Malicious npm Package Exposes AWS Users to Backdoor
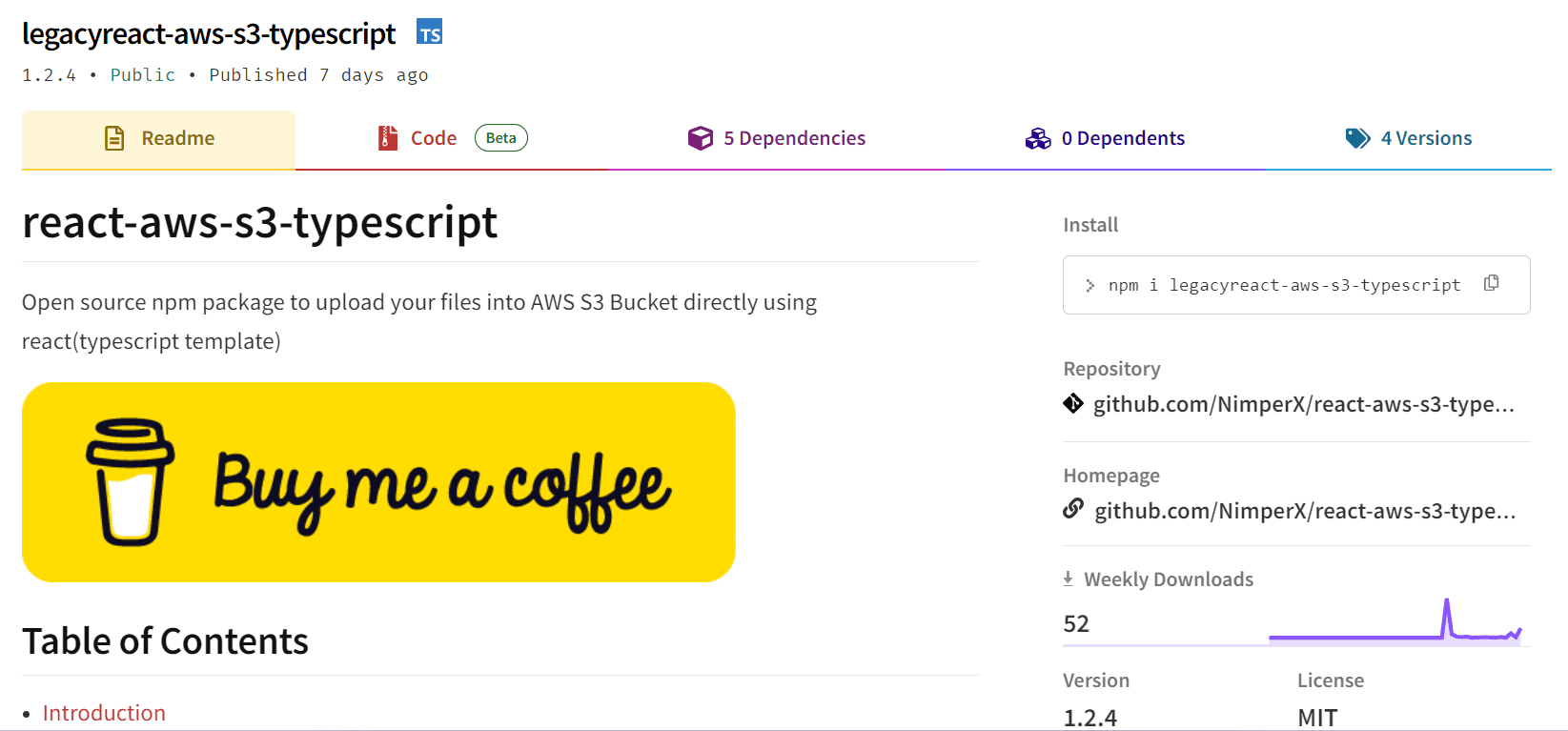
ReversingLabs researchers have uncovered a malicious package named “legacyreact-aws-s3-typescript” on the npm registry. The package, designed to mimic a legitimate tool for uploading files to Amazon S3 buckets, was found to contain a hidden backdoor that could grant attackers remote access to infected systems.
The malicious package remained dormant for four months before a series of suspicious updates were published in May 2024. While those updates were quickly removed, ReversingLabs managed to analyze them, confirming their malicious intent. The final version, 1.2.4, contained a post-install script that downloaded and executed a malicious ELF file, establishing a backdoor to a remote server.
legacyreact-aws-s3-typescript’s npm page | Image: ReversingLabs
Upon analysis, the ELF file was found to be a simple backdoor that opened a socket, connected to the IP address 91[.]238[.]181[.]250, and executed commands through /bin/sh. This led to the immediate classification of the package as malicious and its subsequent reporting to npm for removal.
The history of the legacyreact-aws-s3-typescript package underscores the challenges of monitoring open-source threats. Initial versions (1.1.5, 1.1.6, and 1.1.7) published in February 2024 were clean. However, subsequent versions (1.1.9, 1.2.1, and 1.2.2) published briefly in May contained malicious code. These versions were quickly removed, likely by the author, for reasons that remain unclear. The malicious functionality reappeared in version 1.2.4, which remained publicly accessible until detected by ReversingLabs.
The threat actors behind this attack employed typosquatting, a tactic where malicious packages adopt names similar to legitimate ones, hoping to trick unsuspecting users. The “legacyreact-aws-s3-typescript” package even copied content from the legitimate “react-aws-s3-typescript” package to further the deception.
ReversingLabs emphasizes the need for heightened scrutiny and security measures when working with open-source components. Developers should not only be cautious of known vulnerabilities but also of the potential for malicious code to be introduced through seemingly innocuous updates.





