Cybersecurity firm Volexity has revealed a new cyber-espionage campaign targeting Indian government entities, employing a custom-built malware dubbed DISGOMOJI. This Linux-based malware, a modified version of the open-source project discord-c2, leverages the Discord messaging platform for command and control (C2) communications, utilizing emojis as a unique communication protocol.
UTA0137’s campaign appears to be specifically designed to target Indian government entities that use a custom Linux distribution called BOSS. Volexity’s analysis suggests that this operation has been highly successful, with DISGOMOJI playing a central role in the threat actor’s toolkit. The malware is delivered via phishing campaigns using decoy documents, a strategy that aligns with the espionage objectives of UTA0137.
The campaign begins with the delivery of a UPX-packed ELF file written in Golang, disguised within a ZIP file. Upon execution, this ELF file downloads a benign lure document, DSOP.pdf, which refers to India’s Defence Service Officer Provident Fund, to distract the victim. Concurrently, the malware retrieves the DISGOMOJI payload from a remote server and deposits it in a hidden directory within the user’s home directory.
DISGOMOJI’s innovative use of Discord for C2 is noteworthy. The malware creates dedicated channels for each infected machine, formatted as sess-%s-%s, where the first %s represents the operating system, and the second %s is the victim’s username. Upon startup, the malware sends a check-in message containing details about the infected machine, such as internal IP, username, hostname, operating system, and current working directory.
To maintain persistence, DISGOMOJI employs cron jobs, adding entries to ensure it survives reboots. Additionally, it downloads and executes a script named uevent_seqnum.sh, which monitors for connected USB devices and copies files from them to a local folder for later exfiltration.
DISGOMOJI listens for commands sent via emojis in the Discord channel, processing tasks such as executing shell commands, taking screenshots, downloading and uploading files, and exfiltrating data to third-party storage services.
Recent variants of DISGOMOJI have introduced several enhancements, such as:
- Preventing duplicate processes from running.
- Dynamically retrieving Discord credentials from an attacker-controlled server, complicating efforts to disrupt the malware’s operations.
- Adding numerous bogus strings to misdirect analysts.
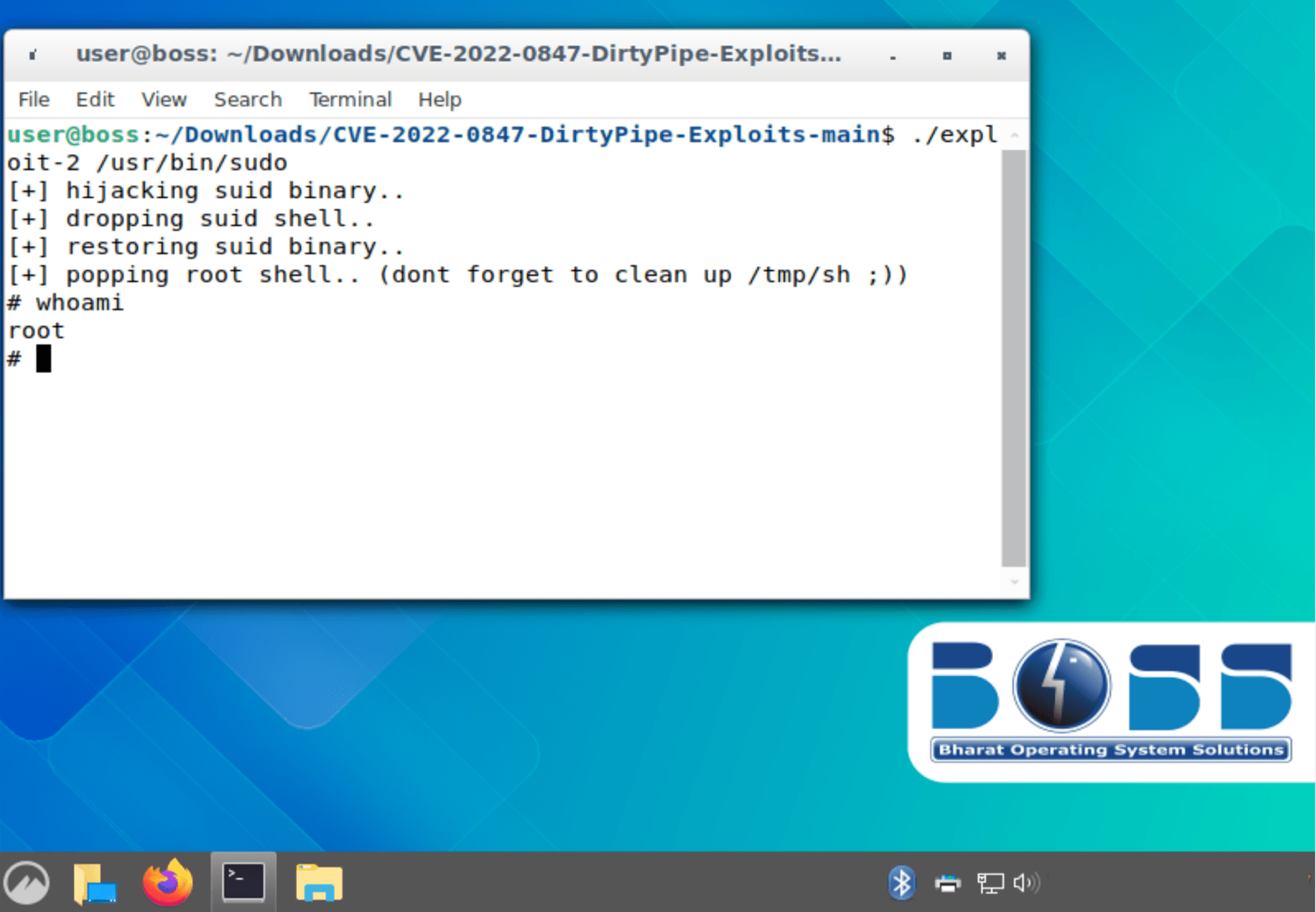
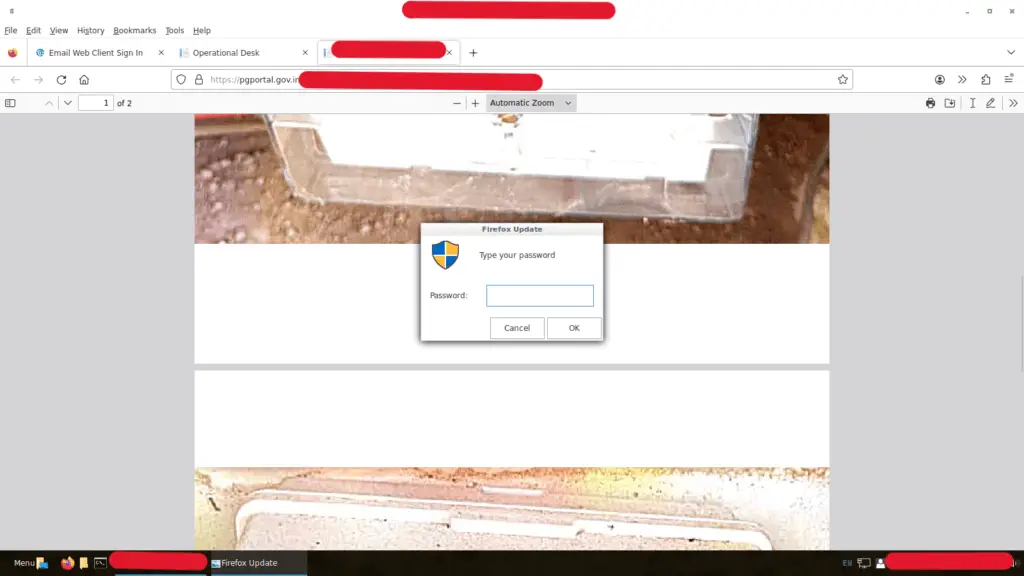
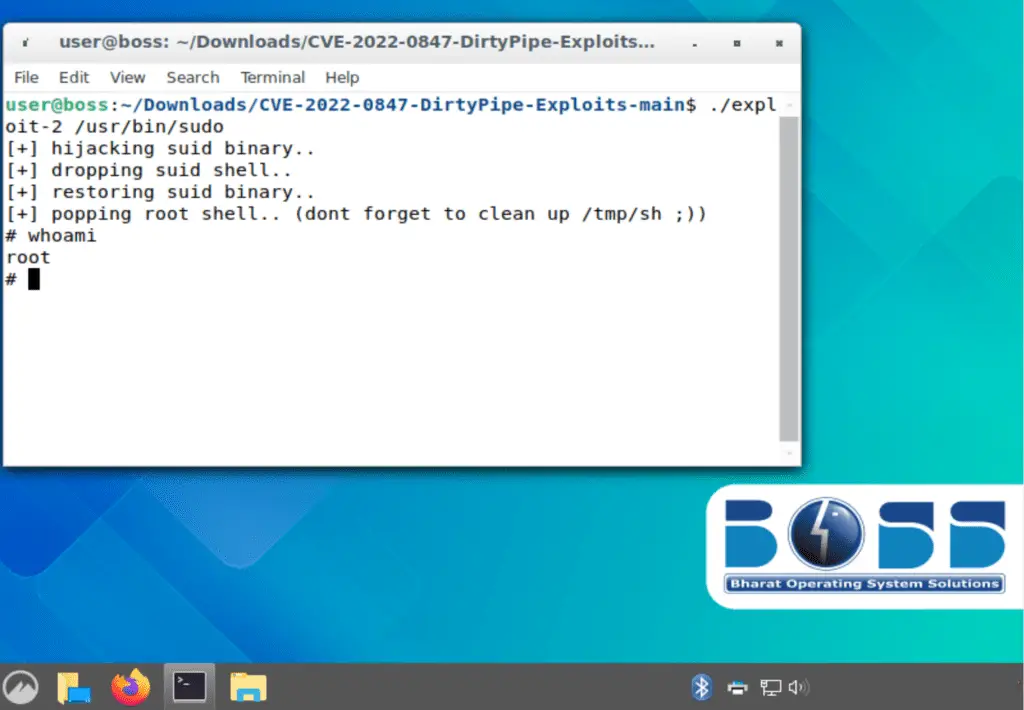
Following successful infection, UTA0137 employs various tools and techniques, including Nmap for network scanning, Chisel and Ligolo for network tunneling, and Zenity to display deceptive dialog boxes for password harvesting. The attacker also uses the DirtyPipe (CVE-2022-0847) privilege escalation exploit against vulnerable BOSS 9 systems.
Volexity attributes this campaign to a Pakistan-based threat actor with moderate confidence, based on indicators such as time zone settings, language use, and targeted entities. UTA0137’s ongoing improvements to DISGOMOJI and their strategic targeting of Indian government organizations underscore the persistent threat posed by this group.
Volexity’s detailed analysis and indicators of compromise (IoCs) provide valuable insights for defending against this advanced malware. For more information, including YARA rules and IoCs, visit Volexity’s GitHub page.