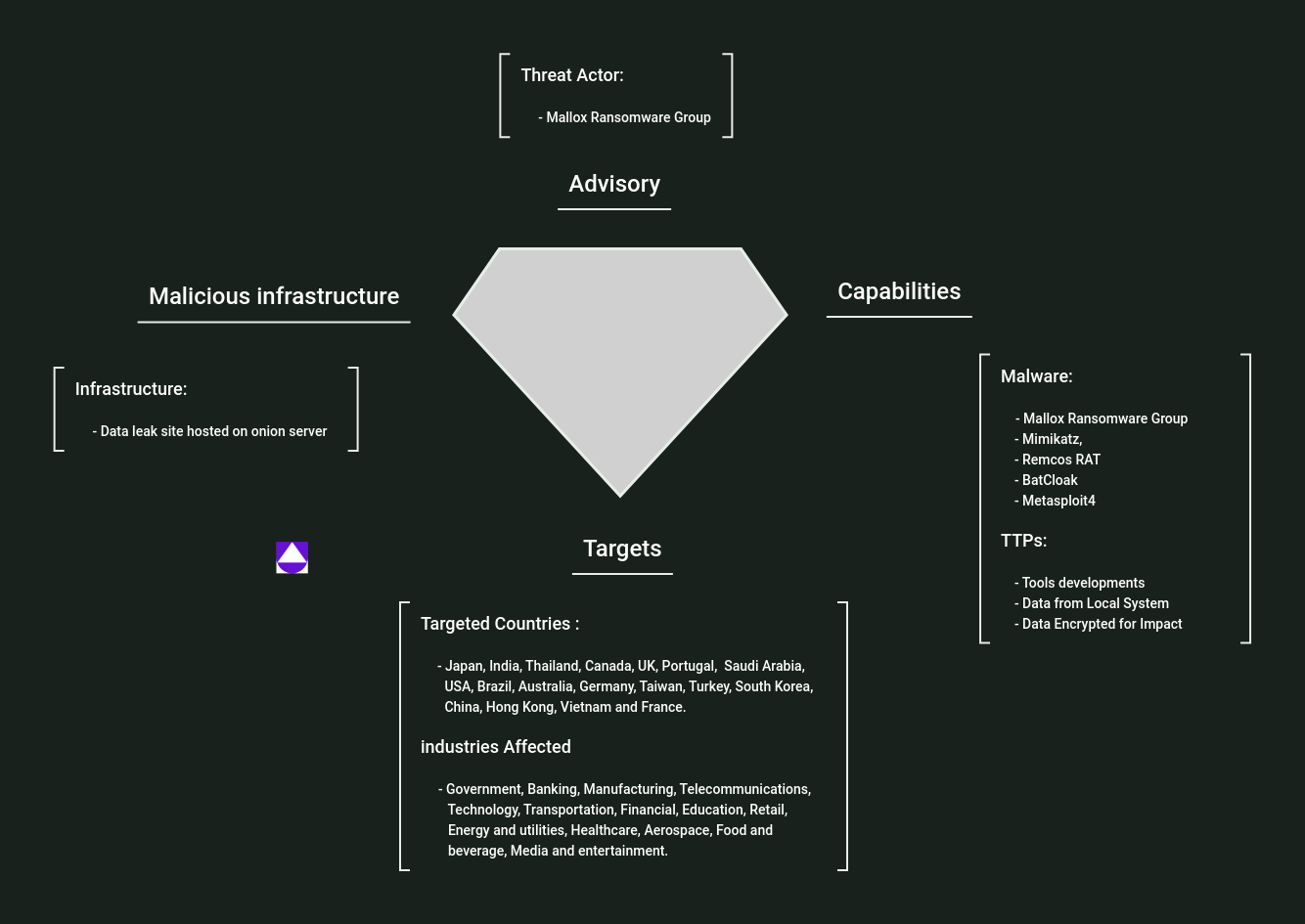
Mallox ransomware diamond model| Image: Uptycs
The notorious Mallox ransomware gang, known for their aggressive multi-extortion tactics, has expanded their arsenal with a new Linux variant. This marks a significant shift for the group, which traditionally targeted Windows systems with .NET-based payloads.
The new Mallox ransomware variant represents a significant shift, as it targets Linux systems using custom Python scripts. The Uptycs Threat Research team discovered a critical Python script named web_server.py during their investigation. This script is part of a Flask-based web panel used to create and manage ransomware payloads for Linux systems.
The script connects to a backend database using environment variables for credentials and includes functionalities for user authentication, build management, and administrative tasks. This allows for the creation of a fast and customizable ransomware for Linux, enabling admins to manage users, view logs, and perform account actions. The application also features a chat interface for builds and a custom 404 error page.
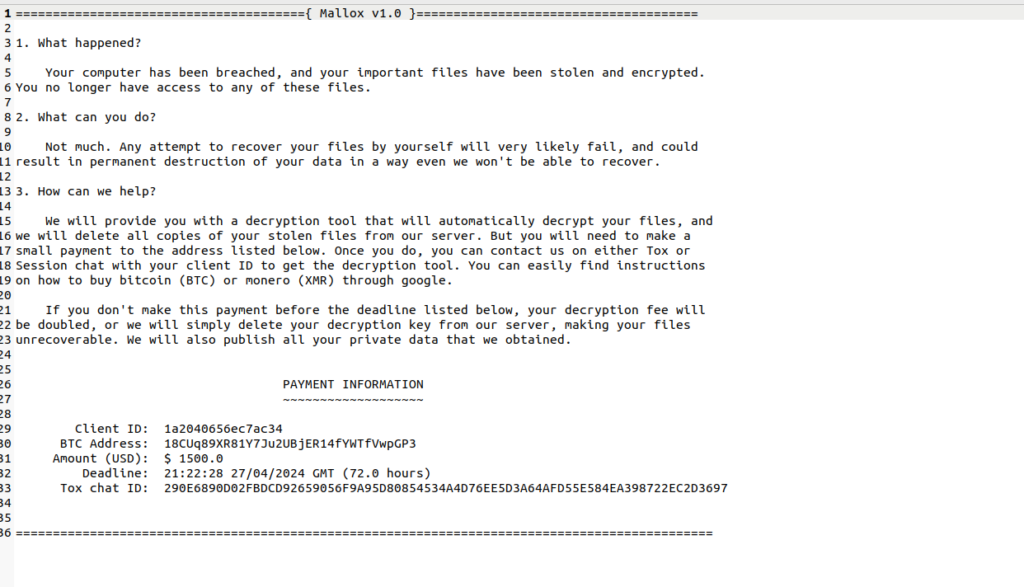
Upon examining the web_server.py script, it was found that the script hosts a Mallox ransomware encryptor and decryptor for registered users. The ransomware encrypts user data, appending a .locked extension to the encrypted files, and drops a ransom note named READ_THIS_NOW.txt. The payload delivery and victim information exfiltration are handled through custom scripts, with an IP address (185[.]73[.]125[.]6) identified in the host IP field, used to build the ransomware.
The Linux variant employs AES-256 CBC encryption with a hardcoded key and initialization vector (IV). This means that while the ransomware can encrypt files with the extension “.lmallox,” the same key and IV can be used to decrypt them. Notably, the Uptycs team has successfully recovered decryptors for several Mallox builds, offering potential relief to victims.
The configuration for the ransomware, including the ransom note, client ID, BTC address, amount in USD, deadline, Tox chat ID, note name, persist, target ID, and targeted directories, is embedded within the encrypted content.
Victims whose files have been encrypted by the Mallox ransomware Linux variant may be able to recover their data using the decryptors found at 185[.]73[.]125[.]6/output/{build-id}/decryptor. Uptycs has confirmed the availability of decryptors for the following build IDs:
- 1a2040656ec7ac34
- 7cc49d60f71e4ca4
- 84bb1f05ce370665
- 928bc7bf4d954d3d
- b90ae4c6e011c45e
- f6b040a56afcb6fb
- F65bccf063ee3cc6
For detailed technical insights and protective measures, refer to the full report by the Uptycs Threat Research team.