KMSPico is a popular activation software since the Windows 8 era. It supports activation of Windows 8/10 system and Office 2013/2016/2019 office software.
As the activation software, KMSPico is popular among pirated users all over the world, and that is why the hacker group also saw the opportunity to start spreading malicious KMSPico installers.
Malicious KMSPico installers do not have too high technical content. It mainly embeds malicious software in the activator and then distributes it through the Internet and software forums.

If the user downloads and uses this activator, the system will be implanted with a backdoor program, which is specifically used to steal the user’s installed cryptocurrency wallet.
The stolen cryptocurrency wallets are as follows
- Atomic cryptocurrency wallet
- Avast Secure web browser
- Brave browser
- Ledger Live cryptocurrency wallet
- Opera Web Browser
- Waves Client and Exchange cryptocurrency applications
- Coinomi cryptocurrency wallet
- Google Chrome web browser
- Jaxx Liberty cryptocurrency wallet
- Electron Cash cryptocurrency wallet
- Electrum cryptocurrency wallet
- Exodus cryptocurrency wallet
- Monero cryptocurrency wallet
- MultiBitHD cryptocurrency wallet
- Mozilla Firefox web browser
- CCleaner web browser
- Vivaldi web browser
When the malware is deployed, it will automatically detect whether the user installs the above-mentioned wallet software, and if it is installed, find a way to steal the file and trick the user’s key.
It is worth noting that while the malware is deployed, its activation function can indeed be used, so it should be difficult to find that you have been infected with a virus after activation.
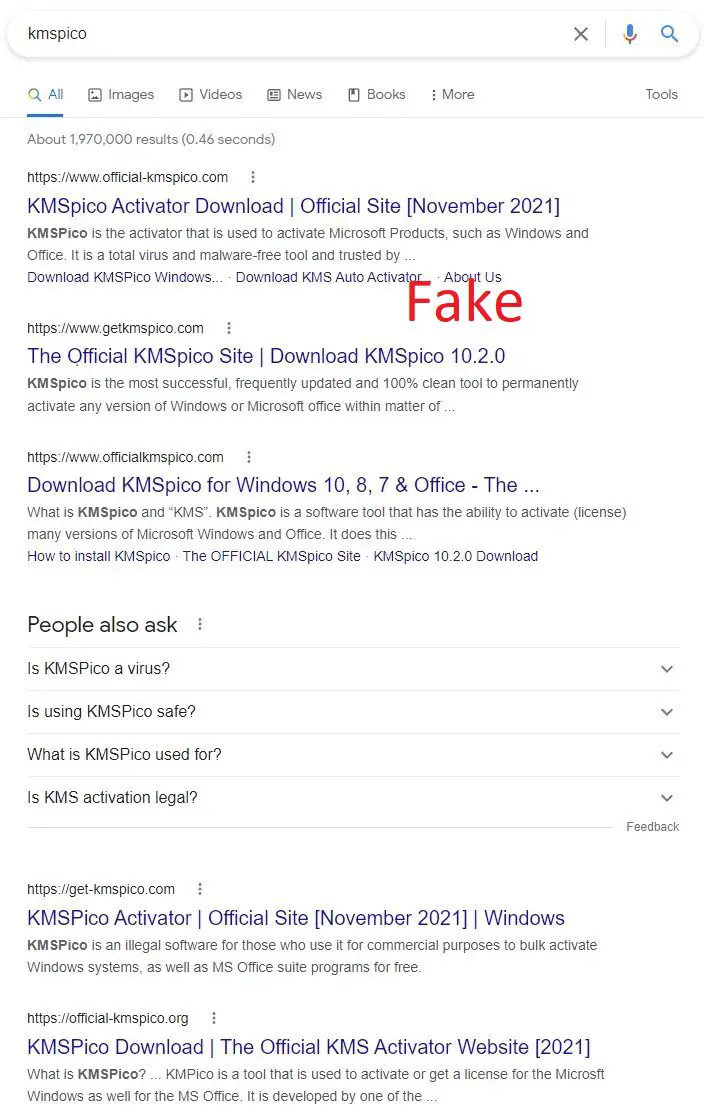
It should be emphasized that as a pirated software activation tool KMSPico itself does not have an official website. Searching on major search engines can see many so-called official websites.
Some of these so-called official websites provide installations that contain viruses, and some may just be used to add advertisements. It is actually difficult for users to find the official originals.
In addition, this activator may also be used by corporate users. If it is used by corporate users, it may also cause other devices in the corporate intranet to be infected by viruses.
Therefore, enterprises must also strictly manage the pirated tools downloaded by their employees. After all, the probability of carrying viruses in such tools is much higher than that of other conventional software.
Via: bleepingcomputer