kubestalk: discovers Kubernetes and related infrastructure based attack surface
KubeStalk
KubeStalk is a tool to discover Kubernetes and related infrastructure-based attack surfaces from a black-box perspective. This tool is a community version of the tool used to probe for unsecured Kubernetes clusters around the internet during Project Resonance – Wave 9.
Install
git clone https://github.com/redhuntlabs/kubestalk
python3 -m pip install -r requirements.txt
Use

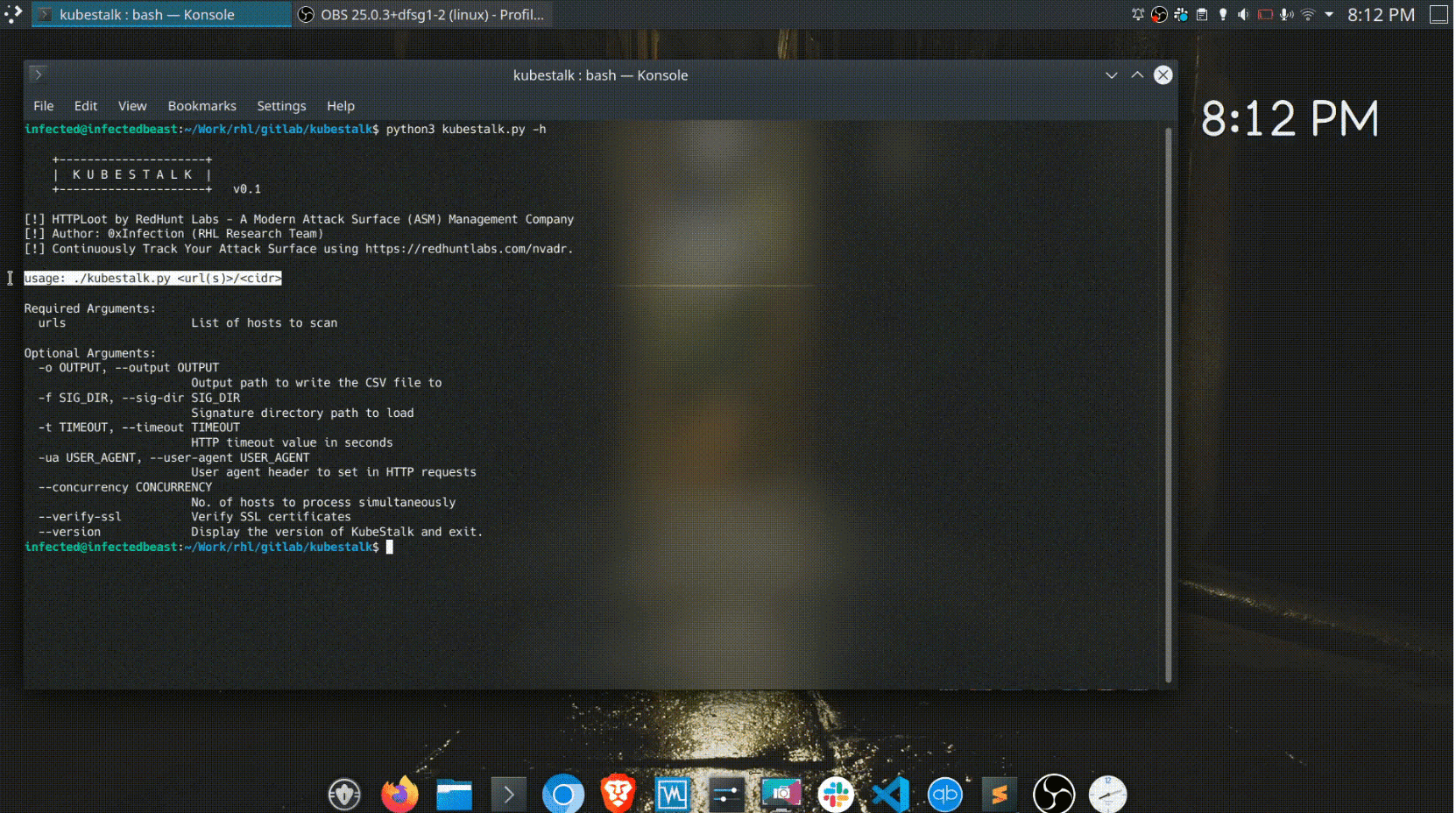
Basic Usage
To use the tool, you can pass one or more hosts to the script. All targets passed to the tool must be RFC 3986 compliant, i.e. must contain a scheme and hostname (and port if required).
Basic usage is as below:
HTTP Tuning
HTTP requests can be fine-tuned using the -t (to mention HTTP timeouts), -ua (to specify custom user agents), and the –verify-ssl (to validate SSL certificates while making requests).
Concurrency
You can control the number of hosts to scan simultaneously using the –concurrency flag. The default value is set to 5.
Output
The output is written to a CSV file and can be controlled by the –output flag.
A sample of the CSV output rendered in markdown is as below:
| host | path | issue | type | severity |
|---|---|---|---|---|
https://█.█.█.█:10250 |
/pods | Kubernetes Pod List Exposure | core-component | vulnerability/misconfiguration |
https://█.█.█.█:443 |
/api/v1/pods | Kubernetes Pod List Exposure | core-component | vulnerability/misconfiguration |
http://█.█.██.█:80 |
/ | etcd Viewer Dashboard Exposure | add-on | vulnerability/exposure |
http://██.██.█.█:80 |
/ | cAdvisor Metrics Web UI Dashboard Exposure | add-on | vulnerability/exposure |
Copyright (c) 2022 0xInfection
Source: https://github.com/redhuntlabs/