Major VPN Flaw Exposed: “TunnelVision” (CVE-2024-3661) Threatens Security on Public Networks

The very backbone of Virtual Private Networks (VPNs), praised for their ability to secure online activities, is under scrutiny following a breakthrough discovery by Dani Cronce and Lizzie Moratti from Leviathan Security Group. Their research introduces “TunnelVision,” a technique that can compromise all routing-based VPNs by exploiting vulnerabilities in local network configurations.

The Revelation of TunnelVision
TunnelVision, officially cataloged as CVE-2024-3661 (CVSS 7.6), exploits a fundamental flaw in how devices on a local network handle routing decisions, which can lead to complete VPN bypasses. Unlike previous methods that required sophisticated attacks on VPN servers, TunnelVision operates on the local network level, making it remarkably easier to exploit and affecting virtually any device using routing-based VPNs.
How TunnelVision Operates
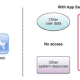
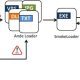
CVE-2024-3661 exploits the routing tables used by operating systems to determine network traffic paths. By manipulating these tables, an attacker on the same local network can reroute VPN traffic to a different network, essentially bypassing the VPN’s security mechanisms. This can be achieved without needing to compromise critical network infrastructure such as DHCP servers, making the attack notably straightforward and potent.
Impact and Implications
TunnelVision has been tested and confirmed to affect multiple operating systems that support DHCP option 121 routes, including Windows, Linux, iOS, and MacOS. Android is notably unaffected due to its lack of support for DHCP option 121.
This discovery is particularly alarming for individuals and organizations relying on VPNs for privacy and security—especially journalists, activists, and political dissidents who use these services to shield their activities from hostile entities. The research indicates that while most commercial VPN traffic is encrypted via HTTPS, the exposure of metadata (like destination addresses) still poses significant privacy risks. Moreover, any traffic over HTTP is left completely unprotected, revealing all transmitted data.
Technical Insights and Research Tools
The Leviathan team has also provided the community with tools and resources to analyze and demonstrate the TunnelVision technique. These include a detailed blog post, a video proof of concept, and a GitHub repository with lab setup code, which simulate various attack scenarios like compromised DHCP servers and rogue access points.
Challenges in Remediation
Addressing the vulnerabilities exposed by TunnelVision is complex, as the issue lies not with the VPN technologies themselves but with the foundational network and operating system configurations. The researchers propose several mitigations, such as using network namespaces on Linux to isolate network interfaces from general traffic routes. However, other operating systems lack robust solutions, highlighting a significant gap in current VPN security assurances.
Broader Implications for Cybersecurity
TunnelVision’s unveiling challenges the long-standing perceptions of VPN security. It underscores the need for a more nuanced understanding of what VPNs can and cannot secure. The technique’s potential has been latent since as early as 2002, suggesting that many could have unknowingly been compromised.
Conclusion and Call to Action
The findings from Cronce and Moratti have triggered a vital conversation about the efficacy of VPNs in safeguarding user privacy on local networks. They emphasize a collective responsibility among VPN providers, users, and operating system developers to reevaluate and reinforce the security frameworks surrounding VPN usage.
For users, the advice is clear: avoid using VPNs on untrusted networks without additional protections, such as network segregation or enhanced firewall settings. For VPN providers and OS developers, this is a call to refine their systems and marketing to align with the realities of these newfound vulnerabilities.