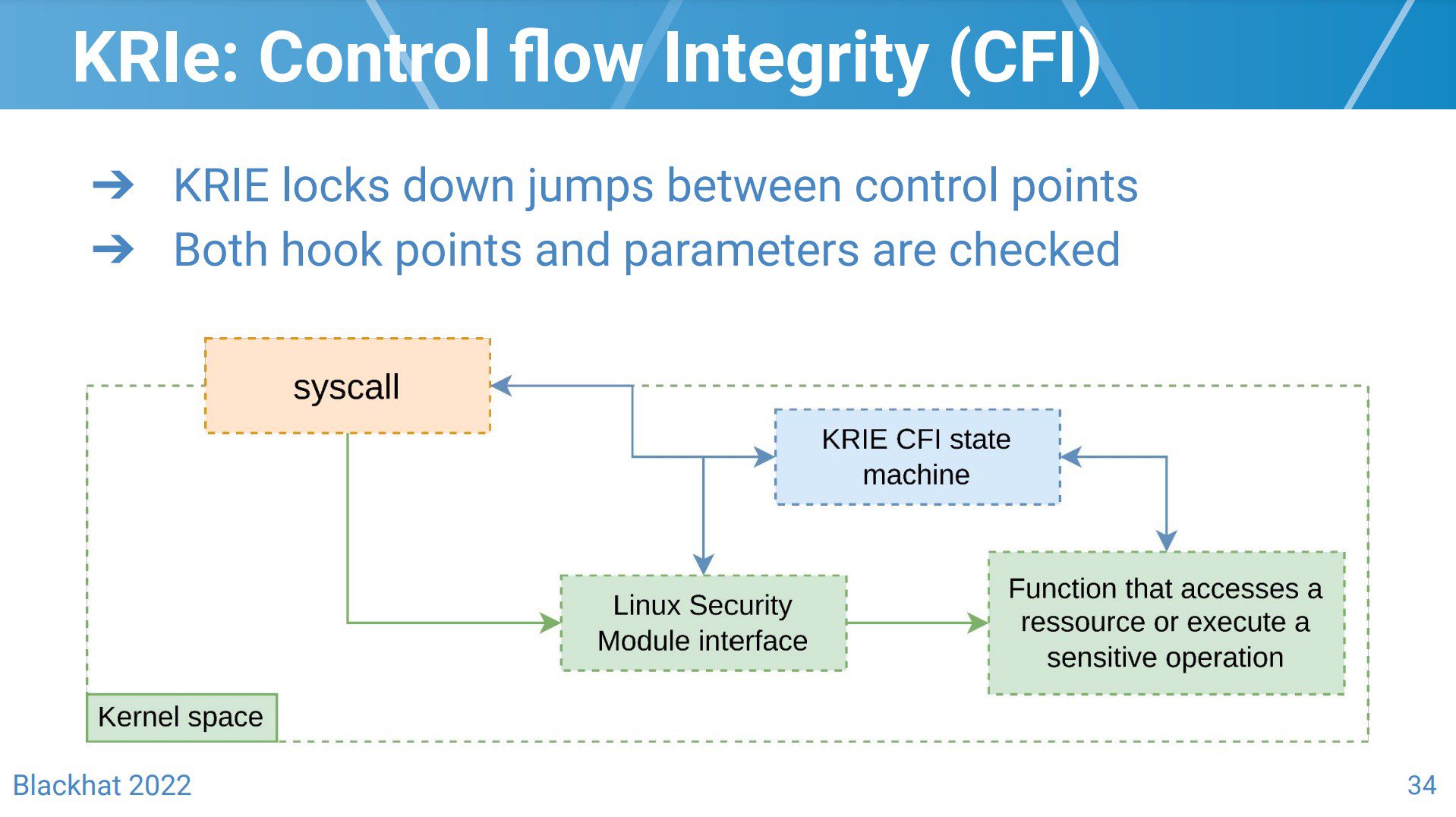
KRIe
KRIe is a research project that aims to detect Linux Kernel exploits with eBPF. KRIe is far from being a bulletproof strategy: from eBPF-related limitations to post exploitation detections that might rely on a compromised kernel to emit security events, it is clear that a motivated attacker will eventually be able to bypass it. That being said, the goal of the project is to make attackers’ lives harder and ultimately prevent out-of-the-box exploits from working on a vulnerable kernel.

KRIe has been developed using CO-RE (Compile Once – Run Everywhere) so that it is compatible with a large range of kernel versions. If your kernel doesn’t export its BTF debug information, KRIe will try to download it automatically from BTFHub. If your kernel isn’t available on BTFHub, but you have been able to manually generate your kernel’s BTF data, you can provide it in the configuration file.
System requirements
This project was developed on Ubuntu Focal 20.04 (Linux Kernel 5.15) and has been tested on older releases down to Ubuntu Bionic 18.04 (Linux Kernel 4.15).
- golang 1.18+
- (optional) Kernel headers are expected to be installed in
lib/modules/$(uname -r), update theMakefilewith their location otherwise. - (optional) clang & llvm 14.0.6+
Optional fields are required to recompile the eBPF programs.
Install & Use
Copyright (C) 2022 Gui774ume