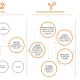
mando.me: Web Command Injection Tool

mando.me: Web Command Injection Tool
PHP Command Injection exploitation tool
- Exploit web page and upload simple-shell.php (or simply find an existing exploitable command injection).
- Execute the controller to exploit the command injection vulnerability. The controller is simply a command injection exploitation tool, and can therefore with a few adjustments be rewritten to exploit already existing vulnerabilities without the need for uploading the ‘simple-shell.php’.
- Automated exploit-injection via POST or GET (eg. ./mando.me.py –cookie “security=low;PHPSESSID=DEADBEEFDEADBEEFDEADBEEFDEADBEEF” –url “http://metasploitable:2280/dvwa/vulnerabilities/exec/” –post “{‘submit’:”,’ip’:_INJECT_}”)
- Encrypted agent communication
- Meterpreter/Reverse Shell Injection
- A more user friendly UI
- Built in post exlpoitation tools (enumeration, privilege escalation etc.)
- And much more…
Download
git clone https://github.com/z0noxz/mando.me.git
Use
(python) mando.me.py [options]
Options:
–help Show this help message and exit
–url Shell interface URL without paramters (e.g. “http://www.site.com/simple-shell.php”)–post Declare POST data (eg. “{‘submit’:”,’ip’:_INJECT_}”)
–get Declare GET data (eg. “{‘ip’:_INJECT_}”)
–cookies Declare COOKIE data (eg. “PHPSESSID=deadbeefdeadbeefdeadbeefdeadbeef”)
Shell commands:
Commands that are executable while in shell interfacemeterpreter Injects a PHP Meterpreter, PHP Reverse TCP Stager (requires a listener for php/meterpreter/reverse_tcp)
upload Upload a file
download Download a file
kill_self Cleans up traces and aborts the shell
exit Exits the shell