Image Credit: SquareX
SquareX, along with its founder Vivek Ramachandran, a renowned cybersecurity expert, recently uncovered a vulnerability in Secure Web Gateway (SWG) systems, which are employed to safeguard corporate networks. It was revealed that all SWGs featured in the Gartner Magic Quadrant for SASE and SSE can be bypassed, allowing the download of malicious software onto the system without raising any alarms within the security framework.
Ramachandran has developed over 25 distinct methods to circumvent SWGs. This hacking technique is called “Last Mile Reassembly.” All the bypass methods converge on one fundamental exploit—the fact that modern browsers remain beyond the surveillance scope of SWG systems.
SWGs were created over 15 years ago, serving as SSL proxies to intercept traffic, but as cloud technologies evolved, their functionalities expanded significantly. Herein lies the core issue.
Most SWGs rely on their ability to detect application-level attacks based on network traffic before it reaches the browser. If the traffic is not identified as malicious, the SWG permits it to pass through to the user’s browser, and it is at this juncture that an attacker can launch an assault. Ramachandran asserts that these architectural vulnerabilities are so deeply ingrained that they are irreparable.
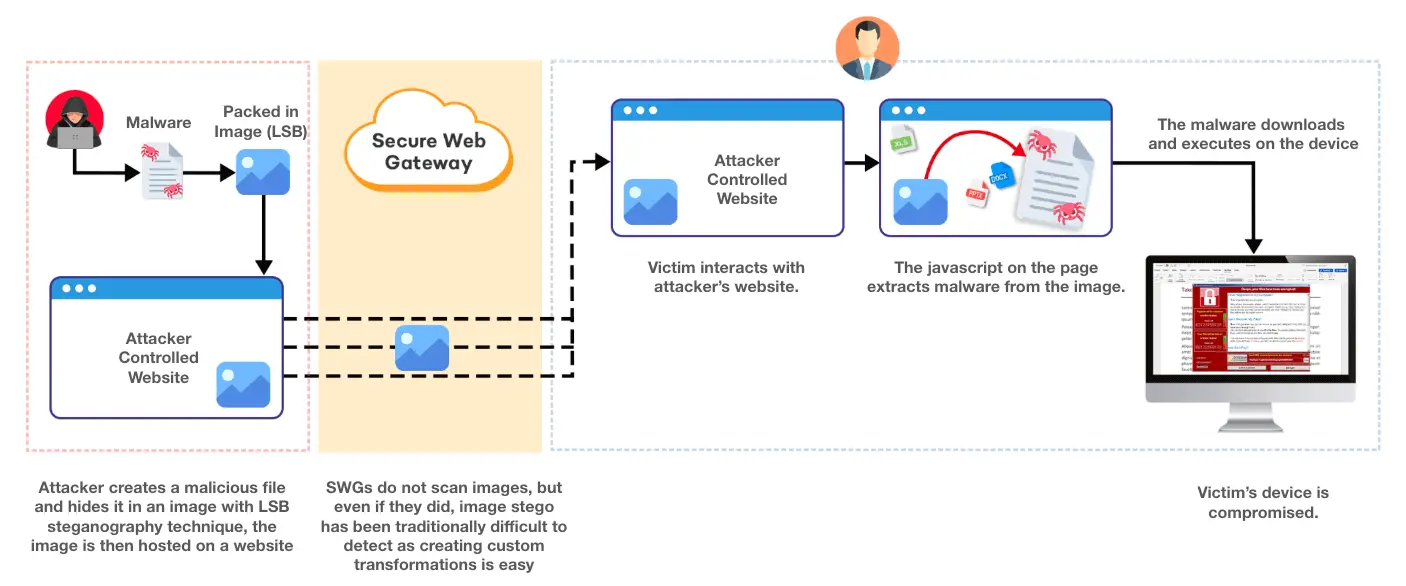
The “Last Mile Reassembly” technique exploits a simple concept: the cybercriminal has access to the computer, which, in this case, is the browser, and can “assemble” the attack at the last moment using various techniques.
For example, a hacker might fragment malicious software, use Web Assembly files, conceal malware within other files, and employ other methods to divide it into numerous small, unrecognizable parts. After fragmentation, the attacker can deliver the malicious payload and have the browser reassemble it, all without the security system’s knowledge.
One of the reasons for this vulnerability is the age of SWGs. These systems cannot cope with the modern complexities of web browsers, which possess numerous uncontrolled channels such as gRPC, webRTC, WebSocket, and WebTorrent, all of which go entirely unnoticed.
Ramachandran claims that SWG manufacturers are aware of some of the vulnerabilities that have been discovered, but fixing them would undermine their security approach. He noted that SWGs are only capable of stopping the most basic attacks. To fully detect all attacks, a complete emulation of every open browser window would be required, ensuring the gateway is aware of the application context, which is practically unfeasible.
While Ramachandran refrained from naming specific vendors to avoid casting a negative light, he strongly urges cybersecurity professionals and company leaders to recognize that the systems they rely on to protect web activity might be failing in their role.
Ramachandran also suspects that some of the attacks (as presented at Def Con) are already being actively exploited in real-world scenarios. In response, SquareX has released a free tool to test the vulnerability of existing SWG configurations.
To defend against such attacks, companies must focus on endpoint protection. It is within the browser where the attacks occur, and only there can they be detected. However, many SWG clients may lack sufficient endpoint protection, relying instead on vendor assurances that cloud solutions can fully guard against malware. The rise of “Last Mile Reassembly” attacks presents a compelling argument for re-evaluating endpoint protection strategies.
Related Posts:
- Zero-Day Vulnerability: 18 Years of Exploiting the ‘0.0.0.0’ Flaw
- CVE-2024-38063 (CVSS 9.8): 0-Click RCE Affects All Windows Systems
- CVE-2024-28986 (CVSS 9.8): SolarWinds Web Help Desk Users Must Patch Now!
- CISA & Microsoft Warn of 6 Actively Exploited Zero-Day Vulnerabilities