Kuiper
Digital Investigation Platform
What is Kuiper?
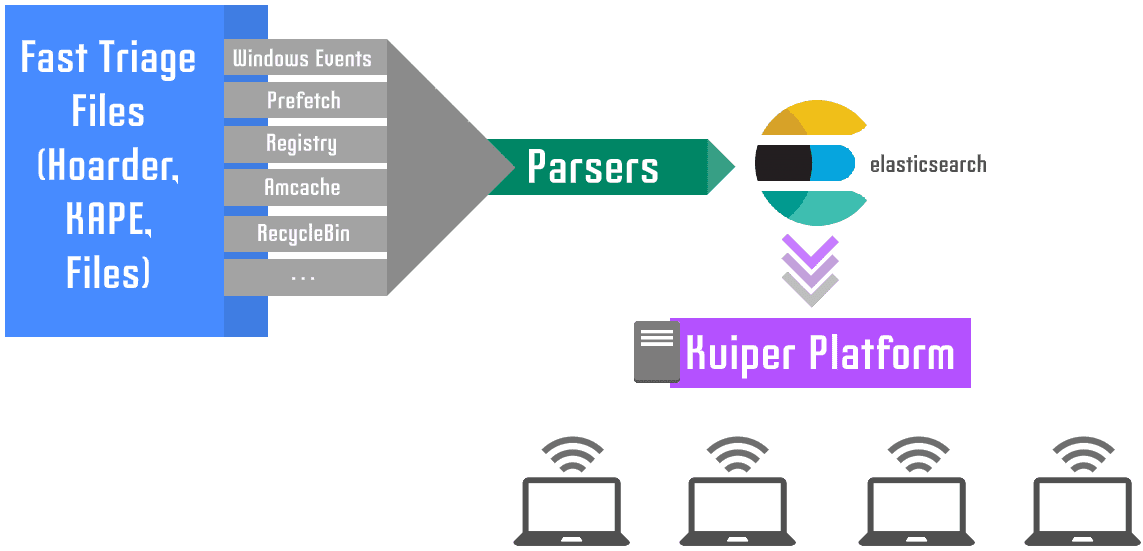
Kuiper is a digital investigation platform that provides capabilities for the investigation team and individuals to parse, search, visualize collected evidence (evidence could be collected by fast triage script like Hoarder). In addition, collaborate with other team members on the same platform by tagging artifacts and present it as a timeline, as well as setting rules for automating the detection. The main purpose of this project is to aid in streamlining digital investigation activities and allow advanced analytics capabilities with the ability to handle large amounts of data. 
Why Kuiper?
Today there are many tools used during the digital investigation process, though these tools help to identify the malicious activities and findings, as digital analysts there are some shortages that need to be optimized:
- Speeding the workflow.
- Increase accuracy.
- Reduce resource exhaustion.
With a large number of cases and a large number of team members, it becomes hard for team members collaboration, as well as events correlation and building rules to detect malicious activities. Kuiper solves these shortages.
How Kuiper Will Help Optimize the Investigation?
- Centralized server: Using a single centralized server (Kuiper) that does all the processing on the server-side reduces the needed hardware resources (CPU, RAM, Hard-disk) for the analysts’ team, no need for a powerful laptop anymore. In addition, all evidence stored in a single server instead of copying it on different machines during the investigation.
- Consistency: Depending on different parsers by team members to parse the same artifacts might provide inconsistency on the generated results, using tested and trusted parsers increase the accuracy.
- Predefined rules: Define rules on Kuiper will save a lot of time by triggering alerts on past, current, and future cases, for example, creating a rule to trigger suspicious encoded powershell commands on all parsed artifacts, or suspicious binary executed from the temp folder, within Kuiper you can define these rules and more.
- Collaboration: Browsing the parsed artifacts on the same web interface by team members boost the collaboration among them using tagging and timeline features instead of every analyst working on his/her own machine.
Use Cases
- Case creation: Create cases for the investigation and each case contains the list of machines scoped.
- Bulk evidences upload: Upload multiple files (artifacts) collected from scoped machines via Hoarder, KAPE, or files collected by any other channel.
- Evidence processing: Start parsing these artifact files concurrently for selected machines or all.
- Holistic view of evidences: Browse and search within the parsed artifacts for all machines on the opened case.
- Rules creation: Save search query as rules, these rules could be used to trigger alerts for future cases.
- Tagging and timeline: Tag suspicious/malicious records, and display the tagged records in a timeline. For records or information without records (information collected from other external sources such as FW, proxy, WAF, etc. logs) you can add a message on the timeline with the specific time.
- Parsers management: Collected files without predefined parser is not an issue anymore, you can write your own parser and add it to Kuiper and will parse these files. read more how to add parser from Add Custom Parser
Changelog v2.3.4
Fixes:
- Bug Fix: Flask and Celery Docker Images (changed gevent to version 1.2.2) Pull Request #85
- Bug Fix: fixed system health scheduler script
- Changed the Elasticsearch Java options from
ES_JAVA_OPTS=-Xms512m -Xmx512mtoES_JAVA_OPTS=-Xms4g -Xmx4g
Added:
- Net Logon parser parser Pull Request #86
- Add machine select box to alerts page Pull Request #88
Install && Use
Copyright (C) 2019 DFIRKuiper