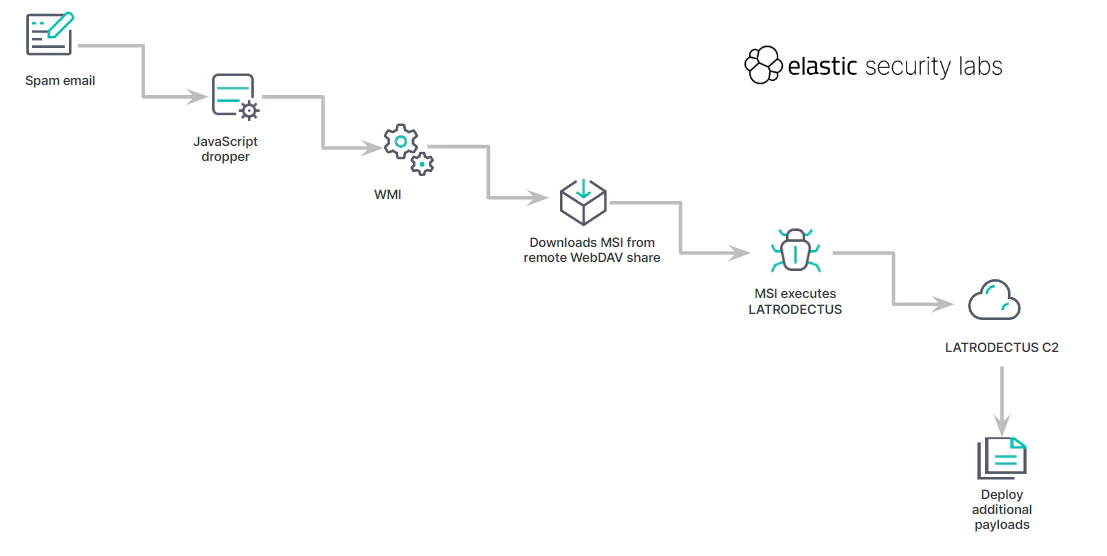
LATRODECTUS campaign overview
Cybersecurity researchers at Elastic Security Labs have issued a warning about the increasing prominence of LATRODECTUS, a malware loader exhibiting concerning similarities to the notorious ICEDID family. Their comprehensive analysis reveals a surge in LATRODECTUS-driven campaigns targeting financial institutions and individuals.
LATRODECTUS, while a relatively new malware family, has quickly become popular due to its robust capabilities. Similar to ICEDID, it features a command handler that downloads and executes encrypted payloads. Elastic Security Labs notes that the malware’s codebase is lightweight and direct, containing only 11 command handlers focused on enumeration and execution, a trend also observed in other recent malware like PIKABOT.

Starting in March 2024, Elastic Security Labs observed an uptick in email campaigns delivering LATRODECTUS. These campaigns typically involve oversized JavaScript files leveraging Windows Management Instrumentation (WMI) to invoke msiexec.exe and install a remotely hosted MSI file via WEBDAV shares. This method is part of a broader trend of simplified yet effective loaders replacing older, more complex ones.
The LATRODECTUS sample analyzed by Elastic Security Labs masquerades as a component of Bitdefender’s kernel-mode driver (TRUFOS.SYS). The malware is initially packed and requires manual or automatic unpacking for analysis. It is a DLL with four exports, all pointing to the same address, and uses straightforward algorithms for string obfuscation and import resolution.
Key Features and Anti-Analysis Techniques
- String Obfuscation: LATRODECTUS protects its strings using arithmetic and bitwise operations, continuously evolving its methods.
- Runtime API Resolution: It queries the Process Environment Block (PEB) and uses CRC32 checksums to resolve necessary DLLs and functions dynamically.
- Anti-Analysis: The malware includes several anti-analysis checks, such as monitoring for debuggers, validating the number of active processes, checking for WOW64, and verifying MAC addresses to avoid running in sandboxed environments.
LATRODECTUS employs multiple methods to ensure persistence, including creating scheduled tasks using the Windows Component Object Model (COM). It also features a self-deletion technique, complicating incident response efforts. For communication, LATRODECTUS encrypts its HTTP POST requests using base64 and RC4 with a hardcoded password, registering infected systems and receiving commands from its C2 server.
The core functionality of LATRODECTUS is driven by its command handlers, which perform tasks such as:
- Desktop File Listing: Enumerates files on the user’s desktop.
- Process Discovery: Collects running process ancestry.
- System Information Collection: Executes system enumeration commands.
- Downloading and Executing Payloads: Supports downloading and executing PE files, DLLs, and shellcode.
- Updating and Restarting: Handles malware updates and process restarts.
- ICEDID Payload Execution: Downloads and executes ICEDID components, indicating a developmental link between the two malware families.
While LATRODECTUS is still in its developmental stages, its similarity to ICEDID is striking. Both share enumeration commands, similar function structures, and methods for setting up scheduled tasks. The inclusion of a handler for executing ICEDID payloads suggests that LATRODECTUS may be positioned as a replacement for ICEDID, especially following recent disruptions in the loader landscape.