A recent security advisory from the LibreNMS project has revealed a severe vulnerability (CVE-2024-51092) affecting versions up to 24.9.1 of the widely-used network monitoring platform. The flaw, rated a critical 9.1 on the CVSS scale, allows authenticated attackers to execute arbitrary OS commands, potentially leading to full server takeover.
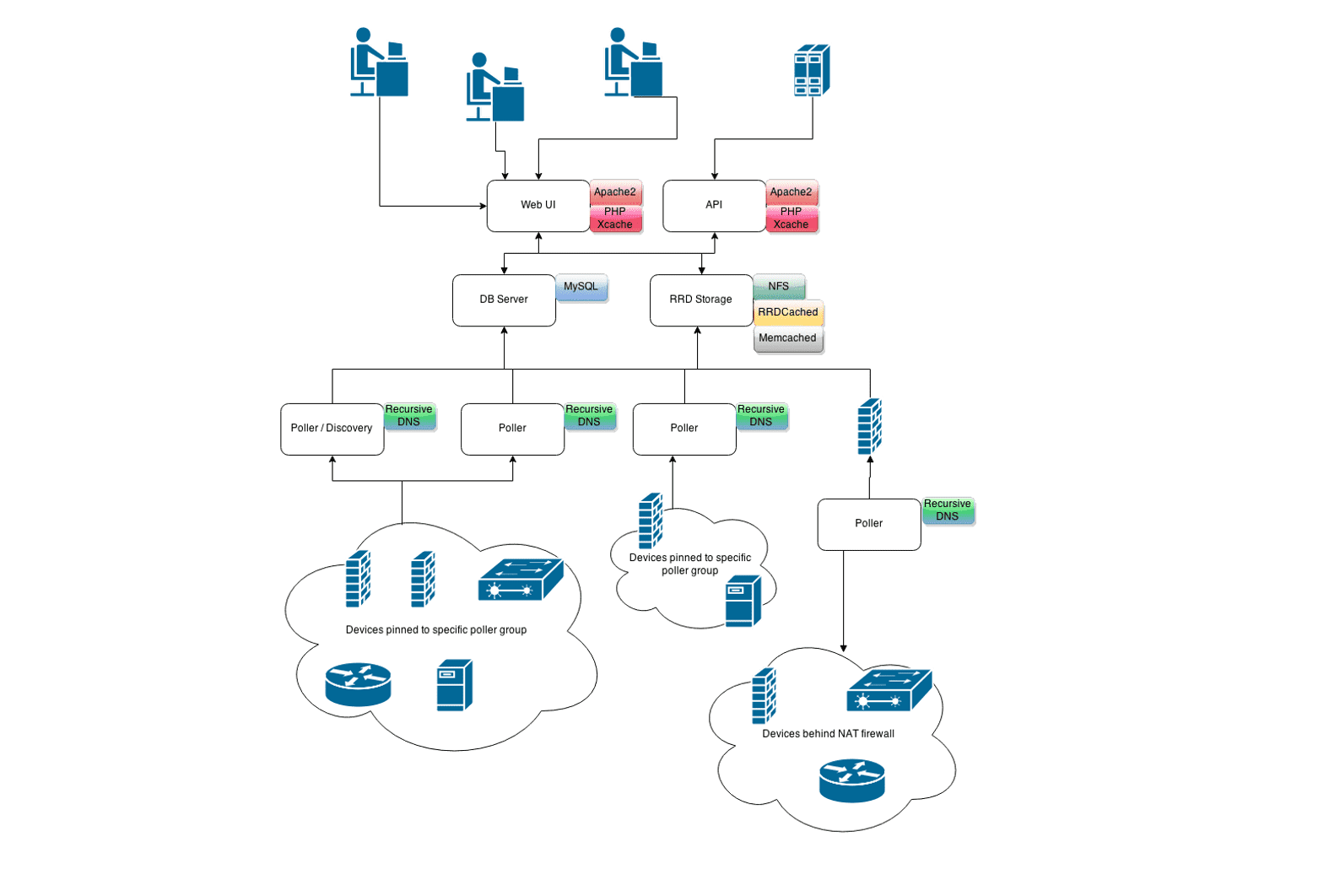
LibreNMS is a PHP/MySQL/SNMP-based network monitoring system, offering support for a variety of network hardware and operating systems. The advisory states, “An authenticated attacker can create dangerous directory names on the system and alter sensitive configuration parameters through the web portal. Those two defects combined then allow for arbitrary OS commands inside shell_exec() calls, thus achieving arbitrary code execution.”
The vulnerability stems from a combination of design flaws:
- OS Command Injection: The
AboutController.phpscript processes unsanitized inputs, enabling injection of shell commands. - Configuration Parameter Poisoning: Attackers can manipulate configuration values using the
SettingsController.phpscript to point to malicious binaries. - Arbitrary Directory Creation: Unsanitized hostnames allow attackers to create malicious directory structures.
The advisory demonstrates how an attacker can chain these issues to achieve code execution. The process involves creating a device with a malicious hostname, altering configuration parameters, and executing shell commands through the /about page.
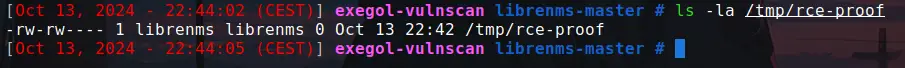
The report explains: “To summarize: if an attacker finds a valid full-path to a system binary, while that full-path also holds shell metacharacters, those characters would be interpreted by the shell_exec() call defined above and allow for arbitrary command execution.”
A provided Proof of Concept (PoC) illustrates how a base64-encoded command can exploit this vulnerability to create a file on the server.
The LibreNMS team has addressed this issue in version 24.10.0. Users are strongly urged to update their installations immediately to prevent exploitation.