malcom: Malware Communication Analyzer
Malcom – Malware Communication Analyzer
Malcom is a tool designed to analyze a system’s network communication using graphical representations of network traffic, and cross-reference them with known malware sources. This comes in handy when analyzing how certain malware species try to communicate with the outside world.

It can help you:
- detect central command and control (C&C) servers
- understand peer-to-peer networks
- observe DNS fast-flux infrastructures
- quickly determine if a network artefact is ‘known-bad’
The aim of Malcom is to make malware analysis and intel gathering faster by providing a human-readable version of network traffic originating from a given host or network. Convert network traffic information into actionable intelligence faster.
Check the wiki for a Quickstart with some nice screenshots and a tutorial on how to add your own feeds.
Installation
For IP geolocation to work, you need to download the Maxmind database and extract the file to the malcom/Malcom/auxiliary/geoIP directory. You can get Maxmind’s free (and thus more or less accurate) database from the following link: http://dev.maxmind.com/geoip/geoip2/geolite2/:
Launch the web server from the malcom directory using ./malcom.py. Check ./malcom.py –help for listen interface and ports.
For starters, you can copy the malcom.conf.example file to malcom.conf and run ./malcom.py -c malcom.conf
Configuration options
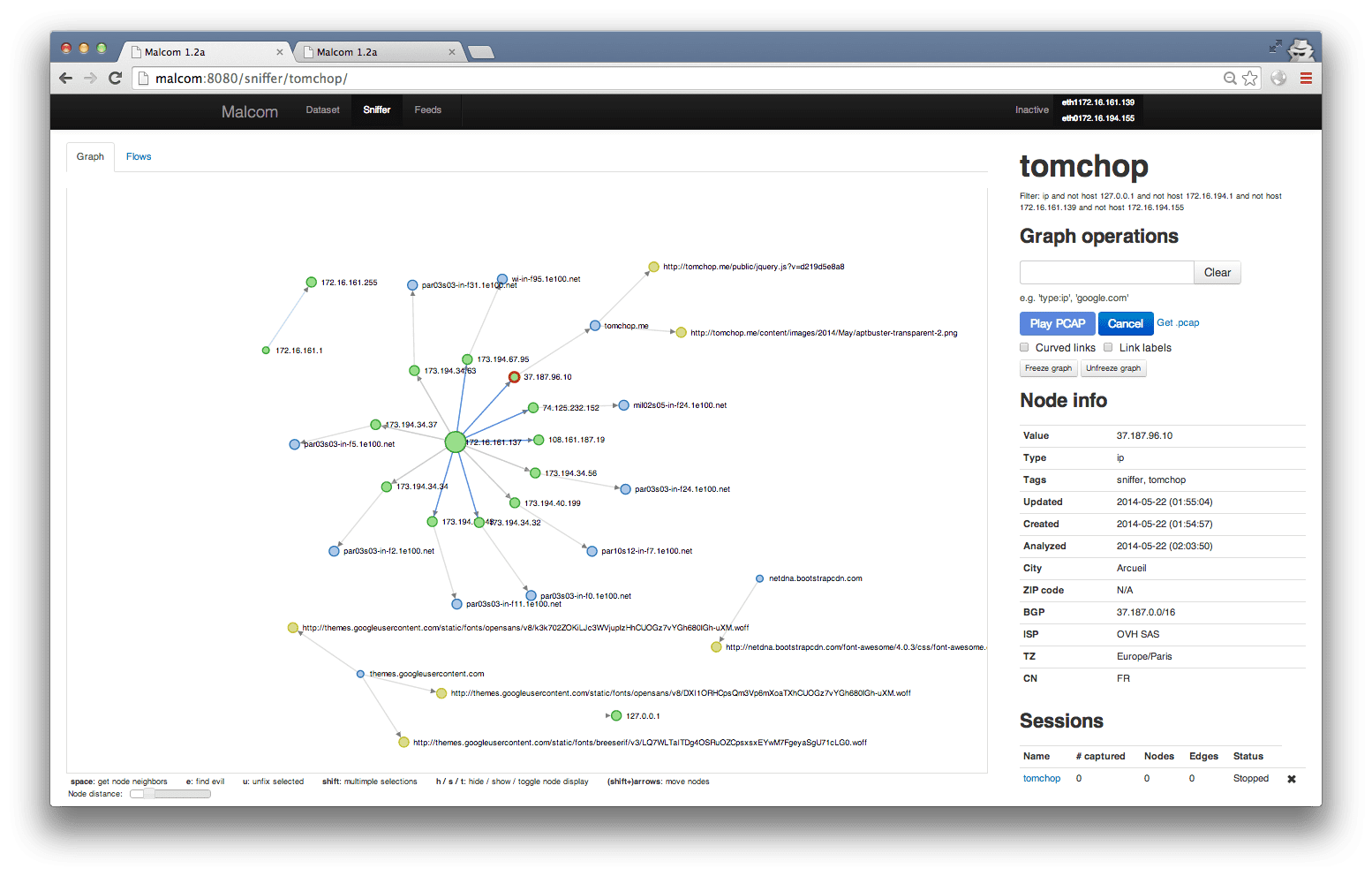
Dataset view (filtered to only show IPs)
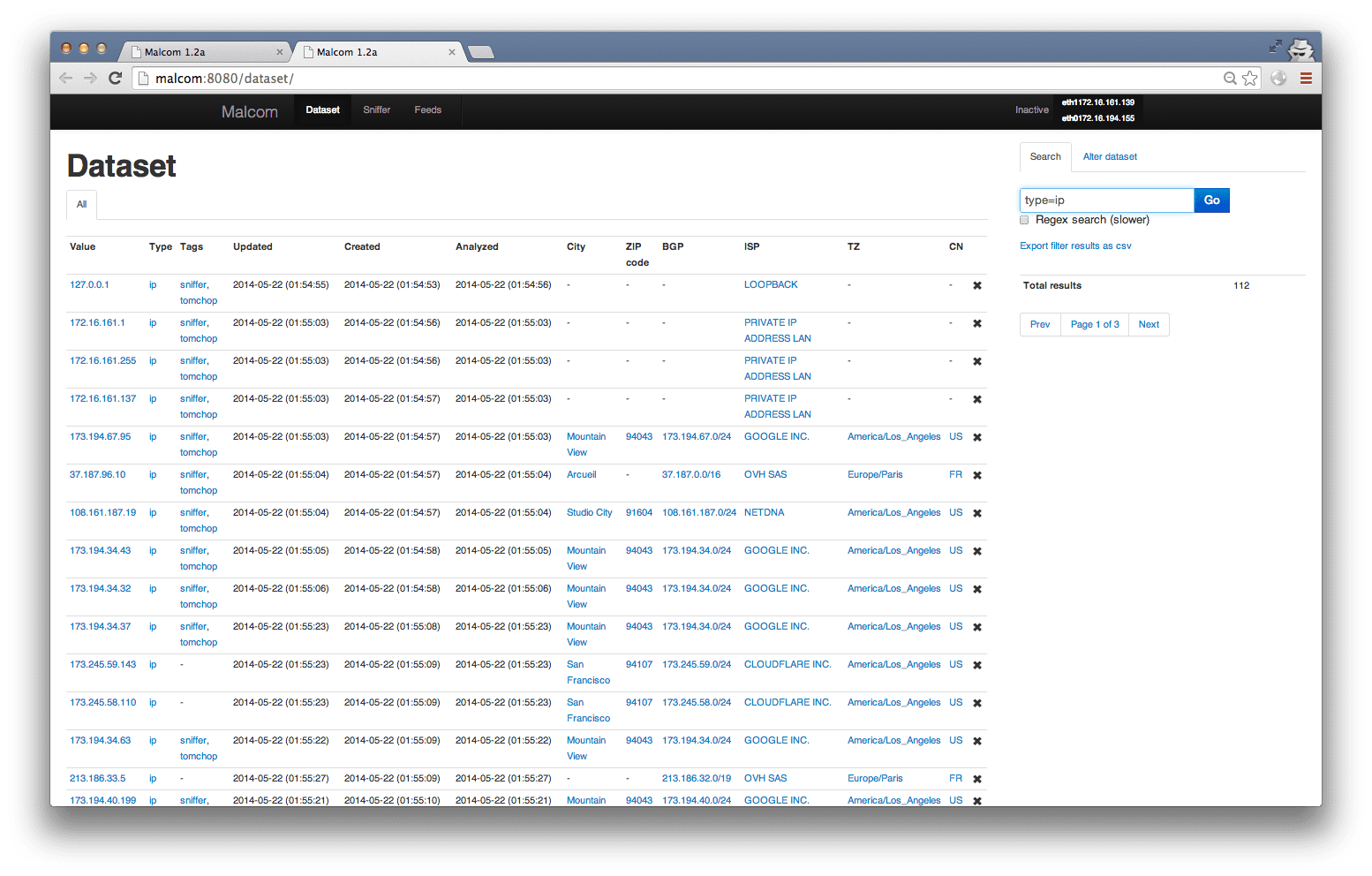
use Malcom for three main purposes:
- Quickly determine if a host, IP, or URL is “known-bad” (i.e. it has been flagged as being malicious by other websites or sources).
- Get some intelligence on what relates two different elements. For example, you could see that several different hosts are pointing to the same IP address (or small AS), which has been seen in previous attacks. Eventually, you could also see what those same hosts have been registered by three different email addresses, which have also been seen in phishing kits.
- Get a detailed overview of the kind of network traffic patterns a host is displaying. Is it pinging specific IP addresses? Is it sending SMTP traffic? Is it part of a botnet? What kind of C&C infrastructure is being used?
Copyright (C) 2013 Thomas Chopitea
Source: https://github.com/tomchop/





