macOS Security Compromised: Novel Exploit Bypasses Sandbox Protections
A newly discovered vulnerability in macOS could allow attackers to bypass critical security mechanisms and gain unauthorized access to sensitive files. This revelation comes from independent security researcher Mickey Jin, who presented his findings at the POC2024 conference.
Jin’s research focuses on exploiting weaknesses within macOS’s Inter-Process Communication (IPC) mechanism, specifically XPC services. These services, designed for communication between different processes, have been found to possess vulnerabilities that can be leveraged to circumvent the operating system’s sandbox protections.
Exploiting XPC Services to Breach Security Barriers
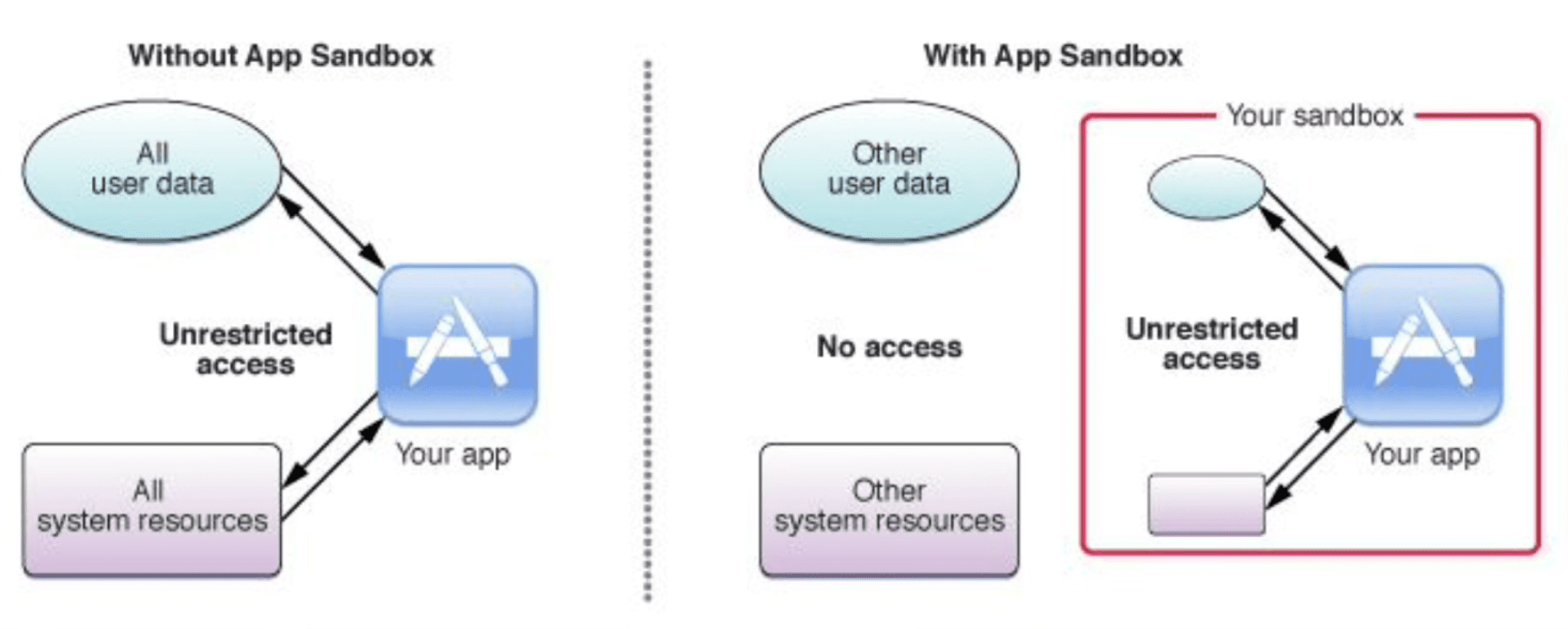
macOS employs sandboxing to restrict application access to system resources and user data, enhancing overall system security. However, Jin’s research demonstrates how certain XPC services, particularly those residing within system frameworks, can be manipulated to escape these sandbox constraints. Researcher discoveries multiple sandbox escape vulnerabilities: CVE-2023-27944, CVE-2023-32414, CVE-2023-32404, CVE-2023-41077, CVE-2023-42961, CVE-2024-27864, CVE-2023-42977, and more.
By exploiting these vulnerabilities, malicious actors can gain elevated privileges, effectively bypassing the intended security limitations. One notable example highlighted by Jin is the “ShoveService,” which can be exploited with minimal code to achieve system-level command execution.
Apple’s Mitigation Efforts and Ongoing Research
Apple has responded to these findings by releasing patches for several identified vulnerabilities. However, Jin’s research remains ongoing, as some vulnerabilities, particularly those related to XPC services with inadequate client permission verification, are still under investigation.
In recent macOS versions, such as Ventura and Sonoma, Apple has introduced several security enhancements to mitigate these threats:
- Mandatory XPC client authorization: This ensures that only authorized processes can access sensitive XPC services.
- Access restrictions to vulnerable services: This limits the interaction of applications with potentially exploitable services.
- Enhanced protection mechanisms: These safeguards prevent unauthorized commands from being executed, bolstering system security.
Recommendations for Enhanced Security
Users are strongly advised to keep their macOS systems updated to the latest versions to benefit from the most recent security patches. Additionally, exercising caution when downloading and installing applications, particularly from untrusted sources, is crucial in minimizing the risk of compromise.




