HappyDoor’s execution flow
The AhnLab Security Intelligence Center (ASEC) has issued a warning about a new backdoor malware called HappyDoor, linked to the Kimsuky group, a North Korean state-sponsored threat actor. HappyDoor is a sophisticated and continuously evolving malware that has been used in numerous data breaches since 2021.

HappyDoor first appeared on ASEC’s radar in 2021, and subsequent investigations have shown that it has been actively used in cyberattacks up to the present day. The malware’s name is derived from the hardcoded “happy” string found in its debug string and export DLL name. Notably, the latest version (4.2), created on January 12, 2024, showcases the continuous efforts by the threat actors to patch and improve the malware.
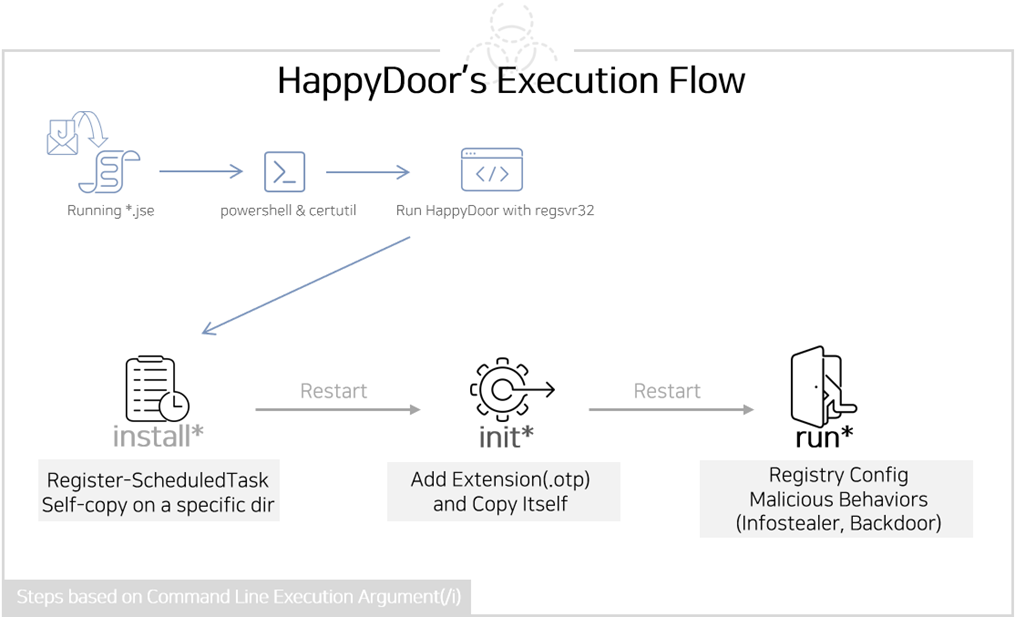
Kimsuky has historically utilized spear phishing email attacks to distribute various malware strains, and HappyDoor is no exception. The group sends emails containing compressed files that house either a JScript or an executable dropper. Once executed, HappyDoor is deployed alongside legitimate bait files, making detection more challenging. This method has been consistent with previous distribution tactics for other Kimsuky malware like AppleSeed and AlphaSeed.
HappyDoor’s execution arguments distinguish it from other backdoors. These arguments operate with an asterisk (*) added and are divided based on the identity of the arguments. For instance, from December 2023 to April 2024, HappyDoor used specific arguments like “syrsd” and “s*” for its operations.
Since its inception, HappyDoor has undergone significant changes. Initially collected in 2021, the malware lacked execution arguments. However, starting from version 4.1 in 2023, execution arguments were introduced, allowing HappyDoor to perform specific malicious activities based on these commands. The evolution of these arguments indicates a strategic enhancement to its functionality.
HappyDoor is equipped with six distinct information-stealing features, which include:
- Screenshot Capture (ssht): Captures the current screen and saves it as a JPG file.
- Keylogger (klog): Records keystrokes along with the current time and processes.
- File Monitoring (fmon): Collects files from specific paths and with certain extensions, focusing on recently modified files.
- USB Alarm (ausb): Collects information related to connected portable devices.
- Voice Recording (mrec): Activates the microphone to record and save audio files.
- Android File Monitoring (mtpmon): Collects files from connected Android devices via Media Transfer Protocol (MTP).
These features operate via multithreading, and the collected data is encrypted and sent to command-and-control (C2) servers. The encryption process employs an RSA public key and a randomly generated RC4 key, ensuring that the data remains secure during transmission.
HappyDoor can execute a variety of backdoor commands, including:
- Terminate: Ends the backdoor operation.
- Sleep: Puts the main thread to sleep for a specified time.
- Restart: Restarts the backdoor.
- Update: Loads a new DLL file, replacing the old one.
- Run Command Line: Executes commands received as arguments.
- Collect Information: Gathers OS information and backdoor configurations.
These commands enable the threat actor to maintain control over the infected system and carry out further malicious activities.
ASEC urges individuals and organizations to be vigilant against spear-phishing emails and to implement robust security measures to protect against HappyDoor and other malware threats. This includes keeping software up to date, using strong passwords, and employing multi-factor authentication. For more detailed information, visit the AhnLab Security Intelligence Center.