lockc
lockc is open source software for providing MAC (Mandatory Access Control) type of security audit for container workloads.
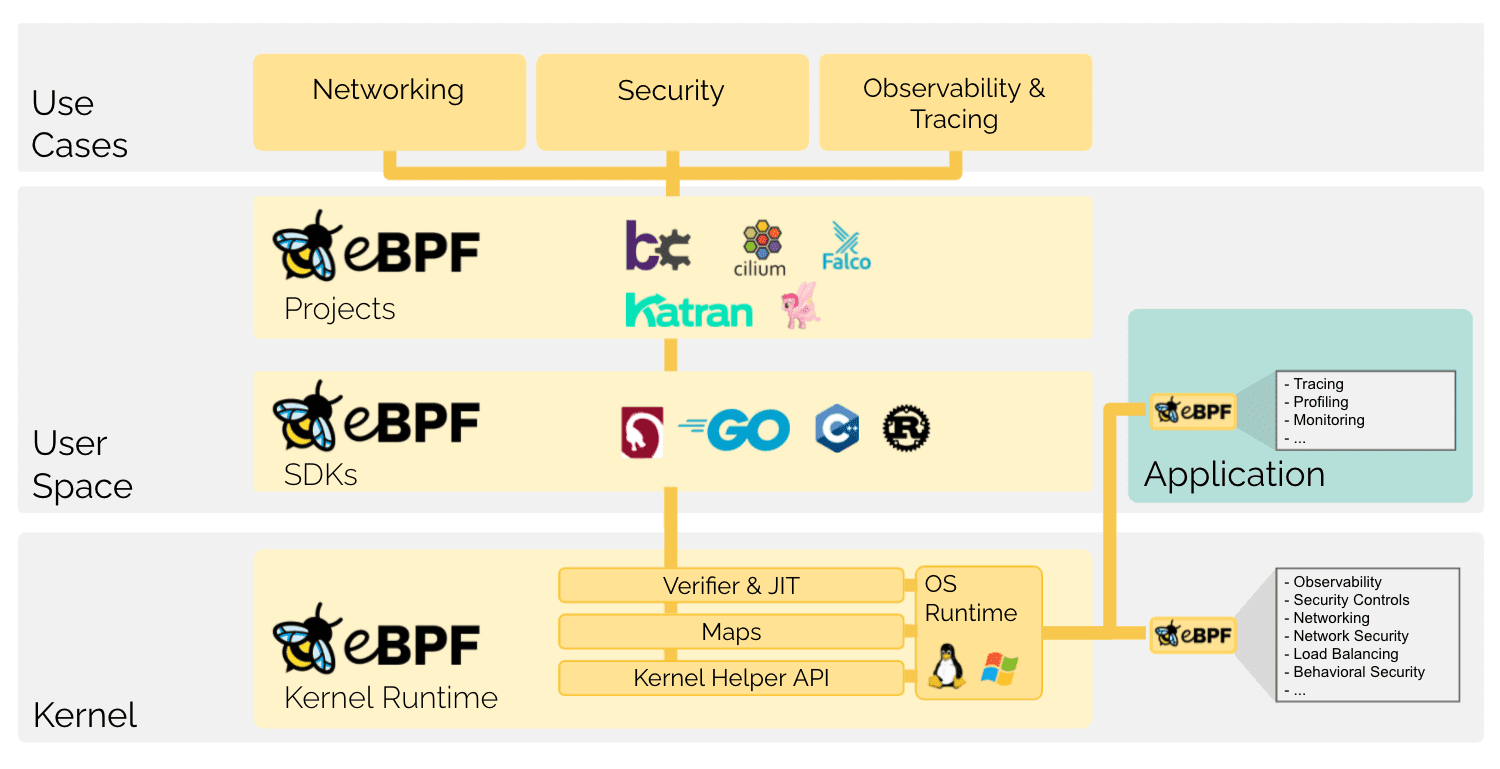
The main technology behind lockc is eBPF – to be more precise, its ability to attach to LSM hooks.
Architecture
The project consists of 3 parts:
- the set of BPF programs (written in C)
- programs for monitoring processes, which detects whether new processes are running inside any container, which means applying policies to them
- programs attached to particular LSM hooks, which allow or deny actions based on the policy applied to the container (currently all containers have the baseline policy applied, the mechanism of differentiating between policies per container/pod is yet to be implemented)
- lockcd – the userspace program (written in Rust)
- loads the BPF programs into the kernel pins them in BPFFS
- in the future, it’s going to serve as the configuration manager and log collector
- lockc-runc-wrapper – a wrapper for runc which registers new containers and determines which policy should be applied to a container
Functions
- add_container
- add_process
- check_bpf_lsm_enabled Checks whether BPF LSM is enabled in the system.
- cleanup Removes all old BPF entities (programs, maps, links) from BPFFS, to stop the execution of old BPF programs. All directories with timestamps lower than the current ones get removed.
- delete_container
- delete_process
- hash The simple string hash function allows to use of strings as keys for BPF maps even though they use u32 as a key type.
- init_runtimes Registers the names of supported container runtime init processes in a BPF map. Based on that information, BPF programs will track those processes and their children.
- load_programs Performs the following BPF-related operations:
- skel_reused_maps
- write_policy
Install & Use
Copyright (C) 2021 rancher-sandbox