LEAKEY: checks and validates for leaked credentials
LEAKEY
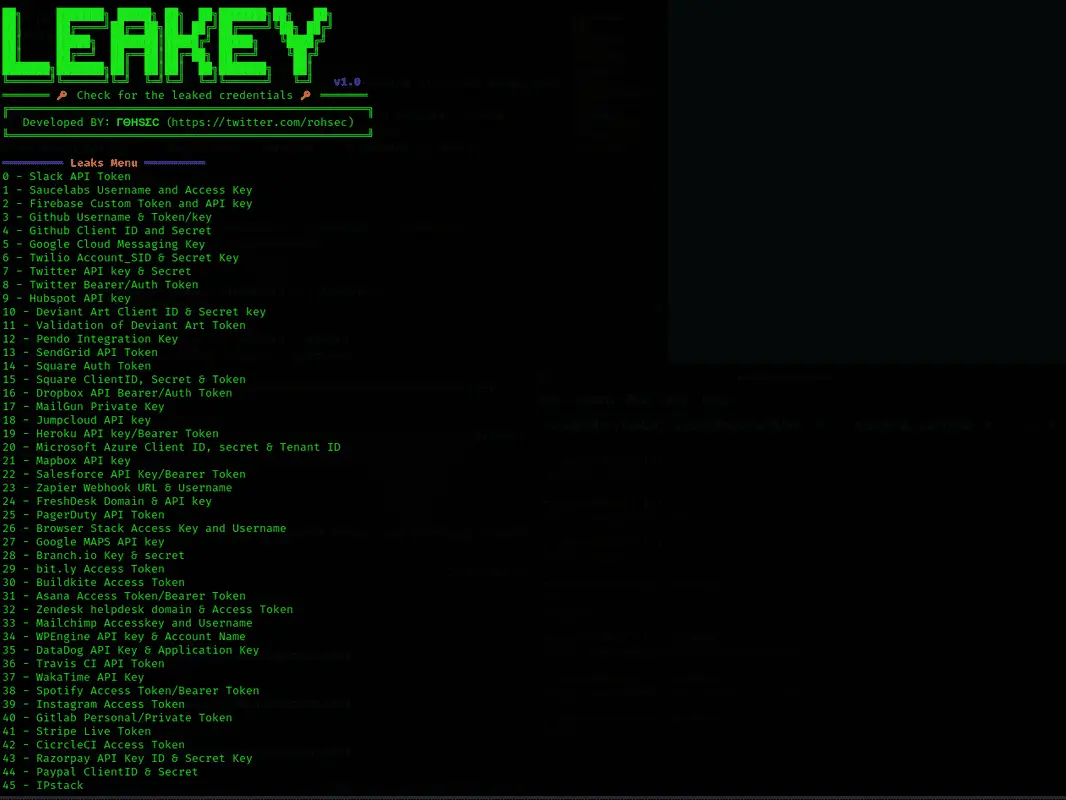
LEAKEY is a tool for validation of leaked API tokens/keys found during pentesting and Red Team Engagements.
The script is really useful for Bug Hunters in order to validate and determine the impact of leaked credentials.

LEAKEY uses a json based signature file located at ~/.leakey/signatures.json
The idea behind LEAKEY is to make it highly customizable and easy to add new services/checks once they are discovered.
LEAKEY loads the services/check list via the signature file, if you wish to add more Checks/services, simply append it to the signatures.json file.
Installation
curl https://raw.githubusercontent.com/rohsec/LEAKEY/master/install.sh -o leaky_install.sh && chmod +x leaky_install.sh && bash leaky_install.sh
Use
After running the installation command, simply run the below in your terminal
Adding Checks:
All the checks for LEAKEY are defined in the signatures.json file.
To add any new checks, simply append the signatures file at ~/.leakey/signatures.json

Source: https://github.com/rohsec/





