Lazarus Group Exploits xattr with “RustyAttr” to Evade Detection
The Lazarus Group, a notorious North Korean cyber espionage collective, has added another stealthy technique to its arsenal: the abuse of xattr, or extended file attributes, in Unix-based systems like macOS and Linux. According to an analysis by security researcher Tonmoy Jitu, this method—dubbed RustyAttr—leverages macOS metadata to hide malicious payloads, evading traditional detection tools and antivirus software.
The xattr command, commonly used to store metadata such as Finder tags or quarantine flags, can also embed binary data alongside files without altering their visible contents. While useful for legitimate purposes, it provides an avenue for attackers to conceal malicious scripts. As Jitu explains: “Much like Windows Alternate Data Streams (ADS), xattr provides a mechanism for embedding metadata alongside files without altering their visible content“.
The RustyAttr trojan, reportedly developed by Lazarus Group, takes advantage of this metadata to persist on compromised systems. Embedded within extended attributes, its malicious payloads bypass traditional file-scanning tools like macOS Gatekeeper. Jitu’s analysis highlighted the trojan’s capabilities: “The RustyAttr trojan is able to fetch and execute malicious scripts directly from extended attributes, bypassing the file system’s conventional monitoring tools.”
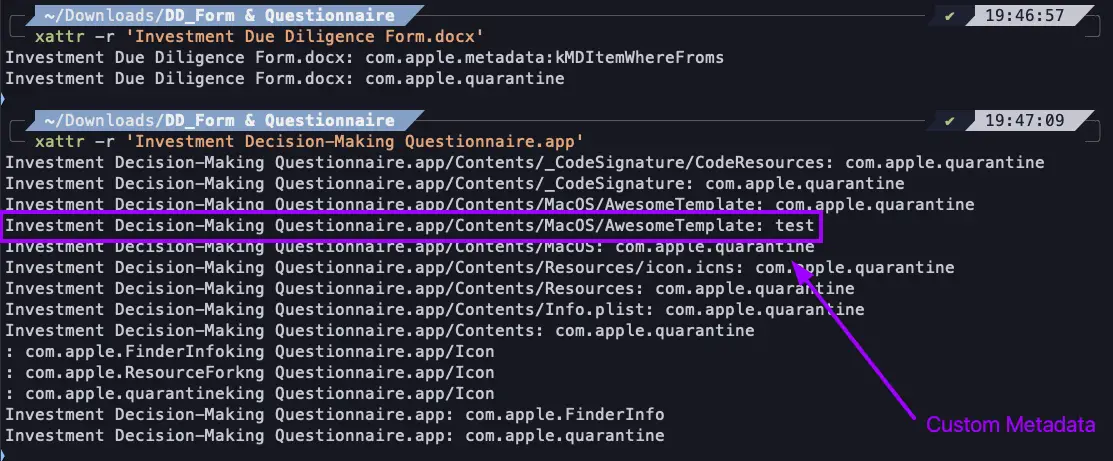
Jitu’s investigation of a malicious file, DD Form Questionnaire.zip, revealed RustyAttr’s infection chain. The trojan is hidden in metadata linked to application files, such as .app bundles. A standout discovery was the test attribute, which contained a malicious shell command to download and execute additional payloads.
The process involves:
- Embedding Commands in Metadata: Malicious shell commands are stored in attributes like com.example.hidden_data.
- Executing Hidden Payloads: These commands download decoy files (e.g., PDFs) and execute shell scripts via AppleScript. The command downloads a PDF file to a specific location… then fetches a shell script from a URL and executes it via AppleScript.
- Persistence via Leaked Certificates: Initially signed with a leaked certificate, the trojan bypassed security checks until the certificate was revoked.
The malicious infrastructure tied to RustyAttr further connects it to Lazarus Group. Jitu notes that: “The domain used in the malicious curl commands is flagged as malicious… linked to an IP address associated with known threat actor infrastructure.”
Additionally, the group employed social engineering tactics, disguising RustyAttr as legitimate PDFs or system utilities to trick users into execution.
Despite its capabilities, RustyAttr’s technique remains absent from the MITRE ATT&CK Framework, leaving defenders unprepared for such subtle attacks. Jitu emphasizes the risks: “By hiding critical data and payloads in file metadata, RustyAttr can evade detection… allowing attackers to maintain control of compromised systems for extended periods.”
Related Posts:
- RustyAttr Trojan: Lazarus Group’s New macOS Malware Evades Antivirus with Ease
- Temptation from Money: Lazarus APT extended to cryptocurrencies
- From Spear-Phishing to Zero-Day: Lazarus Group’s Latest Cyber Strategies
- North Korea’s Lazarus Group: A Persistent Threat to the Defense Sector
- Fake Crypto Game Hides Chrome Zero-Day CVE-2024-4947 Attack by Lazarus APT





