Mad Liberator Ransomware Group Exploits Anydesk to Steal Data in Stealthy Attacks
Sophos X-Ops Incident Response team has recently uncovered the tactics of a relatively new ransomware group known as Mad Liberator, which has been active since mid-July 2024. The group has garnered attention for its use of the popular remote-access application Anydesk to execute highly targeted and covert attacks on unsuspecting victims.
Mad Liberator is a ransomware group that primarily focuses on data exfiltration rather than the typical encryption of files seen in many other ransomware campaigns. While there have been reports, notably from watchguard.com, suggesting that the group occasionally employs encryption and engages in double extortion tactics—where they both steal and encrypt data—the core of their operation appears to be exfiltrating sensitive information and pressuring victims to pay by threatening to release the stolen data.
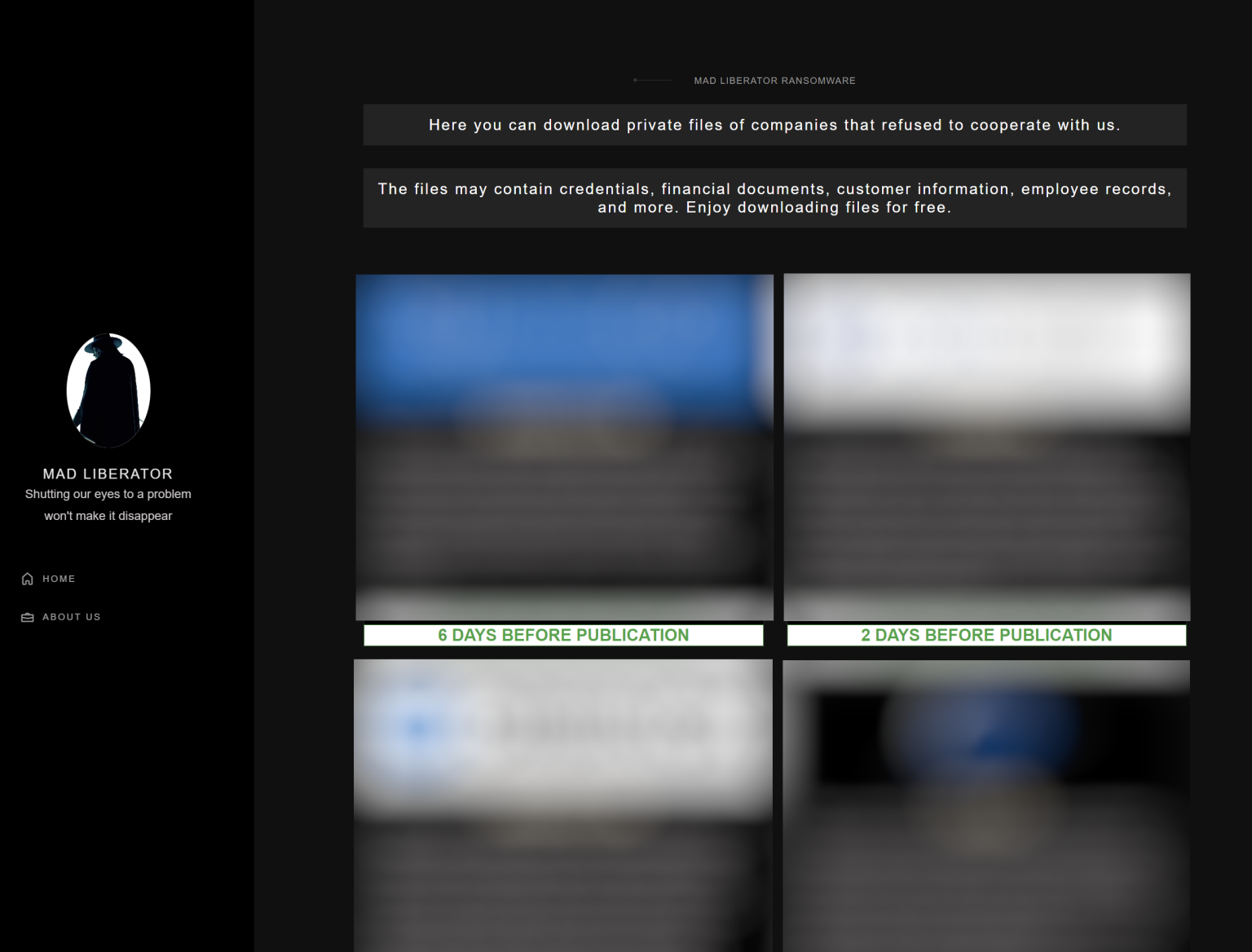
Mad Liberator also runs a leak site where they publish victim details to further coerce payment. The site provocatively claims that these files can be downloaded “for free,” adding an extra layer of intimidation for their targets.
In the incidents observed by the Sophos X-Ops team, Mad Liberator utilized Anydesk, a legitimate remote-access tool commonly used by IT teams to manage devices. While Anydesk itself is not malicious, the attackers have found a way to exploit it for their nefarious purposes.
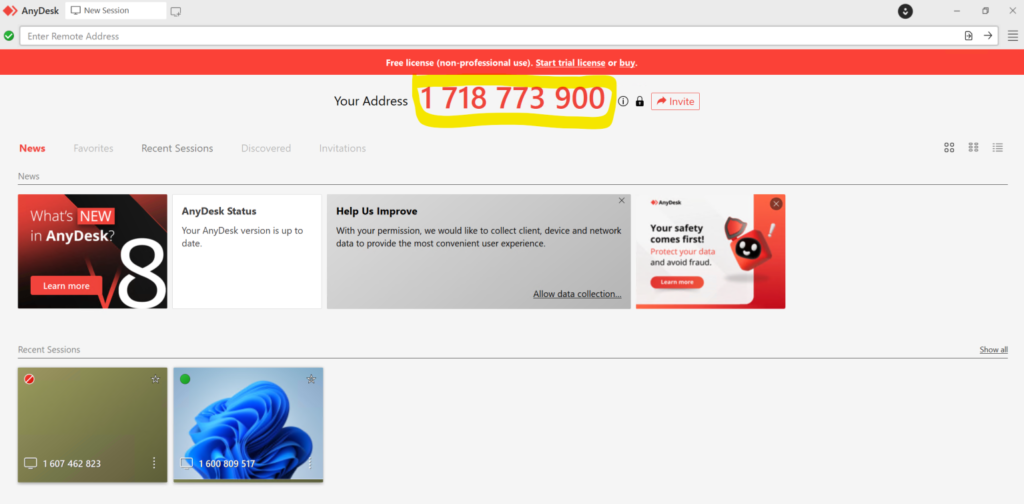
An Anydesk session with the ten-digit address prominently displayed | Image: Sophos
Anydesk assigns a unique 10-digit ID to each device on which it is installed. Users can either request access to a remote device by entering its ID or invite another user to take control of their device via a remote session. In the cases investigated by the Sophos X-Ops team, victims received unsolicited Anydesk connection requests. These victims were not high-profile targets, and there was no clear indication of why they were selected, suggesting that the attackers may have been indiscriminately cycling through potential IDs until they found one that responded.
Once the connection request was accepted, often under the mistaken belief that it was a routine IT maintenance operation, the attacker would upload and execute a binary titled “Microsoft Windows Update” on the victim’s device. This binary, while simple, was ingeniously deceptive: it displayed an animated splash screen mimicking a standard Windows Update, effectively disguising the attack.
While the fake update screen was displayed, the attacker took additional steps to ensure their activities went unnoticed. Utilizing Anydesk’s features, they disabled the victim’s keyboard and mouse inputs, preventing them from interrupting the attack. With control of the device secured, the attacker began exfiltrating data from the victim’s OneDrive account and other files stored on a central server accessible via a mapped network share.
The attack lasted for nearly four hours, during which time the attacker stole sensitive company files using Anydesk’s FileTransfer facility. They also employed Advanced IP Scanner to scan the local network for other devices of interest, though no lateral movement was observed in this instance.
Once the data theft was complete, the attacker executed another program that generated numerous ransom notes across shared network locations. These notes informed the victim that their data had been stolen and provided instructions on how to pay the ransom to prevent the public release of the stolen files.
After the attack, the fake update screen was terminated, and the Anydesk session was ended, returning control of the device to the victim. The binary remained on the system but was not set to run again, making it unlikely to be detected as malicious by many antivirus programs.
Organizations and individuals should exercise heightened caution when handling unsolicited Anydesk connection requests, particularly those from unfamiliar sources. Verification of the request’s legitimacy is paramount before granting access. Additionally, maintaining up-to-date remote access software and implementing robust access controls are crucial.
Related Posts:
- AnyDesk’s Cybersecurity Breach: Unveiling the Recent Attack
- AnyDesk Breach 2024: Dark Web Sale of 18,317 Credentials
- Patch Now! Ladon, AnyDesk, and More Lurk in Unpatched ActiveMQ Servers
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities
- Unpatched Vulnerabilities: Ransomware’s Favorite Entry Point