
The notorious Latrodectus downloader malware, known for its similarities to IcedID and its use by prominent threat actors TA577 and TA578, has undergone a significant upgrade. Netskope Threat Labs recently uncovered a new version, Latrodectus 1.4, which includes enhanced capabilities and evasion techniques.
Key Features and Updates in Latrodectus v1.4
- JavaScript File Obfuscation
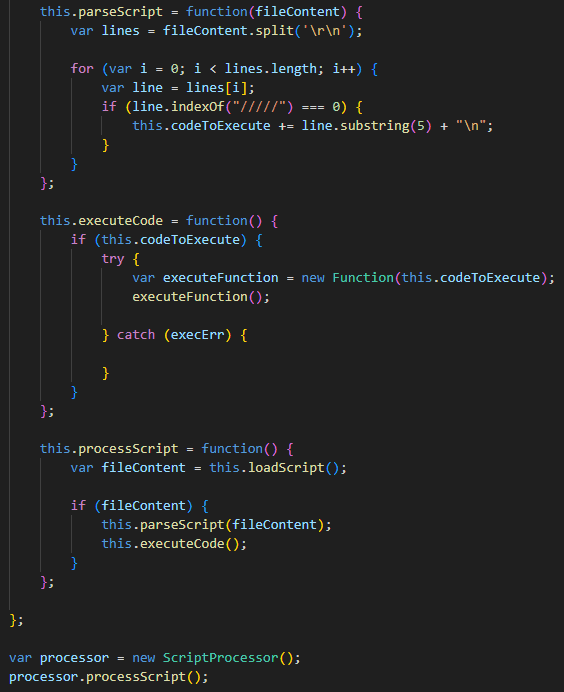
The infection chain begins with a heavily obfuscated JavaScript file, employing a technique designed to hinder analysis. The obfuscation is achieved by inserting numerous comments throughout the file, significantly increasing its size and complexity. The malicious code is hidden among these comments, specifically lines starting with the “/////” string, which are then extracted and executed as a JavaScript function. This function proceeds to download and install an MSI file from a remote server, continuing the malware’s infection process.
- MSI and DLL Payload Analysis
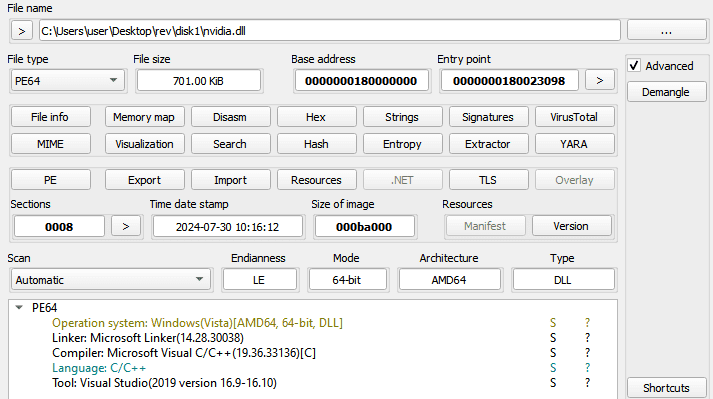
The MSI file, once installed, utilizes the Windows tool rundll32.exe to load a DLL named “nvidia.dll” and calls a function named “AnselEnableCheck.” The malicious DLL is stored within a CAB file named “disk1” inside the MSI. To further obfuscate its activities, the malware employs a crypter known as Dave, which has been associated with other notorious malware such as Emotet and BlackBasta.
The crypter decrypts and loads the final payload, which is a DLL with multiple exported functions. Interestingly, all these functions share the same Relative Virtual Address (RVA), rendering it irrelevant which one is called. The crypter’s simplicity belies its effectiveness, making it challenging for automated detection systems to unpack and analyze the payload.
- Advanced String Obfuscation
In version 1.4, Latrodectus shifts from using XOR for string obfuscation to a more robust AES256 encryption in CTR mode. The decryption process involves a hardcoded AES key and a variable Initialization Vector (IV) for each string, adding a layer of complexity to reverse-engineering efforts. This enhancement demonstrates the malware’s evolution towards more secure and sophisticated obfuscation techniques.
- Campaign ID and C2 Communication
The latest version continues to generate campaign IDs using the FNV algorithm, but with a new input string “Wiski,” resulting in the campaign ID hash 0x24e7ce9e. Communication with the C2 server involves collecting extensive system information, encrypting it using RC4, and sending it via an HTTP POST request to a new endpoint, “/test,” indicating this might be a test version of the malware. The RC4 keys used in these operations have been identified, providing crucial indicators for defenders.
- New Command Features
Latrodectus 1.4 introduces two new backdoor commands, 0x16 and 0x19:
- Command 0x16: This command downloads and executes shellcode from a specified server. The shellcode includes a base64 encoding function passed as a parameter, with its address stored in a mapped file view named “12345.”
- Command 0x19: This command receives a file name and remote location, downloads the file, and stores it in the %AppData% directory. This feature allows the malware to stealthily add new files to the system, expanding its control over the infected machine.
Conclusion
Organizations are urged to remain vigilant, particularly those targeted by TA577 and TA578, and to ensure that their security systems are equipped to detect and respond to the latest Latrodectus variants.
Related Posts
- Watch Out for Latrodectus: New Malware from Suspected IcedID Developers Targeting Businesses
- LATRODECTUS Malware Loader: Threat Poised to Replace ICEDID
- W2 Form Phishing Campaign Delivers Brute Ratel and Latrodectus Malware
- Intel OEM Private Key Leak: A Blow to UEFI Secure Boot Security