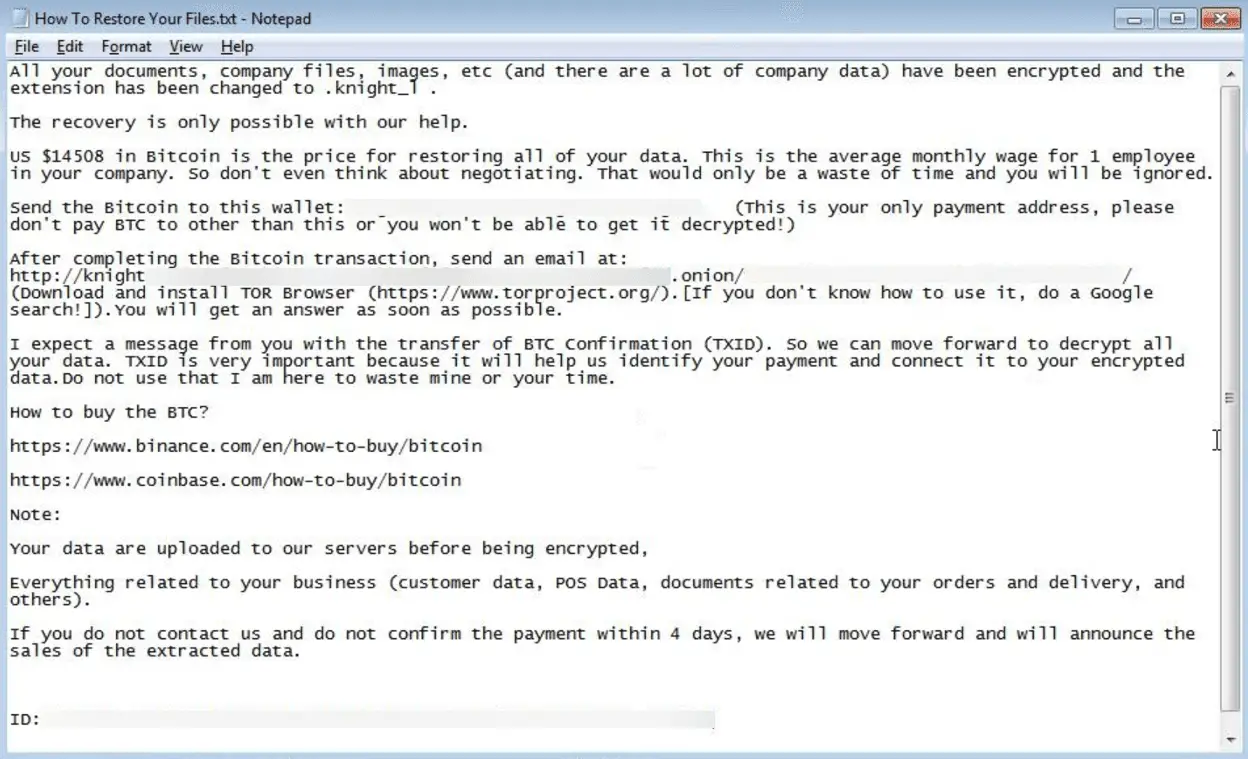
Ransom note dropped by the Knight ransomware | Image Credit: FortiGuard Labs
In August 2023, a new cyber threat named “Knight” made its mark in the world of ransomware. Spearheaded by a malicious group, Knight employs double extortion strategies, where victims’ files are encrypted, and their data is simultaneously stolen for extortion.
Knight is believed to have evolved from its predecessor, “Cyclops,” which had the capability to infect Windows, Linux, and Mac OS. While FortiGuard Labs’ recent analysis has identified only a Windows variant of Knight, other OS versions are anticipated given its lineage.
Italian institutions became early targets. CERT Italy, in a September advisory, highlighted Knight’s phishing onslaught, a sentiment echoed by security researcher @felixw3000 in August. Furthermore, the malware siblings Remcos and Qakbot have been identified as facilitators in delivering Knight to compromised systems.
A stark indicator of the group’s audacity is its widespread attacks on the retail and healthcare sectors. From hospitals to dental clinics, the ransomware showed no remorse, endangering countless individuals requiring medical attention. Geographically, the US emerged as the primary victim, leading the count by a substantial margin.
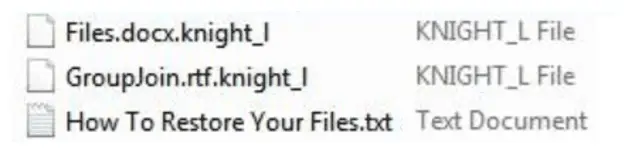
By October 20, 2023, the most recent victim post by the Knight group was dated October 18. Once Knight infiltrates, the compromised files are tagged with the “.knight_l” extension, and a daunting note titled “How To Restore Your Files.txt” is dropped.

Targeting large-scale enterprises means the demanded ransom is steep. But intriguingly, at the time of FortiGuard’s analysis, the Bitcoin wallet mentioned in the ransom note remained untouched.
Further probing reveals Knight’s operations aren’t restricted to a single platform. They maintain a TOR site, both as a medium for victim communication and to display a rogues’ gallery of their conquests. An auxiliary TOR site is dedicated to leaking stolen data, and Knight hasn’t shied away from leveraging mainstream file-sharing platforms like Mega, Gofile, and UploadNow for their operations.
In summary, the rise of the Knight ransomware group underscores the evolving, unpredictable landscape of cyber threats and emphasizes the importance of robust cybersecurity practices.