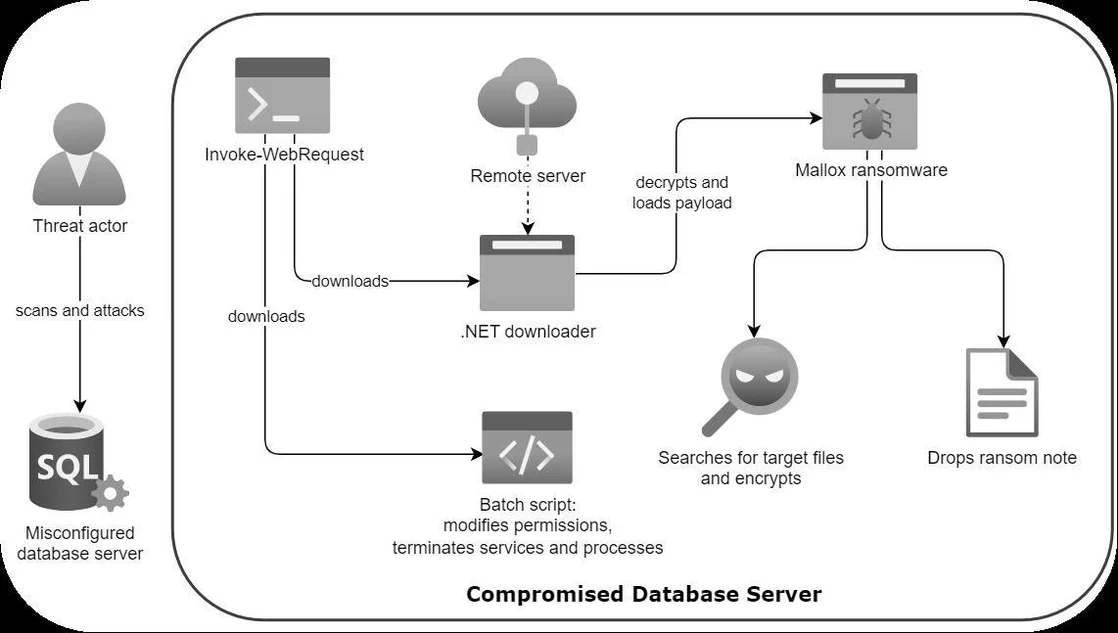
Mallox’s attack chain | Image: Trustwave
The recent Trustwave investigation into a Mallox ransomware attack sheds light on the methods and tools used by modern cybercriminals to infiltrate and compromise cloud-based environments. The attack, which targeted a misconfigured cloud server, highlights the growing sophistication and adaptability of ransomware operations, particularly those utilizing the Ransomware-as-a-Service (RaaS) model.
The incident began with an all-too-common security oversight: a misconfigured server. Exposed to the internet and listed on Shodan—a search engine designed to locate internet-connected devices—this vulnerable server became a key for threat actors. Almost immediately after its listing, the organization experienced a dramatic surge in suspicious activity, with daily events skyrocketing from 3,000 to over 60,000.
The attackers, identified as affiliates of the Mallox ransomware group, leveraged this exposure to initiate a brute-force attack on the exposed Microsoft SQL (MS SQL) server. Through a relentless series of unauthorized access attempts, they eventually breached the server, marking the beginning of a highly orchestrated ransomware campaign.
The Mallox ransomware group, also known as FARGO or TargetCompany, has exhibited a significant increase in activity in recent years. The adoption of a Ransomware-as-a-Service (RaaS) model has enabled the group to expand its reach by enlisting affiliates to carry out attacks on its behalf. This has resulted in a surge of Mallox-related incidents, with a notable spike observed in mid-2023.
The impact of Mallox ransomware attacks is widespread, affecting organizations across a diverse range of industries, including IT, manufacturing, retail, transportation, and government. The group’s modus operandi involves a double extortion tactic, where they not only encrypt data but also threaten to leak stolen information if the ransom demands are not met.
Once inside the compromised environment, the threat actors deployed a series of Invoke-WebRequest commands to download ransomware droppers, downloaders, and auxiliary batch scripts. These tools were meticulously crafted to enhance the attack, with some executables written in .NET acting as downloaders or droppers for the Mallox ransomware.
The technical analysis revealed a sophisticated use of encryption and obfuscation techniques. Some downloaders retrieved payloads encrypted with AES or 3DES, while others used simpler obfuscation methods. The dropper variants embedded their payloads within the executable’s resource section, decrypting them in real-time using hardcoded keys before executing the ransomware.
In addition to these tools, the attackers utilized batch scripts named Kill$-Arab.bat and Kill-Delete.bat, designed to modify file permissions, manage services, and conceal their presence. These scripts executed a series of commands to disable antivirus services, stop critical processes, and erase logs, ensuring the ransomware’s success and making it difficult for defenders to respond.
The Windows variant of Mallox ransomware employed the ChaCha20 encryption algorithm to encrypt files, appending the ‘.rmallox’ extension to all compromised files. The ransomware targeted database operations by terminating processes associated with SQL servers and encrypting critical data files, including .sql and .vhd files. By performing a language check, Mallox ensured it did not encrypt systems with Russian language settings, a common tactic to avoid scrutiny from Russian authorities.
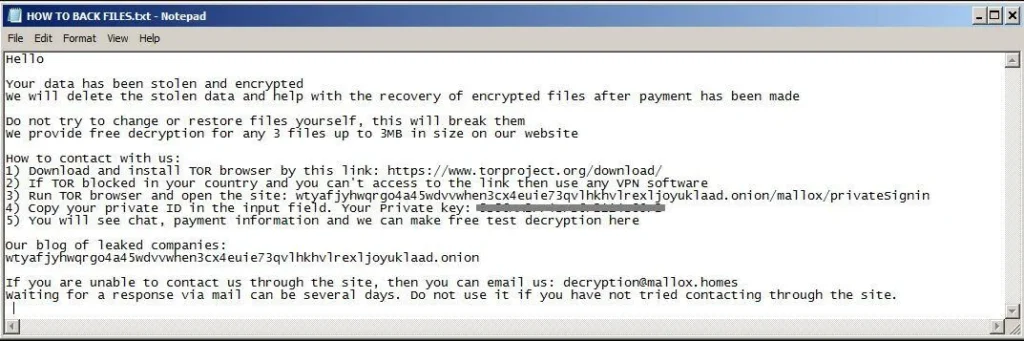
Mallox’s impact extended beyond data encryption. It disabled Recovery and Boot Protections, removed shadow copies to prevent data restoration, and modified system settings to prevent users from rebooting or shutting down their systems. The ransomware then dropped a ransom note titled HOW TO BACK FILES.txt, instructing victims on how to make payment via the TOR network in exchange for decryption keys.
To prevent similar attacks, organizations must take proactive measures:
- Restrict Public Access: Correct misconfigurations that allow unauthorized public access to cloud servers. Implement strict access control lists and firewall rules to limit access to only authorized IP addresses.
- Conduct Regular Audits: Periodically audit cloud environments to identify and address security gaps. This includes reviewing logs for unusual activity and ensuring that all configurations adhere to security best practices.
- Patch and Update: Keep all software and services up to date with the latest security patches to mitigate vulnerabilities that could be exploited by attackers.
Related Posts:
- Cyberattacks Soar in Q2 2024: BEC and Ransomware Dominate
- Mallox Ransomware Goes Cross-Platform: New Linux Variant Discovered, Decryptor Released
- Mallox ransomware Exploits Old Flaws in MS-SQL & ODBC
- TargetCompany Ransomware Group Escalates Attacks: New Tools and Persistent Targeting of MS-SQL Servers
- Mallox Ransomware Affiliates Target MS-SQL Servers with PureCrypter