Image: Perception Point
The cyber realm has witnessed the emergence of a new, sophisticated threat: the LUMMA malware. In a recent investigation by Perception Point’s research team, this insidious malware was discovered to be the centerpiece of a multi-layered fake invoice campaign, representing a significant advancement in the tactics used by cybercriminals.
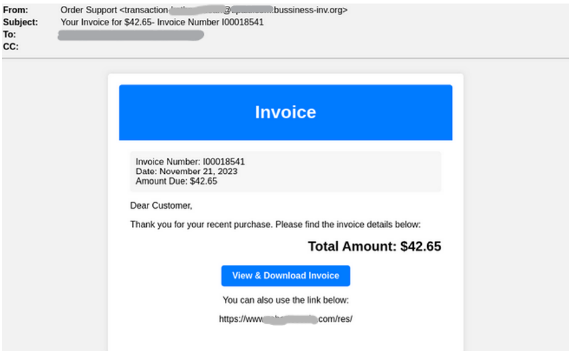
The LUMMA malware operation begins with an attacker impersonating a financial services company, sending an email containing a fraudulent invoice. This email cleverly prompts the recipient to click on a “View & Download Invoice” button. To lend credibility to the message, a legitimate website link is provided as an alternative to the button, a tactic designed to add a veneer of legitimacy to the deceit.

The strategic use of an unavailable page and a legitimate website link serves as a sophisticated form of evasion. Most security solutions scanning the message fail to detect the malicious payload, as the first link leads to an error page, and the second link appears to be a non-malicious website. This cunning design effectively circumvents traditional security measures.
When the unsuspecting user clicks on the website link, they are redirected to another URL, triggering the automatic download of a JavaScript file. This file contains several other files, including the malicious LUMMA payload. Intriguingly, the attacker must have first compromised the legitimate website to host the URL redirect, adding another layer of complexity to the attack.
LUMMA, an InfoStealer malware written in C language, is distributed through a Malware-as-a-Service model. Its execution involves three processes: “1741.exe,” “RegSvcs.exe,” and “wmpnscfg.exe.” The first process, “1741.exe,” notably runs from the user’s temporary folder, a characteristic that raises suspicions about its legitimacy. The second process, “RegSvcs.exe,” originates from the Microsoft.NET framework folder, commonly associated with malware activities, particularly in registering and executing malicious .NET assemblies. The third process, “wmpnscfg.exe,” adds complexity by executing from the Windows Media Player folder.
Each process is intricately linked to a parent process with specific Process IDs (PIDs), a deliberate choice by the attackers aiming to obfuscate their malicious activities and evade detection.
The LUMMA malware incident underscores the evolving tactics of cyber threat actors and emphasizes the necessity for organizations to continuously reassess the effectiveness of their security systems. It highlights the critical need for advanced threat prevention technologies, continuous monitoring, and a multi-layered security approach to effectively detect and mitigate such sophisticated cyber threats. As cyber adversaries adapt and evolve, so must our defensive strategies to protect sensitive information and systems against these cunning digital predators.