Mac Malware Alert: The Rampant Rise of macOS.Bkdr.Activator
In the Internet age, the allure of “free” often comes with hidden costs, particularly through the cracked software markets prevalent across torrent services. This realm, notorious for its cryptominers, adware, and browser hijackers, has now become the breeding ground for a more sinister threat: the macOS.Bkdr.Activator malware. This malicious software, first identified by cybersecurity researchers at Kaspersky, has surged through the macOS ecosystem, embedding itself within cracked versions of popular and business-critical applications. Recently, the security researchers from SentinelOne revealed more details about this malware.

macOS.Bkdr.Activator represents a concerning evolution in cyber threats, targeting macOS users on an unprecedented scale. Its primary aim appears to be the creation of a macOS botnet or the mass distribution of further malware. The campaign is sophisticated, utilizing a multi-stage delivery process that includes novel techniques to ensure its proliferation and persistence.
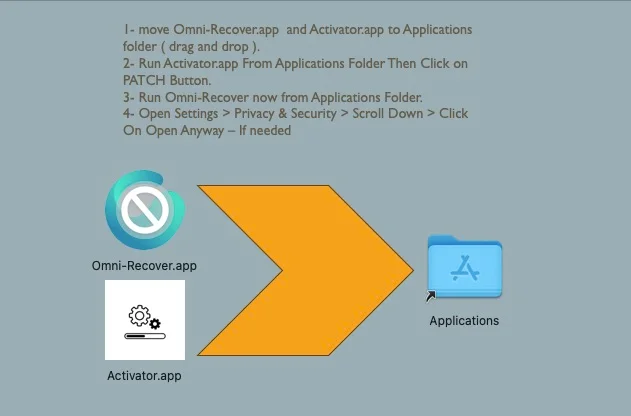
The initial infection vector is a disk image obtained via torrent links, containing a seemingly unusable version of the desired software and an ‘Activator’ application. This Activator, when launched, prompts users for administrative access, subsequently disabling macOS’s Gatekeeper security feature to allow apps from any source to run unchecked. The malware then employs Python scripts to execute a series of malicious actions, including the installation of a LaunchAgent for persistence and attempting to retrieve and execute additional Python scripts based on unique conditions.
One of the more innovative aspects of macOS.Bkdr.Activator is its use of the macOS defaults system for storing information about its operations, a technique not commonly seen in malware. Additionally, the malware employs a novel communication method to retrieve further instructions or payloads via encoded DNS responses, showcasing the complexity and stealthiness of its operation.
This campaign has led to the infection of hundreds of unique binaries, impacting a wide range of applications. From productivity tools to media software, the breadth of affected applications indicates a broad targeting strategy, likely aiming to compromise devices across various sectors and user demographics.
The discovery of macOS.Bkdr.Activator underscores a critical reminder for users and organizations alike: the dangers of sourcing software from unverified locations. As malware authors continue to innovate and adapt, the importance of maintaining rigorous cybersecurity practices and awareness of the latest threats cannot be overstated.