According to TheNextWeb, the personnel responsible for the 2-1-1 system database in Los Angeles County recently made a mistake, resulting in the disclosure of a document containing 3.2 million sensitive data – most of which included personal identification information of abuse and crisis victims’ phones. The Amazon Web Services (AWS) S3 bucket contains details of more than 200,000 calls from Los Angeles County’s 2-1-1 phone, which helps abuse victims and people in crisis.

However, the Amazon Web Services (AWS) S3 bucket was configured for public access for an unknown period of time – until security researchers noticed. This leaked case revealed more than 33,000 social security numbers, more than 300,000 e-mail addresses and many abuse victims, the full names of alleged perpetrators and witnesses.
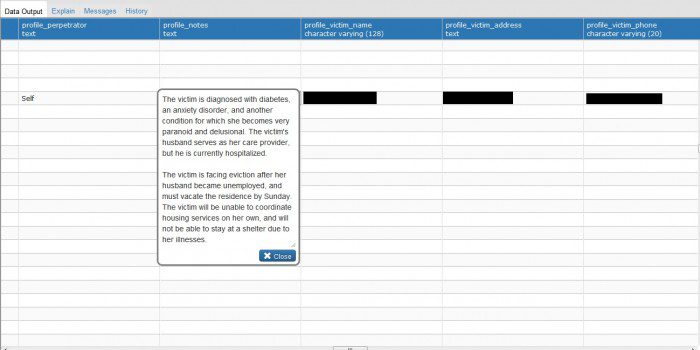
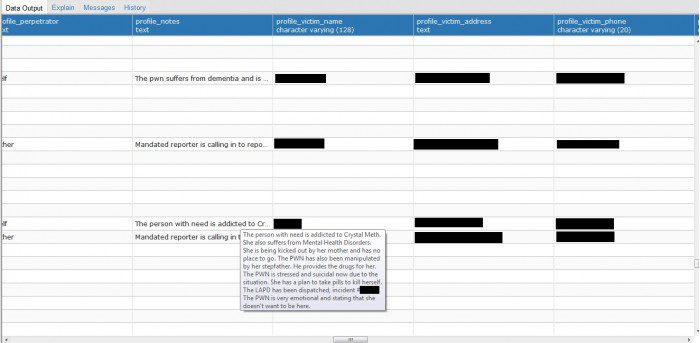
In addition, the S3 bucket holds the “weak hash” password for 384 logins. By using these certificates to log into Los Angeles County’s 2-1-1 LinQ system, content previously unavailable to malicious actors from the S3 bucket is now available. According to reports, after the incident occurred earlier this week, security personnel have encrypted the bucket.
Chris Vickery, a cyber-risk analyst at online security assessment startup UpGuard, found the vulnerability by searching publicly accessible AWS buckets, including files or folders with the word “prefecture” in files or folders. Just like all the vulnerabilities he exposed, all that is needed to access this information is an ordinary old Internet browser.
If a “hacker” can use IE, Chrome, Firefox, Opera or Safari, they have all the tools needed to “hack” these AWS buckets. Worse yet, Amazon has already taken steps to alleviate this type of problem, but it still exists.
Vickery previously found similar vulnerabilities in both the NSA and the Department of Defense databases (all caused by the same AWS S3 bucket misconfiguration). He said that when it comes to this type of leak, we are still in the “shunt phase” – which means that they will always happen until someone finds a way to ensure that the AWS bucket is not publicly accessible: making it inaccessible.
Source, Image: TheNextWeb