ligolo: Reverse Tunneling made easy for pentesters
Ligolo: Reverse Tunneling made easy for pentesters, by pentesters
Ligolo is a simple and lightweight tool for establishing SOCKS5 or TCP tunnels from a reverse connection in complete safety (TLS certificate with the elliptical curve).
It is comparable to Meterpreter with Autoroute + Socks4a but more stable and faster.
Use case
You compromised a Windows / Linux / Mac server during your external audit. This server is located inside a LAN network and you want to establish connections to other machines on this network.
It can setup a tunnel to access the internal server’s resources.
Features
- TLS 1.3 tunnel with TLS pinning
- Multiplatforms (Windows / Linux / Mac / …)
- Multiplexing (1 TCP connection for all flows)
- SOCKS5 proxy or simple relay
How to use it?
It consists of two modules:
- localrelay
- ligolo
Localrelay is intended to be launched on the control server (the attacker server).
Ligolo is the program to run on the target computer.
For localrelay, you can leave the default options. It will listen on every interface on port 5555 and wait for connections from the ligolo (-relayserver parameter).
For ligolo, you must specify the IP address of the relay server (or your attack server) using the -relayserver ip:port parameter.
You can use the -h option for help.
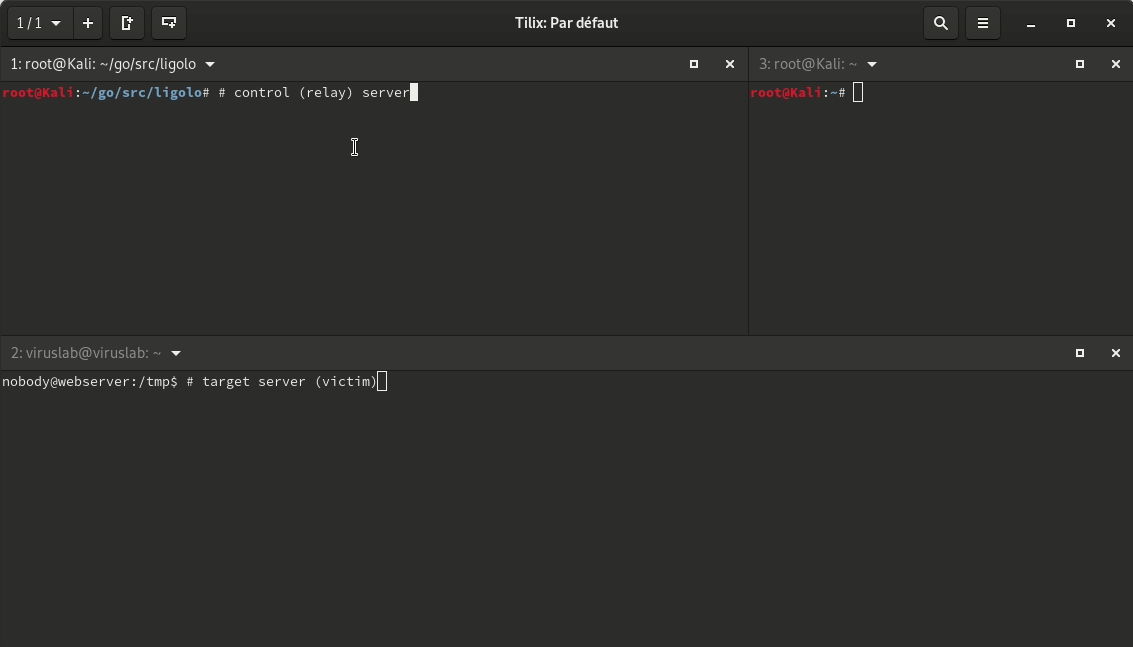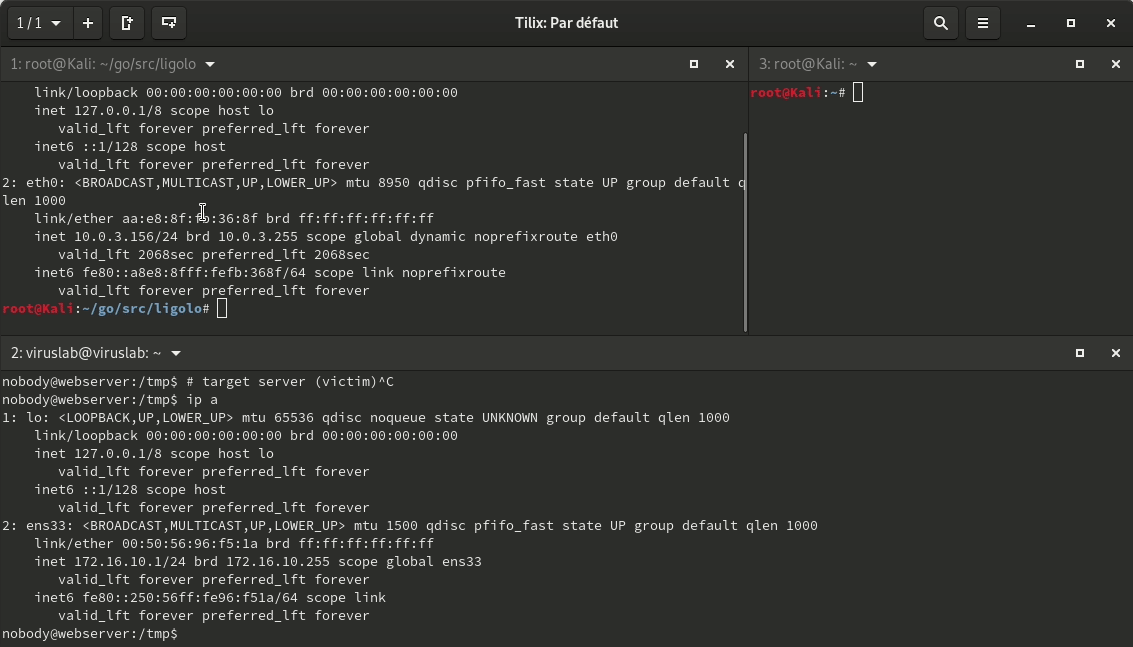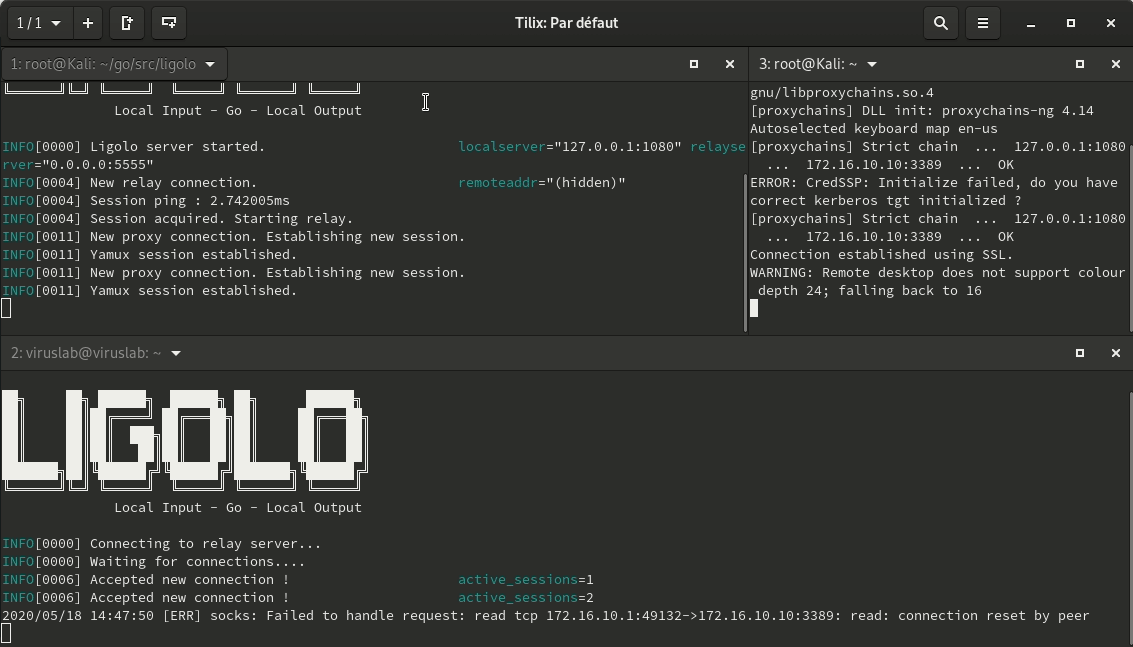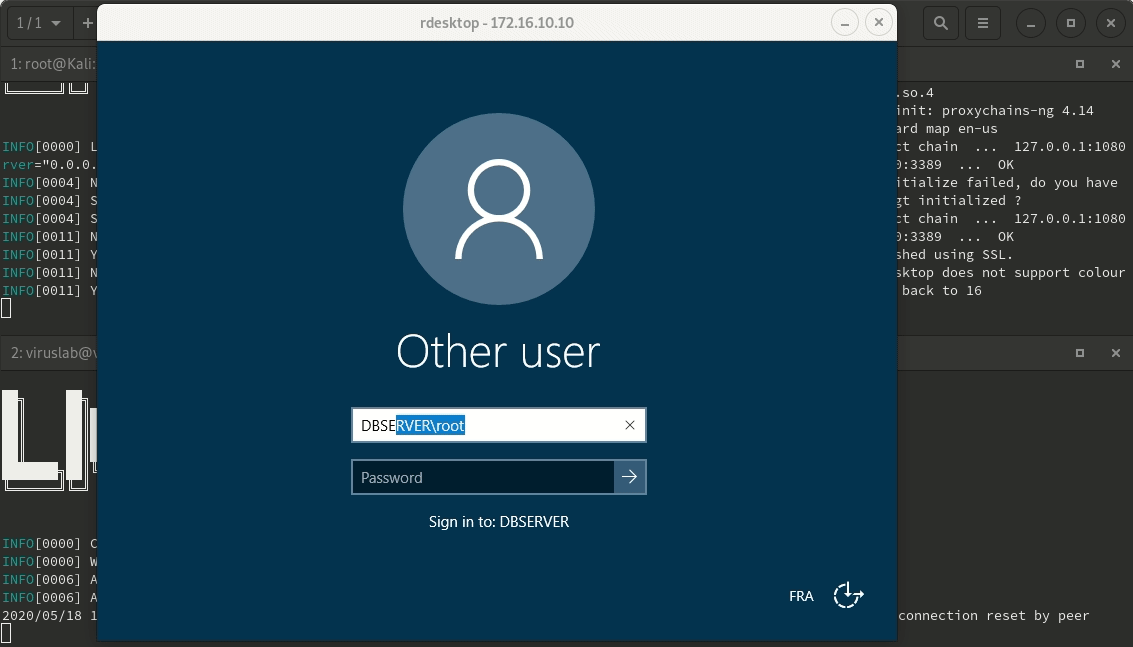
Once the connection has been established between Ligolo and LocalRelay, a SOCKS5 proxy will be set up on TCP port 1080 on the relay server (you can change the TCP address/port using the -localserver option).
After that, all you have to do is use your favorite tool (Proxychains for example), and explore the client’s LAN network.
Install
Copyright (C) 2020 sysdream





