MADLIRA: Malware detection using learning and information retrieval for Android
MADLIRA
Malware detection using learning and information retrieval for Android
Overview
MADLIRA is a tool for Android malware detection. It consists of two components: TFIDF component and SVM learning component. In general, it takes an input a set of malware and benwares and then extracts the malicious behaviors (TFIDF component) or computer training model (SVM classifier). Then, it uses this knowledge to detect malicious behaviors in the Android application.
Installing
Download file MADLIRA.7z and decompress it.
Installed Data:
- MADLIRA.jar is the main application.
- noAPI.txt declares the prefix of APIs.
- family.txt lists malwares by family.
- Folder TrainData contains the training configuration and training model.
- Folder Samples contains sample data.
- Folder TempData contains data for kernel computation.
Functionality
This tool have two main components: TFIDF component and SVM component.
TFIDF component
Command: MADLIRA TFIDF
For this component, there are two functions: the training function (Malicious behavior extraction) and the test function (Malicious behavior detection)
Malicious behavior extraction
- Collect benign applications and malicious applications and oput them in folders named benginAPKFolder and maliciousApkFolder, respectively.
- Prepare training data and pack them in two files named benignPack and maliciousPack by using the command:
MADLIRA TFIDF packAPK -PB benignApkFolder -B benignPack -PM maliciousApkFolder -M maliciousPack
- Extracting malicious behaviors from two packed files (benignPack and maliciousPack) by using the command:
MADLIRA TFIDF train -B benignPack -M maliciousPack
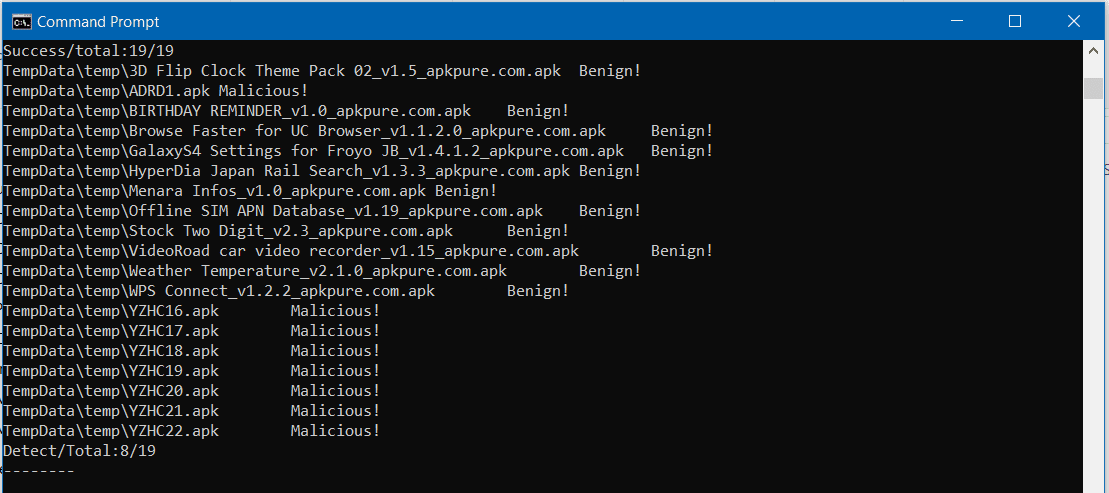
Malicious behavior detection
- Collect new applications and put them in a folder named checkApk.
- Detect malicious behaviors of applications in the folder checkApk by using the command:
MADLIRA TFIDF check -S checkApk
Command:

Copyright (C) 2018 dkhuuthe
Source: https://github.com/dkhuuthe/





