malboxes v0.5 releases: Builds malware analysis Windows VMs

Malboxes is a tool to streamline and simplify the creation and management of virtual machines used for malware analysis. Building analysis machines is a tedious task. One must have all the proper tools installed on a VM such as a specific version of vulnerable software (ie: Flash), Sysinternal tools, debuggers (Windbg), network traffic analyzers (Wireshark), man-in-the-middle tools (Fiddler). One must also avoid leaking his precious proprietary software licenses (IDA). At the moment, this menial job is not automated and is repeated by every analyst.

Malboxes leverages the DevOps principle of infrastructure as code to enable researchers to automatically create fully operational and reusable analysis machines. The tool uses Vagrant and Packer to do an initial out-of-band bootstrapping. Afterwards, chocolatey is used to install further tools benefiting from the chocolatey package repository.
You will learn a simple tool for safe malware analysis practice that is easy to grasp, enabling them to start doing analysis faster. Seasoned malware researchers will also gain from this demo by seeing how the DevOps approach can be applied to simplify and accelerate their labs’ malware reverse-engineering capacity or reduce its management overhead.
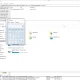
Malboxes’ Architecture
In a nutshell, malboxes wraps together:
- A packer configuration
- Windows unattended installation configuration
- PowerShell recipes to disable security features (Defender, auto-updates, firewall, etc.)
- A set of malware analysis focused tools installed using the Windows package manager chocolatey
- A Vagrantfile generator so that the VMs can be managed with Vagrant
Another benefit is that malboxes, packer, vagrant and the PowerShell scripts all stay out of the guest. Benefits of this architecture include leveraging chocolatey packages. This means one can install anything available in the extensive chocolatey package gallery with a single command. The default list of packages installed can be modified in malboxes’ configuration file. Additionally, packaging for chocolatey is straightforward so there is a huge network effect around chocolatey right now which we benefit from.
Changelog v0.5
BlackHat USA Arsenal 2019 [late] Edition!
Enhancements
- Support for Windows 10 19H1 (version 1903) (#128)
- New tools: Ghidra, x64dbg, ollydbg, dnSpy, Detect It Easy (die), HxD, PE-Sieve, PE-Bear (#9, #125)
- New deployment target: Amazon Web Services EC2 (for the VM) and S3 (for the image) (#115)
- Using VirtualBox’s linked clones by default now.
Creating a new spin of an existing template is now instant. (#126) - Enabling UAC so the default account can use Edge without requiring changes (#93)
- Updated logo (#129)
Bug fixes
- Removed APM from default chocolatey packages (#119)
- Disabled malware protection, cloud and automatic sample submission on Windows 10 (#120, #128)
- Fix Windows 10 download links (#113, #116)
Infrastructure Improvements
Download && Use
Copyright (C) 2018