Kismet 2022-01-R2 releases: wireless network detector, sniffer, intrusion detection system
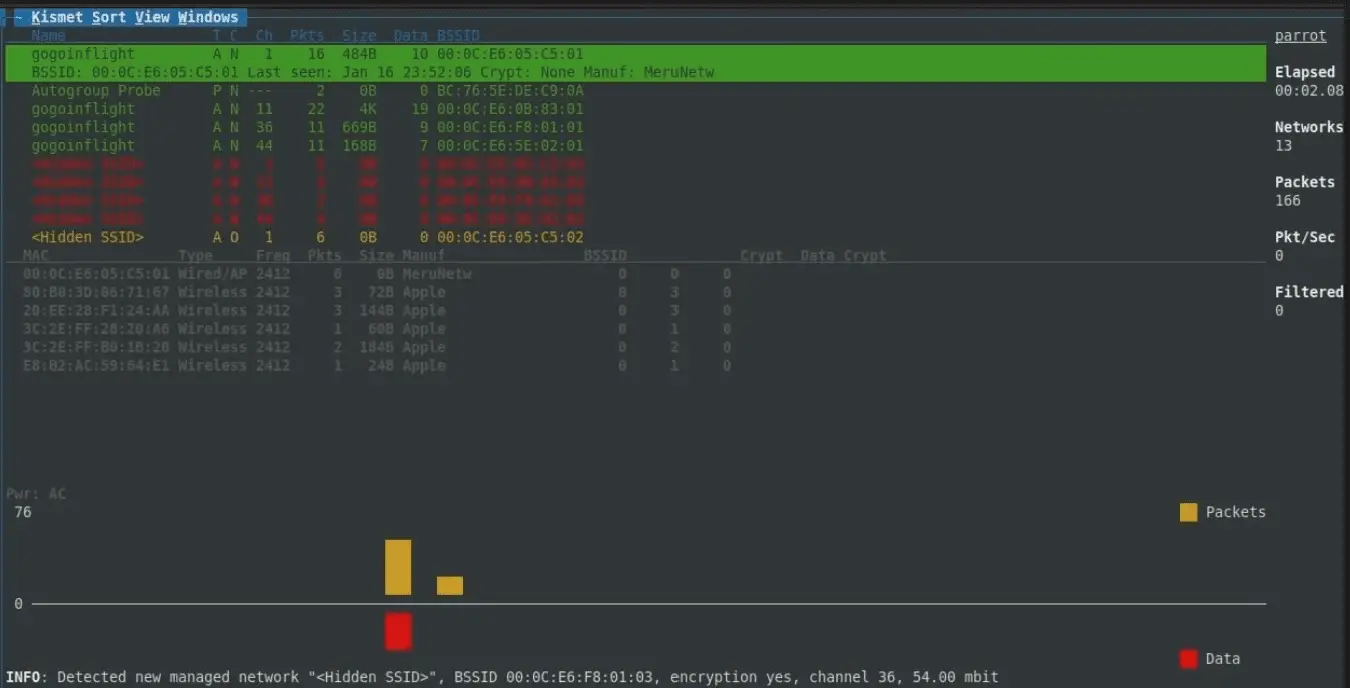
Kismet is an 802.11 layer2 wireless network detector, sniffer, and intrusion detection system. Kismet will work with any wireless card which supports raw monitoring (rfmon) mode and can sniff 802.11b, 802.11a, and 802.11g traffic. Kismet identifies networks by passively collecting packets and detecting standard named networks, detecting (and given time, decloaking) hidden networks, and inferring the presence of nonbeaconing networks via data traffic.
It works on Linux, OSX, and, to a degree, Windows 10 under the WSL framework. On Linux, it works with most Wi-Fi cards, Bluetooth interfaces, and other hardware devices. On OSX it works with the built-in Wi-Fi interfaces, and on Windows 10 it will work with remote captures.
Kismet supports logging to the wtapfile packet format (readable by tcpdump and ethereal) and saves detected
network informat as plaintext, CSV, and XML. kismet is capable of using any GPS supported by gpsd and logs and
plots network data.
kismet is divided into three basic programs, kismet_server kismet_client, and gpsma.
Changelog 2022-01-R2
2022-01-R2 is a minor update on top of the updates for 2022-01, with:
- Fix alert-syslog pluginFix a missed function rename in the alert-syslog example plugin
- Remove outdated docsRemove out-dated docs import, and just reference the proper docs repo now.
- Fix webserver stallFix a bug where the webserver could sometimes stall on very small function endpoints.
- Add regex to the devices view-by-time endpointAdd regex filtering after time filtering to the devices view by time
Download && Tutorial
Copyright (C) 2017





