According to mobile security company Lookout, since 2011, users have received an average of 85% increase in the speed of receiving and clicking on phishing URLs on mobile devices. What is more worrying is that 56% of users received and clicked on the phishing URL that bypassed the existing protection layer. On average, users clicked on the mobile phishing URL six times a year.
Lookout said in a new report analyzing the current state of mobile phishing that attackers successfully circumvented existing network firewalls, targeted mobile devices, and then managed to expose sensitive personal information at an alarming rate.
Since over 66% of e-mails were first opened on mobile devices and e-mail was the primary target of phishing attacks, unprotected e-mail on mobile devices could easily become a new route of attack. “Because of traditional firewalls, secure email gateways, and port protection, most companies are protected from e-mail-based phishing attacks. In addition, today people’s ability to identify phishing attacks is increasing. However, collecting individuals Identifying and blocking phishing attacks with existing security technologies is much more difficult,” said Lookout in the report.
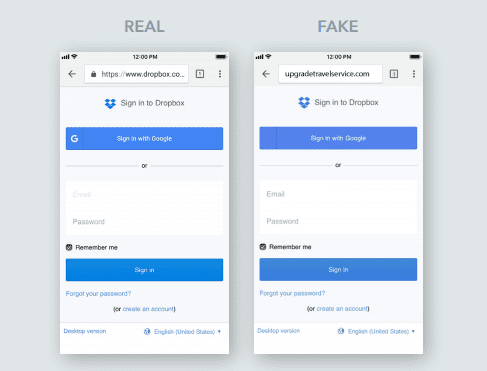
 The security company claims that existing phishing protection measures are not suitable for mobile devices, where a relatively small screen makes it more difficult to distinguish genuine login pages from fake login pages. In addition, SMS and MMS also provide new means of fishing for attackers, not to mention high-frequency personal social media applications and messages such as WhatsApp, Facebook Messenger, and Instagram. According to Lookout’s data, more than 25% of employees click on the link in a text message by forging a phone number.
The security company claims that existing phishing protection measures are not suitable for mobile devices, where a relatively small screen makes it more difficult to distinguish genuine login pages from fake login pages. In addition, SMS and MMS also provide new means of fishing for attackers, not to mention high-frequency personal social media applications and messages such as WhatsApp, Facebook Messenger, and Instagram. According to Lookout’s data, more than 25% of employees click on the link in a text message by forging a phone number.
Lookout also pointed out that the likelihood of a user clicking on a suspicious link on a mobile phone is three times that on a PC. On mobile devices, users cannot always see the entire link they clicked on, and they always have no firewall to protect the device. And because some applications include URLs in the code base to communicate and obtain information in real time, attackers can abuse phishing. For example, apps often use ads to make money. To do this, they integrate the advertising SDK into the code. These SDKs connect to behind-the-scenes URLs to display advertisements to end users. If a benign application uses an ad SDK run by an attacker, then An attacker may use the SDK to access malicious URLs to show ads that are designed to trick users into ultimately giving up sensitive data.