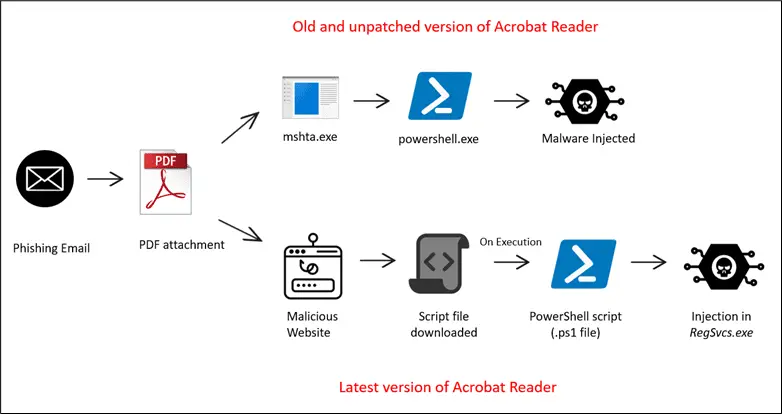
Infection Chain
A recent investigation by McAfee Labs has shed light on a significant surge in malware distribution through one of the most ubiquitous document formats: the PDF. This surge marks a concerning shift in cybercriminal tactics, exploiting the trusted nature of PDF files to unleash a wave of malicious activities.
With the introduction of Microsoft’s macro-blocking measures for Internet-delivered Office files, cybercriminals were cornered into finding new avenues for their nefarious activities. Enter the PDF: a format so common and trusted that it has become the perfect Trojan horse for cyberattacks. The complexity and versatility of PDFs make them ideal for embedding malicious code that can evade detection, exploiting the inherent trust users place in this document format.

Recent observations have uncovered a sophisticated infection chain that begins with a seemingly benign email attachment. For example, a PDF named “Booking.com-1728394029.pdf” promises legitimate content but instead serves as a gateway to malware. Embedded within the PDF’s structure are hidden URLs and JavaScript designed to redirect users to malicious sites, under the guise of familiar services. This redirection plays a critical role in the subsequent download and execution of malware, such as the notorious Agent Tesla.
The exploitation techniques vary depending on the version of Acrobat Reader installed on the victim’s system. In outdated versions, PDFs can directly execute embedded JavaScript, leading to the automatic launch of malicious payloads. In contrast, updated versions require a more convoluted process involving redirection to malicious websites, showcasing the adaptability of attackers in overcoming software defenses.
Agent Tesla demonstrates the intricate steps involved in modern malware distribution. From initial access via deceptive PDFs to the execution of obfuscated JavaScript files, the process is meticulously crafted to evade detection. The malware’s ability to disable system defenses, establish persistence, and exfiltrate sensitive data through secure channels like Telegram bots.
“This orchestrated sequence underscores the sophisticated nature of the attack, spanning from initial infection to data exfiltration and persistent infiltration, posing significant challenges for detection and mitigation efforts,” the researcher concludes.