Lazarus Group Deploys New Hacking Arsenal in Targeted Cyberattacks
Security researchers at Avast have uncovered a sophisticated cyber espionage campaign linked to the infamous Lazarus Group. The attackers are targeting individuals in Asia, using fake job offers and a series of advanced hacking tools to gain access to sensitive systems. This attack highlights the increasing sophistication of such groups and their ability to develop custom malware and even zero-day exploits.

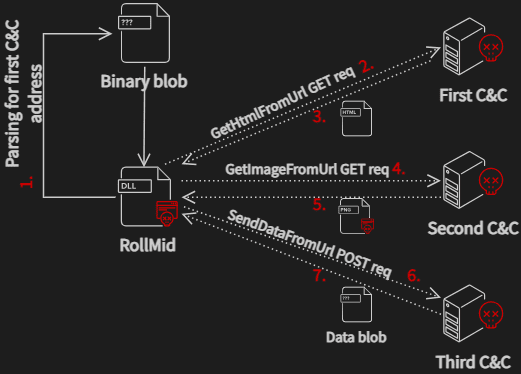
Communication with C&C servers | Image: Avast
Avast’s investigation exposed a multifaceted attack involving an initial lure through fabricated job postings. Potential victims received seemingly legitimate job offers, leading them to download and execute a malicious ISO file presented as part of the interview process. This file cleverly bypassed Windows 10’s Mark-of-the-Web (MotW) security feature, showcasing the attackers’ profound understanding of modern operating systems.
The malware initiated its intrusion by sideloading a malicious DLL through a legitimate Windows application, a method increasingly favored by attackers to evade detection. The process did not stop there; the malware further exploited a zero-day vulnerability (CVE-2024-21338) in the Windows appid.sys driver, thereby embedding itself deeply within the system through the use of the “FudModule 2.0” rootkit.
Further complicating the malware’s capabilities was the introduction of the previously undocumented Kaolin RAT. This tool not only performed standard RAT functions but also could manipulate file timestamps and dynamically load DLLs from its command and control (C&C) server. This RAT is believed to be a conduit for loading the FudModule alongside the zero-day exploit.
The Kaolin RAT can execute a variety of commands, including:
- Updating the duration of the sleep interval.
- Listing files in a folder and gathering information about available disks.
- Updating, modifying, or deleting files.
- Changing a file’s last write timestamp.
- Listing currently active processes and their associated modules.
- Creating or terminating processes.
- Executing commands using the command line.
- Updating or retrieving the internal configuration.
- Uploading a file to the C&C server.
- Connecting to the arbitrary host.
- Compressing files.
- Downloading a DLL file from C&C server and loading it in memory, potentially executing one of the following exported functions:
_DoMyFunc_DoMyFunc2_DoMyThread (executes a thread)_DoMyCommandWork
- Setting the current directory.
The attack employed an array of loaders—RollFling, RollSling, and RollMid—to manage the execution and persistence of payloads entirely in memory, further demonstrating the attackers’ skill in maintaining stealth. Each stage of the loader chain meticulously prepared the system for the next phase, ensuring a seamless transition and execution of the malicious payload without triggering security alarms.
The meticulous execution of this attack, combined with the use of custom tools and potential zero-day exploits, highlights the persistent threat posed by well-resourced groups like Lazarus. The reliance on social engineering tactics reminds us that human vigilance remains a crucial defense against ever-evolving cyber threats. Continuous updates, layered security solutions, and ongoing user awareness training are essential to mitigate risks in this complex threat landscape.





