
A new wave of cyberattacks has exposed a critical weakness in Secure Email Gateways (SEGs), allowing malicious emails to bypass security filters and deliver dangerous malware payloads. Cofense Intelligence has uncovered a sophisticated phishing campaign that exploits a loophole in how SEGs scan archive attachments, specifically .zip files.
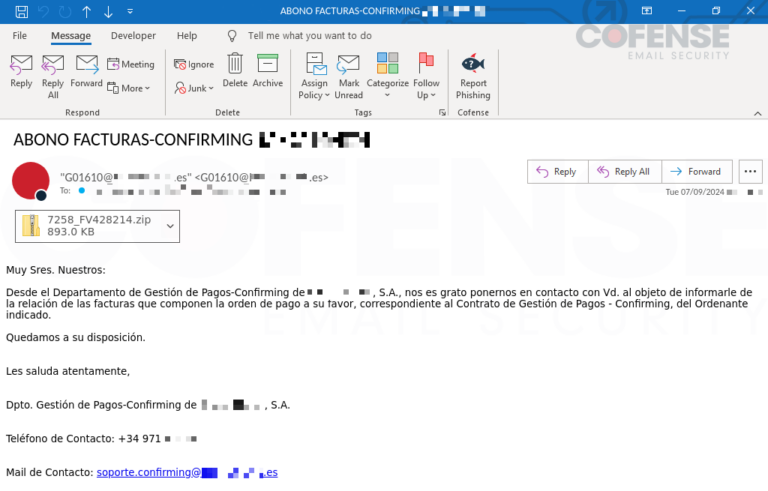
The malicious emails, targeted at employees of a major international financial firm, contained a seemingly harmless .zip attachment. By using a .zip archive attachment, threat actors managed to deceive SEGs into believing the archive contained a harmless .Mpeg video file. However, when the attachment is opened with common archive extraction tools like 7zip or Power ISO, it appears as a .Mpeg but does not play. When opened in Outlook or Windows Explorer, the file is correctly identified as an .html, allowing victims to execute the embedded FormBook malware.
Cofense Intelligence identified specific phishing emails targeting Spanish-speaking employees at an international financial firm. These emails, claiming to deliver an attached invoice, were notably sophisticated, including a full email body and signature, surpassing the typical phishing email format. The emails, sent using the “Roundcube Webmail/1.4.8” User-Agent, successfully bypassed Cisco IronPort and likely other SEGs as well.
The analysis revealed that malicious attachments bypassed SEG detection due to how SEGs parsed the file within the archive. If the SEG had directly received and scanned an email with the malicious HTML attached, it would have blocked it. However, when enclosed in a .zip archive, the SEG incorrectly identified the file as a .Mpeg. This flaw in SEG processing allowed the malware to slip through defenses.
Once the .html file is recognized and opened, it delivers another .zip archive. This secondary archive contains a .cmd file, actually a .cab archive, housing the malicious executable. The executable, identified as DBat Loader, downloads a payload, decrypts its contents, and runs FormBook in memory. This variant of FormBook contacts multiple C2 servers with different paths, enhancing its ability to evade detection.
FormBook, an information stealer, remains one of the most prevalent malware threats. It is capable of keylogging, file management, clipboard management, taking screenshots, logging network traffic, and recovering passwords, cookies, and forms from browsers. Additionally, it can download and execute other malware, further endangering infected users by opening the door to ransomware and other malicious attacks.
Related Posts:
- Backdoor Breaches: The Rise of Stealthy Linux System Attacks
- Beware of Instagram Influencer Scams: McAfee Labs Exposes New Threat
- Beware the Windows Search Scam: Clever Phishing Campaign Exploits User Trust