lsrootkit: Rootkit Detector for UNIX
lsrootkit
Rootkit Detector for UNIX (the actual beta only works as expected in Linux)

Features
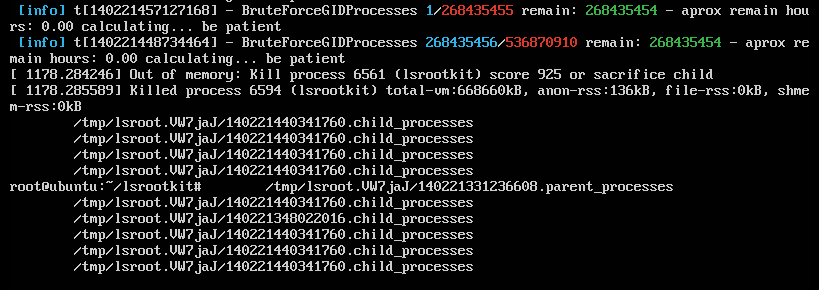
The idea is very simple: a lot of rootkits uses a MAGIC GID (a random GID generated) to hide processes and files. This tool finds rootkits bruteforcing all GIDs possible in the system.
- Processes: Full GIDs process occupation (processes GID bruteforcing)
- Files: Full GIDs file occupation (files GID bruteforcing)
It also can detect some rootkits safeguards and strange things in the hooked code.
Also, some rootkits use a MAGIC (kill) SIGNAL (a random SIGNAL generated) to hide processes. This tool can bruteforcing all Signals possible in the system:
- Processes: Kill Signal process occupation (processes Kill bruteforcing)
lsrootkit needs run as root or with caps for bruteforce: stat, chown, setgid & access to /proc
Warning: each analysis-feature can take: 48 hours in a QUADCORE CPU 3100.000 MHz (NO SSD).
For processes (GID)
- It creates a PARENT and a CHILD processes.
- The CHILD in a loop from 0 to MAX_GID_POSSIBLE calls to setgid(ACTUAL_GID).
- The CHILD sends the new GID to PARENT via a pipe. (It calls to getgid() to get the new gid).
- If the GID returned from getgid() is different from ACTUAL_GID (used in setgid(ACTUAL_GID)): Alert! this is impossible, can be a rootkit doing strange things.
- If setgid(ACTUAL_GID) fails: Alert! this is impossible, can be a rootkit doing strange things.
- If in two loop-iterations the GID returned is the same (last_gid == new_gid): Alert! this is impossible, can be a rootkit doing strange things.
- In each iteration, the PARENT checks if exist the PID of the child in: /proc (readdir/getdents). When the child PID is not listed: bingo!! the new GID is the MAGIC_GID of a rootkit. The rootkit is hidding the process.
- Also, the PARENT checks if the ACTUAL_GID recived from the PIPE is the same listed in /proc/pid/status. When is different: Alert! this is impossible, can be a rootkit doing strange things.
For files (GID)
- It creates a loop from 0 to MAX_GID_POSSIBLE calling to chown(ACTUAL_GID).
- If the GID returned from stat() is different from ACTUAL_GID (used in chown(ACTUAL_GID)): Alert! this is impossible, can be a rootkit doing strange things.
- If chown(ACTUAL_GID) or stat() fails: Alert! this is impossible, can be a rootkit doing strange things.
- If in two loop-iterations the GID returned is the same (last_gid == new_gid): Alert! this is impossible, can be a rootkit doing strange things.
- In each iteration, the process checks if exist the file in the directory (readdir/getdents). When the file is not listed: bingo!! the new GID is the MAGIC_GID of a rootkit. The rootkit is hidding the file.
Install
git clone https://github.com/David-Reguera-Garcia-Dreg/lsrootkit.git cd lsrootkit gcc -lpthread -o lsrootkit lsrootkit.c
If fails try:
gcc -pthread -o lsrootkit lsrootkit.c
Use
Very Important: if lsrootkit process crash you can have a rootkit in the system with some bugs: memory leaks etc.
Copyright (c) 2018 David Reguera Garcia aka Dreg