A new wave of targeted attacks on Microsoft SQL (MS-SQL) servers has emerged, spearheaded by Mallox ransomware affiliates employing advanced exploitation tactics and the stealthy PureCrypter loader, according to a comprehensive report from Sekoia’s Threat & Detection Research (TDR) team.
Initial Discovery and Infection Flow

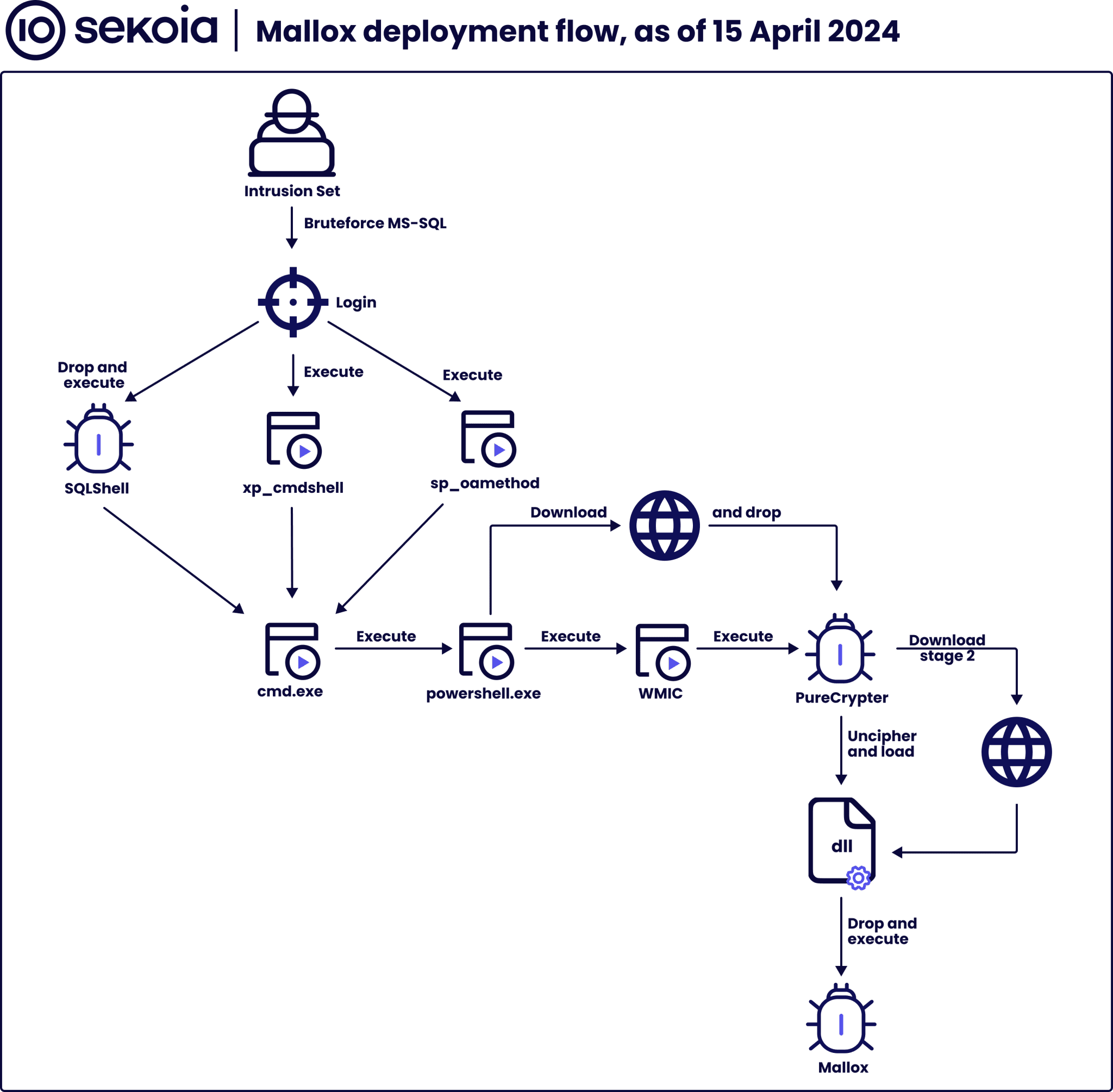
The incident came to light through a honeypot operation involving an MS-SQL server set up by Sekoia’s TDR team. Configured with mixed authentication and a weak password for the ‘sa’ (SQL Administrator) account, the server was compromised on April 15, 2024, within just 50 minutes of going online, highlighting the aggressiveness of the attack. The attackers, linked to hosting provider XHost Internet Solution (AS208091), made approximately 320 brute-force attempts per minute, ultimately gaining initial access and setting the stage for further exploitation.
Technical Analysis of Exploitation Techniques
Two distinct exploitation patterns were identified from the MS-SQL logs:
Exploitation Pattern 1:
- Configuration Changes: Attackers enabled “TRUSTWORTHY” and “clr enabled” settings in the master database, which are prerequisites for executing CLR Assembly—a technique for running user assemblies.
- Malware Deployment: A .NET DLL named “shell” was created in the “msdb” database with “Unsafe” permission. This DLL included a class called StoredProcedure with a cmd_exec function, capable of executing commands via cmd.exe.
- Command Execution: A stored procedure named cmd_exec was used to trigger the SqlShell malware, which subsequently downloaded and attempted to execute further malicious scripts using PowerShell and WMIC.
Exploitation Pattern 2:
- This pattern was less intricate, lacking the assembly deployment seen in the first pattern. It primarily involved exploiting system configurations and executing commands directly via tools like xp_cmdshell and Ole Automation Procedures.
Infection Chain and Malware Analysis
The payloads involved in the exploitation were identified as PureCrypter, which has previously been documented by Any Run for its distinct behavior:
- Payload Download: Initiated by downloading a file with a deceptive multimedia extension (e.g., mp4, wav, pdf).
- Decryption and Execution: The file, encrypted with 3DES, decrypts to a .NET library that employs Reflective Code Loading to execute Mallox ransomware, identified as PureCrypter’s stage2.
Detection and Mitigation Recommendations
The Sekoia TDR team emphasizes the importance of monitoring MS-SQL logs, which are crucial for detecting such compromises. Recommended practices include:
- Logging and Monitoring: Enhance surveillance of MS-SQL server connections, particularly from public IPs and after multiple failed authentications.
- System Configuration Watch: Monitor changes to critical system parameters like xp_cmdshell and clr settings.
- Behavioral Analysis: Use advanced analytics to detect unusual process behaviors and potential misuse of system tools.
Ongoing Monitoring
This exploitation highlights a significant shift in cybercriminal tactics, demonstrating a dual approach involving both targeted and broad attacks. The use of PureCrypter in conjunction with Mallox ransomware indicates a sophisticated, multi-stage attack strategy aimed at maximizing impact and profit.
The involvement of XHost Internet Solution’s AS208091 in previous ransomware incidents adds a layer of complexity to the threat landscape, suggesting possible recurring use of certain IP ranges in cybercriminal operations.