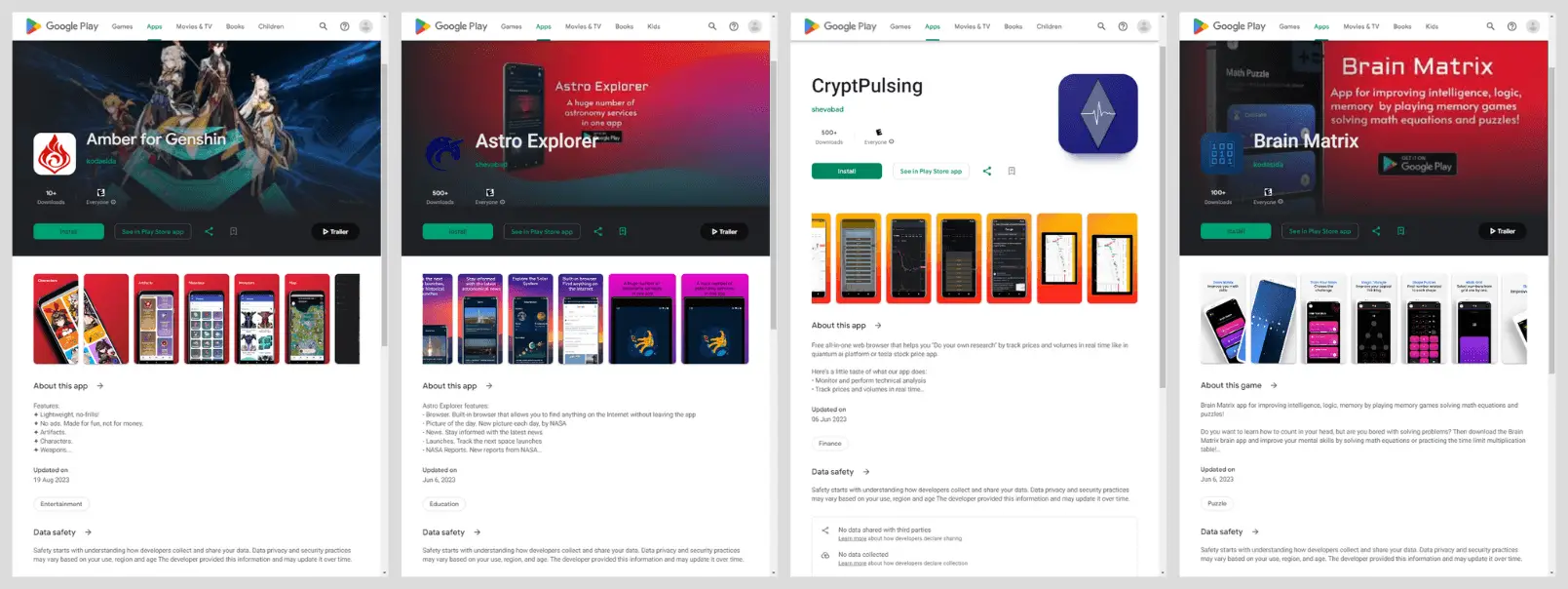
Mandrake applications on Google Play | Image: Kaspersky
Kaspersky researchers revealed the return of the Mandrake Android spyware, which has been discovered lurking on the Google Play Store for two years, amassing over 32,000 downloads across five different apps. This sophisticated cyber-espionage platform, first exposed in 2020, has resurfaced with enhanced obfuscation techniques to bypass security checks and hinder analysis.
Mandrake first gained attention with its major infection waves between 2016-2017 and 2018-2020. Bitdefender’s comprehensive analysis in May 2020 exposed its extensive capabilities and widespread impact. Despite the attention, Mandrake has resurfaced with new samples that showcase enhanced evasion techniques and deeper layers of obfuscation, enabling it to bypass Google Play’s security checks.
In April 2024, Kaspersky identified a new version of Mandrake. This discovery led to the detection of five Mandrake applications on Google Play, collectively amassing over 32,000 downloads since 2022. These applications included obfuscated native libraries and sophisticated certificate pinning for secure communication with command-and-control (C2) servers, making detection and analysis significantly more challenging.
The report highlights five applications that harbored Mandrake spyware:
- AirFS: A file-sharing app with over 30,000 downloads.
- Astro Explorer: A stargazing app.
- Amber: A photo editing app.
- CryptoPulsing: A cryptocurrency tracker.
- Brain Matrix: A brain-training game.
Among these, AirFS was the most prominent, disguised as a legitimate file-sharing tool but functioning as a vehicle for espionage.
The new Mandrake variant exhibits advanced obfuscation strategies. Key malicious functionalities have been moved to obfuscated native libraries, complicating the analysis process. Communication with C2 servers employs certificate pinning, preventing SSL traffic interception. Additionally, the spyware conducts extensive checks to evade sandbox environments and detect rooted devices or emulators.
The infection chain of Mandrake operates in stages: dropper, loader, and core. In the latest campaign, the first-stage malicious activity is hidden within the native library libopencv_dnn.so, which decrypts the next stage (loader) from the assets/raw folder. The application then requests permissions to draw overlays and collects detailed device information to decide on further actions.
The main goals of Mandrake include stealing user credentials and executing next-stage malicious applications. The spyware employs various commands to interact with the infected device, ranging from collecting system information to manipulating web views for credential theft.
The malicious applications were downloaded in various countries, with significant numbers in Canada, Germany, Italy, Mexico, Spain, Peru, and the UK.
For detailed technical insights and protection strategies, refer to Kaspersky’s full report on the latest Mandrake spyware findings.
Related Posts:
- Defend Your Cloud: 8220 Gang Targets Linux & Windows
- DarkGate Malware Resurfaces with New Campaign Tactics
- How Spyware Evades Detection through Advanced Obfuscation
- China-Linked GhostEmperor Resurfaces: Enhanced Demodex Rootkit Targets Southeast Asia
- New Agent Tesla Spyware Variant was spread via Microsoft Word documents