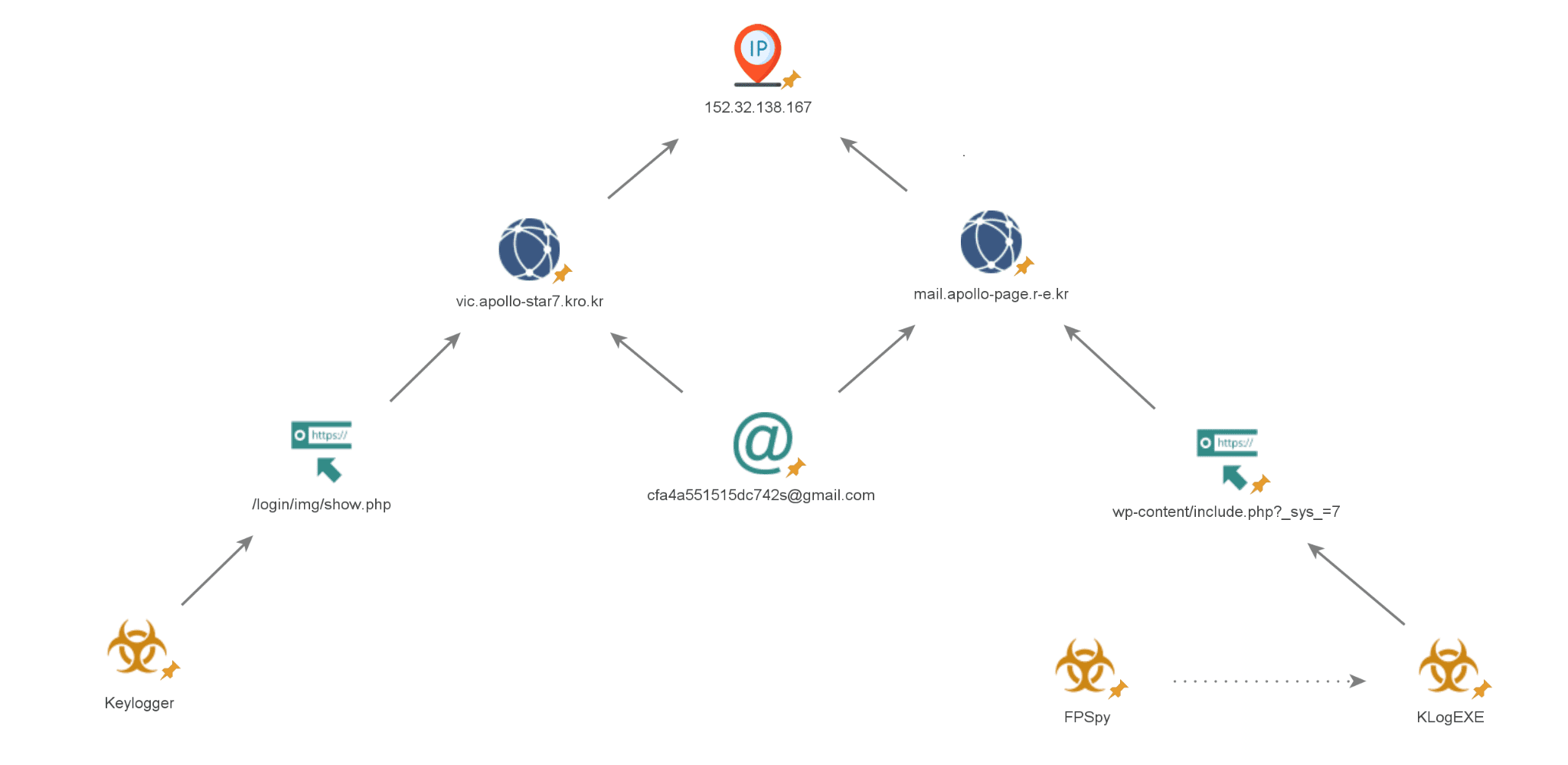
Infrastructure layout showing the connection between the malware. | Image: Unit 42
In an in-depth analysis conducted by Unit 42 researchers, two new malware samples have been linked to the notorious North Korean Advanced Persistent Threat (APT) group, Sparkling Pisces, also known as Kimsuky. The discovery of an undocumented keylogger named KLogEXE and a variant of a backdoor dubbed FPSpy demonstrates the group’s ever-expanding toolkit and evolving capabilities. These findings provide further insight into the ongoing cyber-espionage activities carried out by Sparkling Pisces, targeting critical sectors in South Korea, Japan, and beyond.
Sparkling Pisces, widely recognized for its sophisticated spear-phishing campaigns and cyber espionage operations, has been active for over a decade. The group gained notoriety for its 2014 attack on Korea Hydro and Nuclear Power (KHNP), and has since expanded its operations to target government agencies, research institutions, and even organizations in Western countries.
Often referred to as “the king of spear phishing,” Sparkling Pisces employs highly tailored attacks to deceive targets into downloading malicious payloads. In recent campaigns, the group has disguised itself as legitimate companies, using valid certificates to sign malware and evade detection. The discovery of KLogEXE and FPSpy signals a new chapter in the group’s offensive strategy.
KLogEXE, the first piece of malware identified in this analysis, functions as a stealthy keylogger designed to capture sensitive data from compromised systems. Written in C++, KLogEXE monitors the victim’s keyboard inputs and mouse clicks, collecting critical information that is then stored in an .ini file. Once the file reaches a certain size, KLogEXE sends the stolen data to Sparkling Pisces’s command-and-control (C2) server via HTTP.
What makes KLogEXE particularly dangerous is its ability to bypass static detection methods by using leaked code from HackingTeam to obfuscate API calls. By hiding within the system’s processes and using a legitimate-looking executable, KLogEXE is able to quietly monitor and exfiltrate data without raising alarms. Its communication with the C2 server mimics legitimate web traffic, further complicating detection.
The second malware sample, FPSpy, is an advanced backdoor that builds on Sparkling Pisces’s previous malware campaigns. Believed to be a variant of the group’s earlier KGHSpy malware, FPSpy offers a range of functionalities beyond keylogging. These capabilities include data collection, executing arbitrary commands, and downloading additional encrypted modules.
FPSpy operates as a DLL named sys.dll, which is loaded and executed through a custom loader. Once installed on the victim’s system, it stores system information in a file named Sysinfo_<date>.txt, logs detailed configuration data, and uploads this information to the C2 server. The backdoor also works in a multithreading model, allowing it to carry out multiple tasks simultaneously—one thread dedicated to downloading new modules, and another to uploading stolen data.
One of FPSpy’s most concerning features is its ability to execute PowerShell commands to enumerate the infected system’s drives and directories. This allows Sparkling Pisces to gather a comprehensive overview of the victim’s environment, making it easier to identify high-value targets and conduct further exploitation.
Unit 42 researchers uncovered significant infrastructure overlaps between KLogEXE and FPSpy, suggesting that both malware samples are part of a coordinated campaign. Both tools share the same C2 infrastructure, and their codebases exhibit striking similarities, including the use of hard-coded HTTP packet structures and headers. This connection reinforces the idea that Sparkling Pisces continues to develop and refine its malware arsenal to maintain an edge in its cyber-espionage operations.
The group’s infrastructure is also notable for its complexity and adaptability. By leveraging overlapping domains, registrant emails, and IP addresses, Sparkling Pisces can pivot between different malware strains and campaigns with ease, making it difficult for security teams to track their activities.
Related Posts:
- North Korean Hackers Gleaming Pisces Poisoned Python Packages Target Linux & macOS
- Linux Malware DISGOMOJI Targets Indian Officials
- UNC2970’s Backdoor Deployed via Trojanized PDF Reader Targets Critical Infrastructure
- Ransomware Cyber Attacks Spike to Over 1.2 mn per Month