Limon: Sandbox for Analyzing Linux Malwares
Limon – Sandbox for Analyzing Linux Malwares
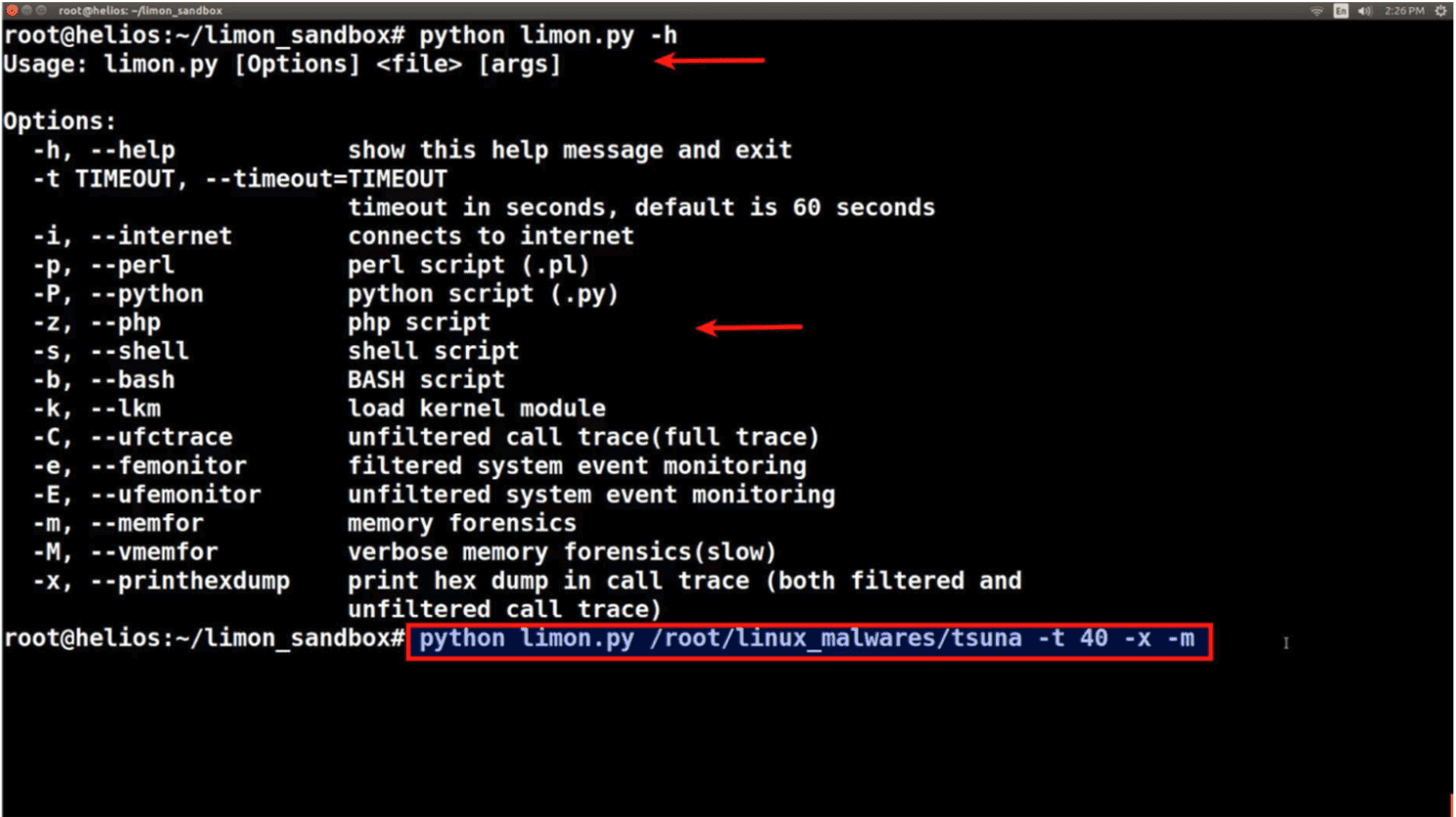
Limon is a sandbox developed as a research project written in python, which automatically collects, analyzes, and reports on the runtime indicators of Linux malware. It allows one to inspect the Linux malware before execution, during execution, and after execution (post-mortem analysis) by performing static, dynamic and memory analysis using open source tools. Limon analyzes the malware in a controlled environment, monitors its activities and its child processes to determine the nature and purpose of the malware. It determines the malware’s process activity, interaction with the file system, network, it also performs memory analysis and stores the analyzed artifacts for later analysis.
Tools used by Limon
Limon relies on various open source tools to perform static, dynamic and memory analysis which means these tools need to installed (some of these tools need to be installed on the host machine and some in the analysis machine and some in both) for Limon to work. Some of these tools come installed with default Linux installations. Below is the list of tools Limon relies on:
• YARA and YARA-python
• VirusTotal Public API
• ssdeep
• strings utility
• ldd
• readelf
• Inetsim
• Tcpdump
• strace
• Sysdig
• Volatility memory forensics framework

Installation && Tutorial
Copyright (C) 2016 Monnappa K A