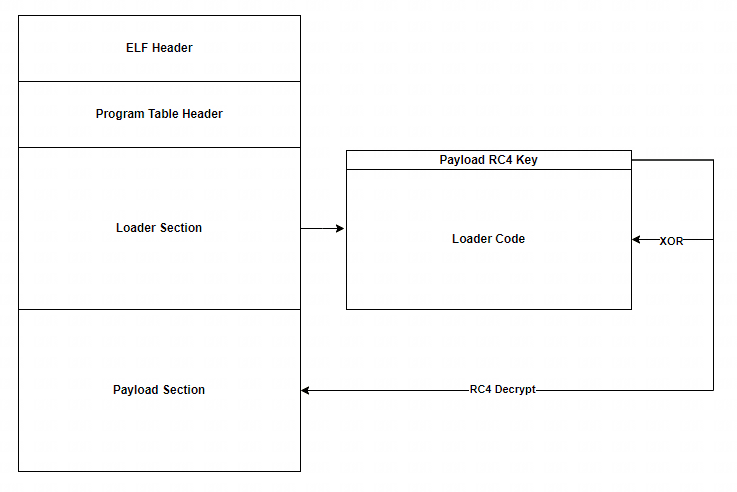
The Loader section uses RC4 to decrypt the Payload.
In a recent analysis, XLab’s Cyber Threat Insight Analysis (CTIA) System uncovered the abuse of the Kiteshield packer by various cyber threat actors targeting Linux environments. Over the past month, XLab detected a batch of suspicious ELF files with low detection rates on VirusTotal (VT) and remarkably similar characteristics. Despite the complexity and excitement of reverse-engineering these files, the investigation revealed that the low detection rates were due to the sophisticated Kiteshield packing method. This packer is now being exploited by advanced persistent threat (APT) groups like Winnti, cybercrime organizations like DarkMosquito, and even less sophisticated attackers, known as script kiddies.
Kiteshield, an open-source packer for Executable and Linkable Format (ELF) binaries, is gaining traction among threat actors due to its sophisticated evasion capabilities. By incorporating multiple layers of encryption, anti-debugging techniques, and string obfuscation, Kiteshield effectively conceals the malicious nature of packed binaries, making analysis and detection a challenging task for security researchers and antivirus software.

XLab’s analysis revealed that Kiteshield-packed ELF files contain two main segments: the Loader section and the Payload section. The Loader section uses RC4 to decrypt the Payload, with an initial RC4 key located between the end of the Program Table Header and the Entry Point. This key is XORed with the loader code to ensure integrity, followed by RC4 decryption to map the decrypted payload into memory.
Kiteshield employs several anti-debugging techniques:
- antidebug_proc_check_traced: Checks
/proc/<pid>/statusfor the presence of theTracerPidfield. - antidebug_prctl_set_nondumpable: Sets the process’s dumpable flag to 0, preventing
ptracefrom attaching or dumping. - antidebug_rlimit_set_zero_core: Sets environment variables
LD_PRELOAD,LD_AUDIT, andLD_DEBUGto empty values. - antidebug_rlimit_set_zero_core: Sets the
RLIMIT_CORE(maximum core dump size) to 0 usingsetrlimit.
Additionally, Kiteshield uses single-byte XOR encryption for string obfuscation, with the key hardcoded as 0x83. This obfuscation hinders static analysis and makes detection challenging.
While initially associated with less sophisticated actors, XLab’s analysis reveals that Kiteshield has been adopted by high-profile threat groups such as the cyberespionage group Winnti and the cybercrime group DarkMosquito. This suggests that Kiteshield is rapidly becoming a preferred tool across the threat landscape, enabling both state-sponsored actors and financially motivated cybercriminals to evade detection and maintain persistence within compromised systems.
The versatility of Kiteshield poses a significant challenge for defenders. The packer’s multi-layered defense mechanisms, including RC4 and XOR encryption, coupled with anti-debugging techniques, render static analysis largely ineffective. Additionally, its dynamic decryption at runtime further complicates the detection process.