LDAP credentials collector backdoor generator

LDAP-credentials-collector-backdoor-generator
Idea About This script
Last year, during external network VAPT of a client I got inside the network using vulnerable web application. Once I was inside, I observed there is an intranet application which was accessible only if the user is having LDAP credentials.
I got the helpdesk LDAP user account and logged into the intranet (its a long story how I managed to get it), also I was having web shell on one server where I got LDAP database dump for the organization and started for hash cracking. After my best, i could get the plain text for only 60% password hashes and my target BIG FISH was still out of my reach (server admin’s LDAP account).
After that, i made my mind to try something different and simple. The server was not rootable but I was having web shell access on the intranet web portal and included my script to get visitors passwords.
How actually it works
This script generates backdoor code which log username password of an user who have passed HTTP basic auth using LDAP credentials.
If the attacker is having web shell access of the website where users are landing after successful HTTP basic authentication via LDAP account, it extracts user’s username and password from request header (Authorization).
The attacker needs to include the backdoor generated by this script on the website and script will start logging username, password of visitors.
How to use
This script generates one file which we need to upload on the target server, include the backdoor file in the webportal (which is getting used by users). Backdoor code will extract username password of the user from Authorization header and will log them in a file.
Step 1. Access script and click “start process” button
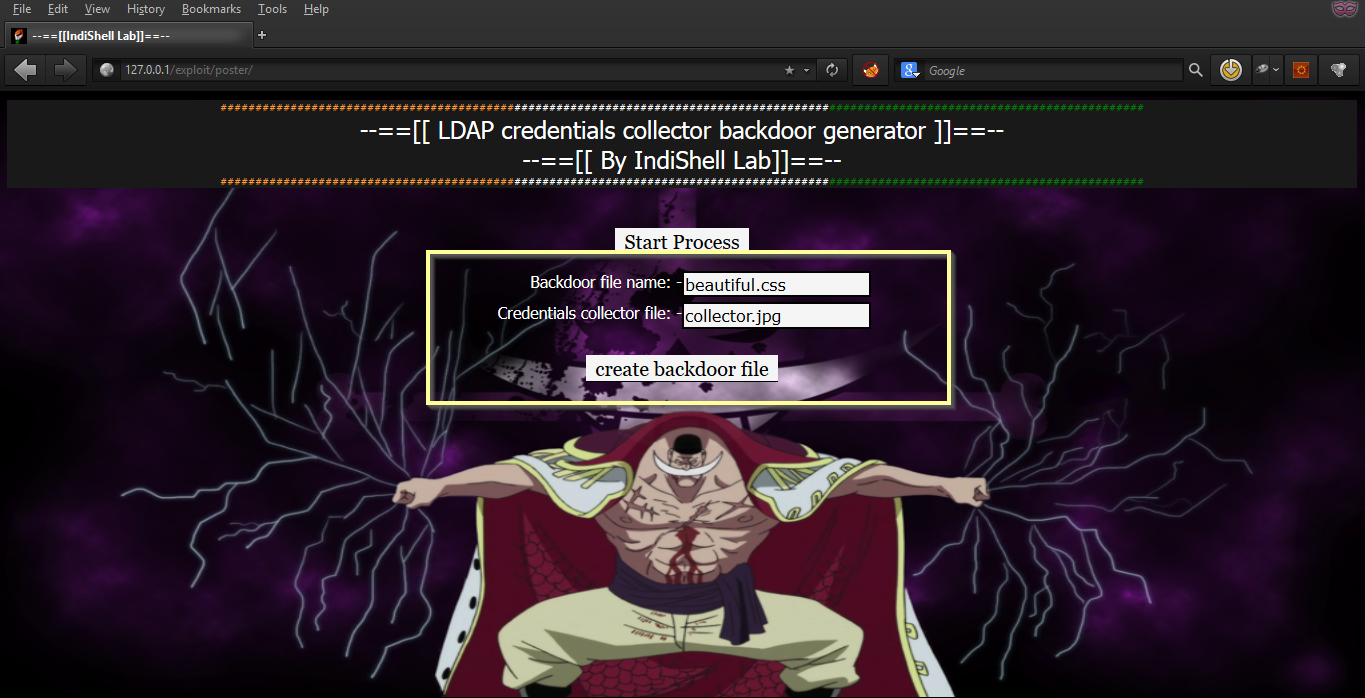
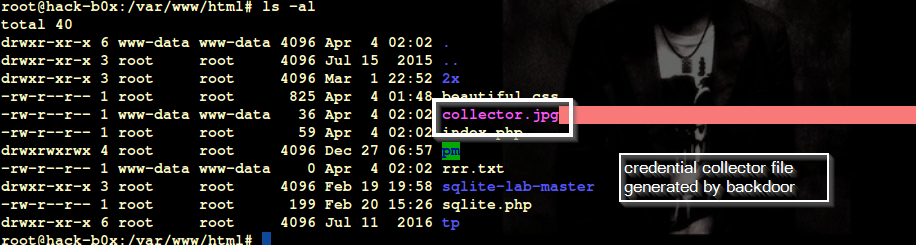
Step 2. Chose any name with which you want to generate backdoor, in my case, I am going for “beautiful.css”. Credential collector file name is the name of the file which will save credentials on the target server. Backdoor will generate this file on the target server to store the stolen credentials, an attacker just needs to download credential collector file to get stolen credenatials. In my case credentials, collector file name is “collector.jpg”
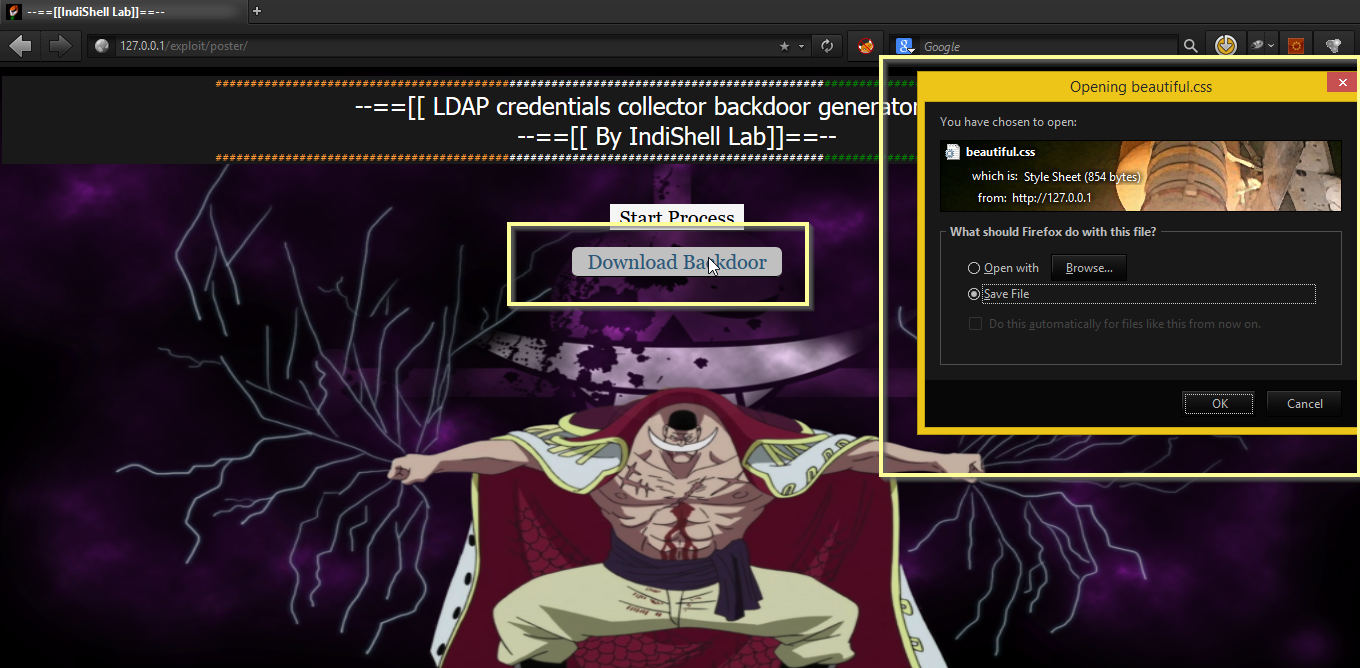
Step 3. once you click “create backdoor file” button, you will be prompted with “download backdoor” button screen, just click the button to download the backdoor.
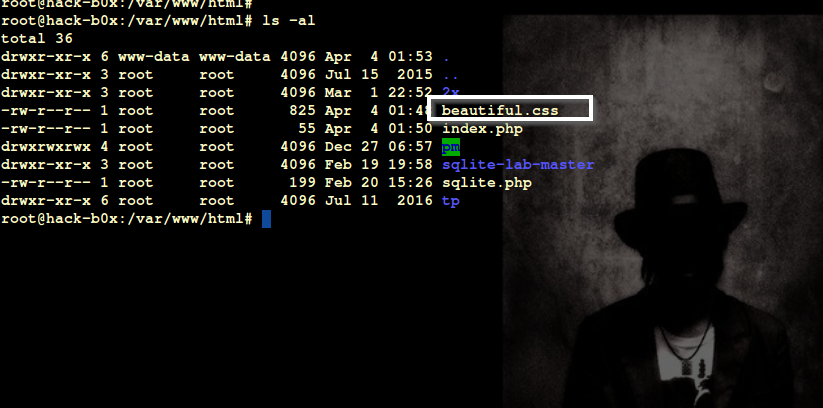
Step 4. Upload backdoor to target server
Step 5. Include backdoor file in the website file which is getting used frequently by users. code to include backdoor is
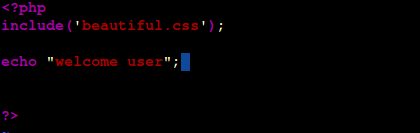
include(‘beautiful.css’);
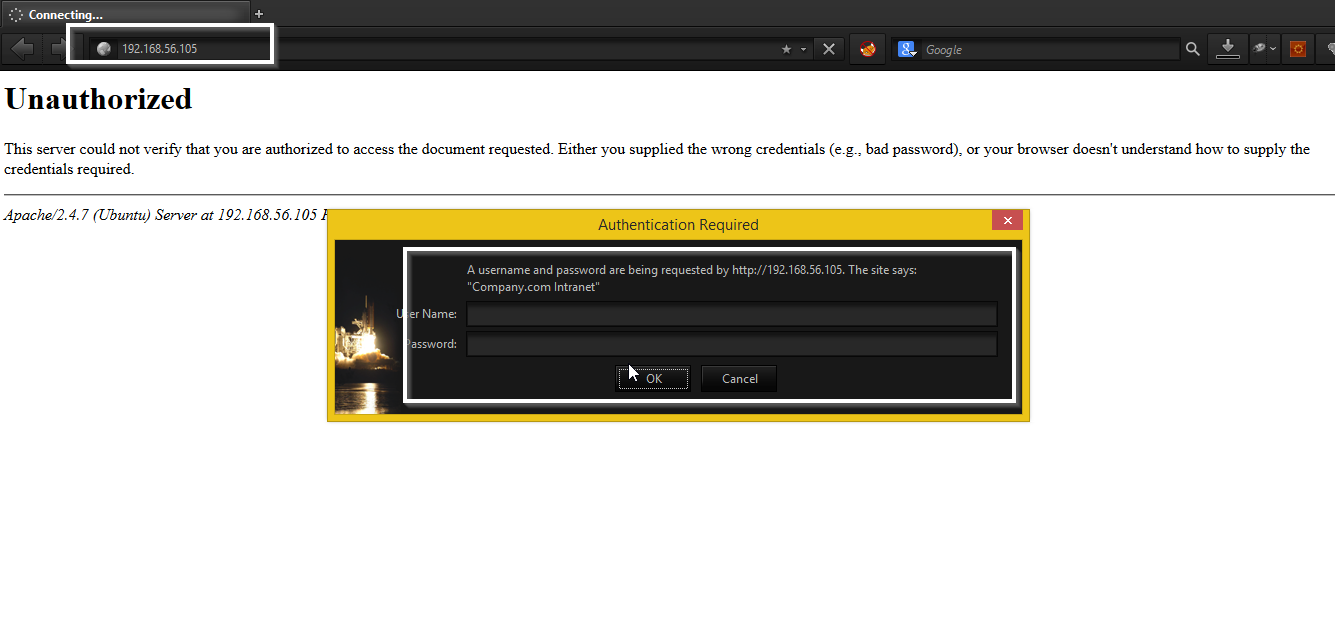
Step 6. Wait for users to log in or to visit the website having our backdoor. Let’s say one user is logging in using his LDAP account.
Step 7. As user will visit the page after successful authentication, backdoor file will generate collector.jpg file for credential storage.
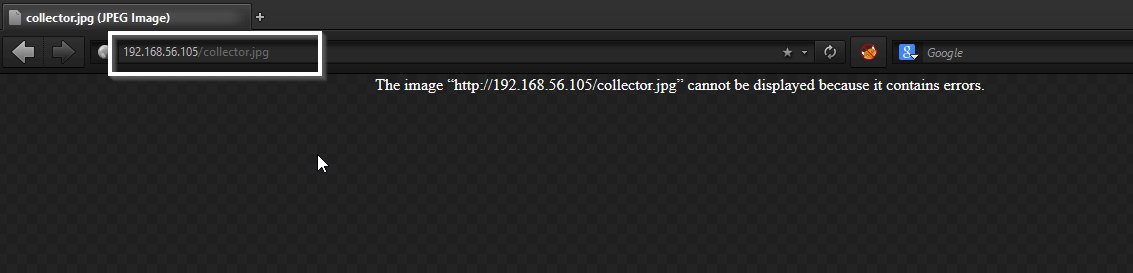
Step 8. To get stolen credentials, attacker need to download credential file (collector.jpg)
Step 9. save the file and open it in any text editor and get your credentials.