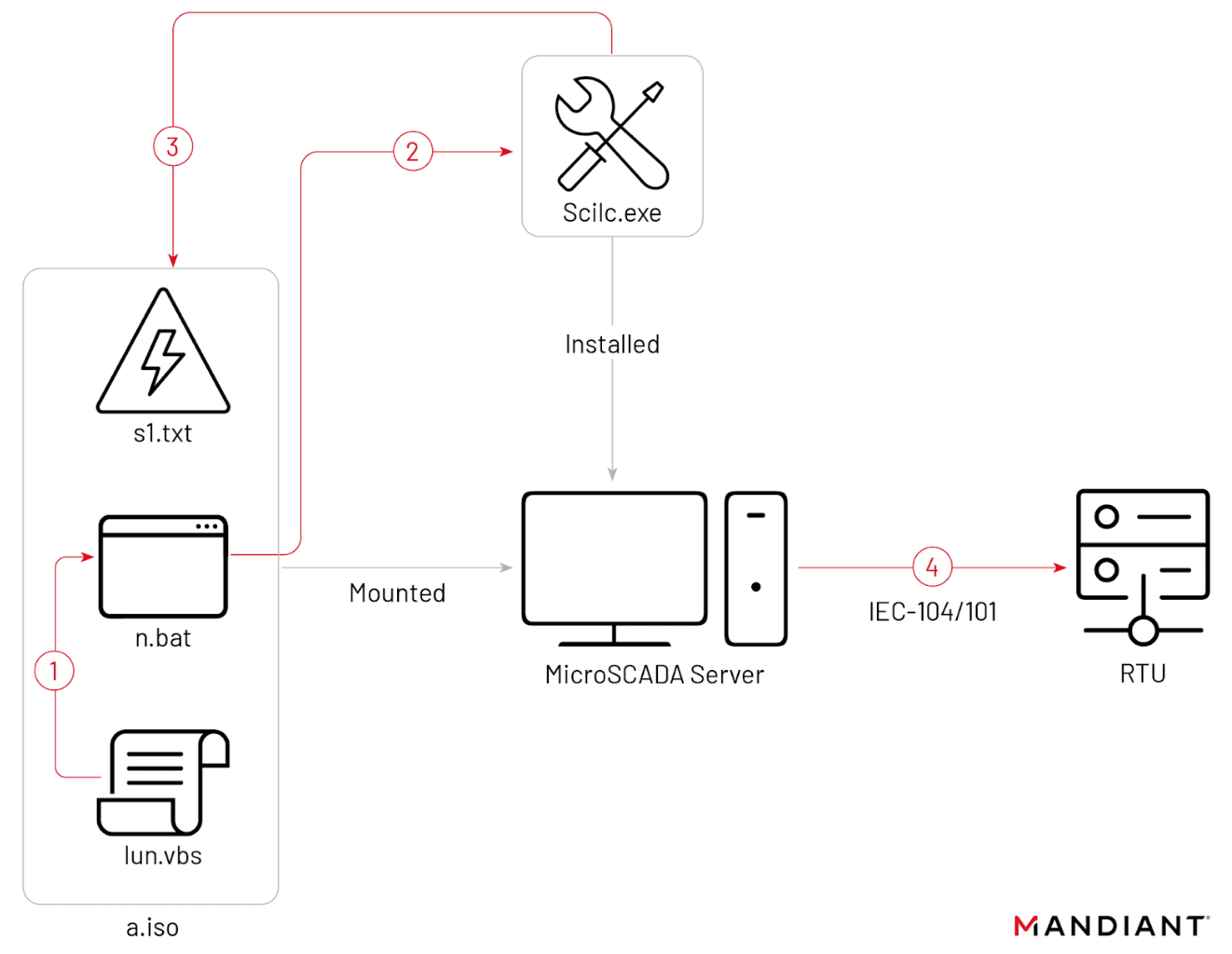
Execution chain of disruptive OT event
In the shadowy realm of cyber warfare, the Russia-affiliated group Sandworm has emerged as a formidable force, orchestrating an intricate cyber-physical attack on Ukrainian infrastructure. This offensive, unveiled by Mandiant in late 2022, disrupted a crucial organization’s operations by tripping circuit breakers during a simultaneous missile assault, casting a dark specter over the nation’s power grid.
Utilizing a novel approach that melds the physical and digital worlds, Sandworm’s strategy involved sophisticated industrial control system (ICS) and operational technology (OT) manipulations. Initially, they harnessed OT-level ‘living off the land’ tactics, deftly tripping substation circuit breakers to precipitate a power outage. Subsequently, Sandworm deployed a new strain of the formidable CADDYWIPER malware, sowing further chaos in the victim’s IT network.

This incident epitomizes the evolution of Russia’s cyber-physical attack capabilities. Sandworm’s adept use of LotL techniques signals a maturation in their offensive arsenal, unveiling an alarming proficiency in recognizing and exploiting novel OT threats. Their rapid development of this capability—estimated to have taken merely two months—poses a stark warning of their potential to unleash similar assaults on other OT systems worldwide.
Sandworm’s prowess isn’t newfound; their roots trace back to at least 2009, operating under Russia’s GRU. With a primary focus on Ukraine, their decade-long campaign has been marked by espionage and destructive attacks using wiper malware, a grim testament to their capabilities. Yet, their reach extends beyond Ukraine, with global espionage activities reflecting Russian military ambitions.
The timeline of the intrusion that culminated in the October 2022 attacks paints a picture of a methodically planned operation. Sandworm gained access to the OT environment through a hypervisor hosting a SCADA management instance, potentially laying in wait for up to three months. On October 10, they used a seemingly innocuous optical disc image to deliver malicious commands, shutting off power substations.
A mere two days later, the CADDYWIPER variant was unleashed, aiming to inflict further disruption and perhaps erase digital evidence of the onslaught. Interestingly, this wiper activity was constrained to the IT environment, sparing the SCADA system—a move that may suggest an operational oversight or lack of coordination within Sandworm.
The insidious nature of Sandworm’s substation assault provides a window into Russia’s investment in OT-oriented offensive cyber capabilities and its strategic approach to OT system attacks. Their operations show a trend toward streamlining disruptive activities, focusing on precise, high-impact maneuvers rather than a scattergun array of tactics.
The use of LotLBin techniques by Sandworm denotes a significant shift in the cyber warfare landscape. These methods, harder to detect due to their use of legitimate system tools, highlight the need for vigilant defense strategies.
In the broader context, the timing of this attack, aligned with Russia’s missile strikes, may point to a chilling synchronicity, underlining the need for heightened security measures globally, particularly for entities leveraging MicroSCADA systems. Sandworm’s demonstrated capabilities and intent serve as a clarion call to critical infrastructure operators worldwide: the threat is real, and the time to fortify against it is now.