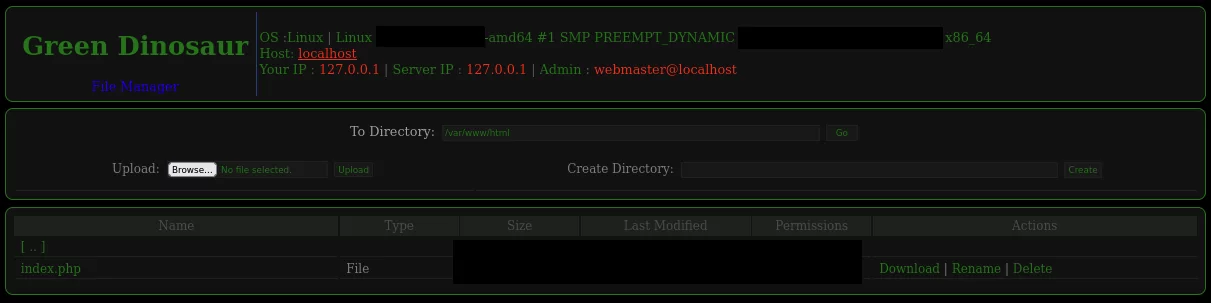
Kimsuky’s attacks are staged from a series of compromised internet hosts. The Resilience team identified several domains, such as audko[.]store and wodos[.]xyz, used to stage their attacks. A key component of their infrastructure is a webshell dubbed “Green Dinosaur,” a modified version of the Indrajith Mini Shell 2.0. This webshell allows Kimsuky operators to upload, download, and manipulate files on compromised servers, all while avoiding detection.
Green Dinosaur is heavily obfuscated, with multiple layers of base64 and gz deflated strings, making it difficult for hosting companies to detect. The webshell is the launchpad for Kimsuky’s phishing pages, which are meticulously crafted to mimic legitimate university login portals.
Once inside the network, Kimsuky deploys phishing pages designed to steal login credentials. The group’s targets include Dongduk University, Korea University, and Yonsei University. These phishing pages are near-perfect replicas of the universities’ real login pages, but with subtle modifications that divert entered credentials to Kimsuky-controlled servers.
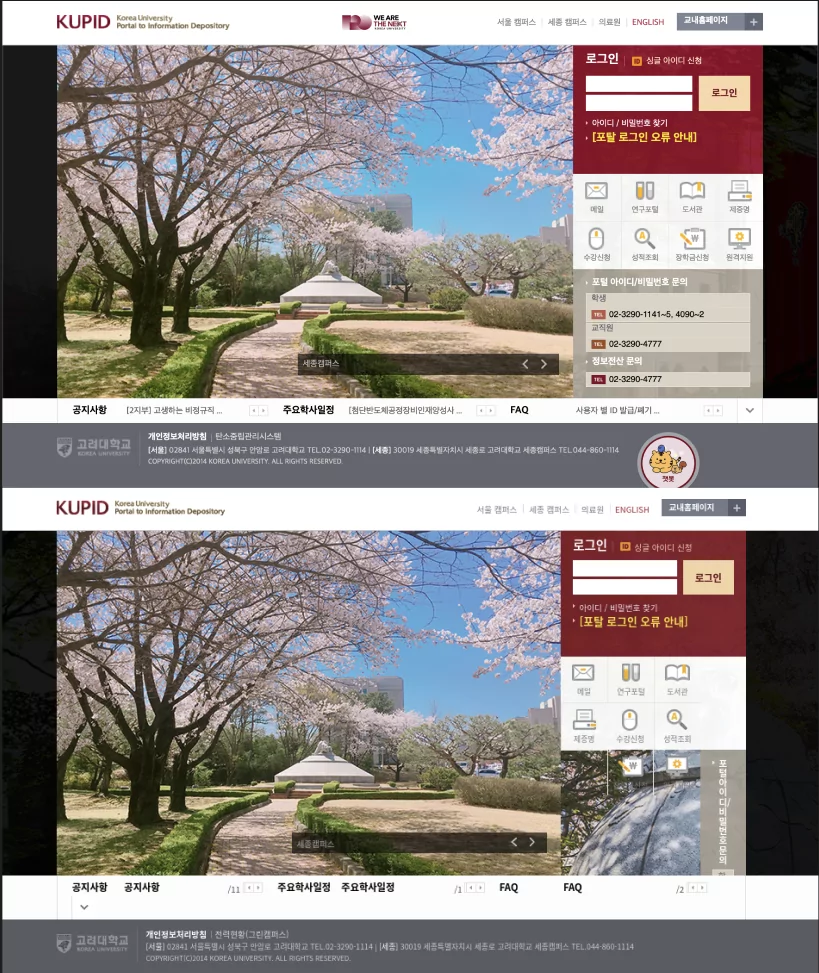
The legitmate Korea University login page (Top) and Kimsuky’s malicious login page (Bottom) show stark similarities | Image: Resilience
For instance, the phishing page for Dongduk University redirects victims to a fake “Login Fail” page after their first attempt, prompting them to re-enter their credentials. This ensures that Kimsuky captures the correct password without typos. The final step redirects the victim to a legitimate-looking PDF, reinforcing the illusion of authenticity.
In addition to targeting specific universities, Kimsuky has developed a phishing toolkit for stealing Naver accounts. This toolkit acts as a proxy, capturing cookies and credentials from unsuspecting victims. The group uses a custom PHPMailer implementation called “SendMail” to distribute phishing emails. These emails often appear to be from legitimate sources, such as professors or university administrators, further increasing their credibility.
The SendMail tool was found to be preconfigured with multiple phishing email templates, including subjects like “네이버 아이디 탈퇴가 완료되었습니다” (Translation: Naver ID was successfully deleted) and “[네이버]메일 송수신 기능 제한 알림.” (Translation: There are restrictions with sending and receiving Naver mail).
Kimsuky’s latest operations underscore the persistent threat posed by state-sponsored APT groups. Their ability to adapt and target new sectors, such as academia, highlights the need for robust cybersecurity measures. Universities and research institutions must remain vigilant and proactive in defending against these sophisticated attacks, as the consequences of a successful breach could be catastrophic.
Related Posts:
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report
- North Korean APT Group Kimsuky Targets Japanese Organizations with Stealthy Malware Campaign
- QiAnXin Uncovers New Kimsuky Malware Campaign
- Mandatory Ransomware Reporting: UK’s New Cyber Defense
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger





