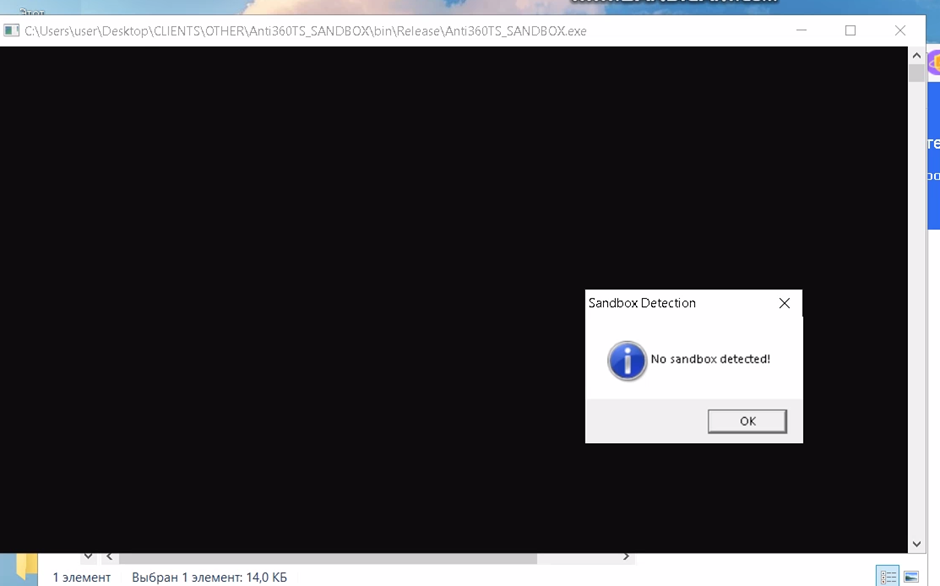
Sample of sandboxing detection bypass posted by the TA
Cyble Research & Intelligence Labs (CRIL) has uncovered the release of a new malware-as-a-service (MaaS) tool known as ManticoraLoader. The service, announced by the notorious threat actors behind the infamous AresLoader, has been available on underground forums and Telegram channels since August 8, 2024.
The developers behind ManticoraLoader are the same individuals responsible for the creation of AresLoader, a tool that has been actively targeting Citrix users since April 2023. Known by the alias ‘DarkBLUP,’ these threat actors have a well-established presence in the cybercriminal community, previously linked to the development of AiDLocker ransomware in late 2022.
ManticoraLoader is designed as a versatile and potent tool, compatible with a broad range of systems, including Windows 7 and later versions, as well as Windows Server. Its primary function is to gather extensive reconnaissance data from infected devices, such as IP addresses, usernames, system languages, installed antivirus software, UUIDs, and date-time stamps. This information is then transmitted to a centralized control panel, enabling attackers to profile victims, customize attacks, and maintain long-term control over compromised systems.
ManticoraLoader boasts several advanced features that make it a formidable tool in the hands of cybercriminals:
- Persistence: The loader is capable of placing files in auto-start locations, ensuring that it remains active on compromised systems even after reboots.
- Modularity: Its design allows for the easy extension of functionalities, making it adaptable to various malicious objectives, including ransomware deployment, data theft, and botnet management.
- Obfuscation: ManticoraLoader employs sophisticated obfuscation techniques to evade detection by security software, making it a stealthy threat that can bypass even advanced defenses.
- Exclusivity: The service is offered under strict terms, with a monthly rental fee of USD 500 and a limit of just 10 clients. This exclusivity may be intended to reduce the risk of detection and maintain the loader’s effectiveness in targeted campaigns.
- Detection Evasion: The loader’s reported detection rate of 0/39 on Kleenscan underscores its ability to fly under the radar, while a video demonstration posted by the developers shows ManticoraLoader successfully bypassing the 360 Total Security sandboxing solution.
As cybercriminals continue to innovate and refine their tools, organizations must remain vigilant in their cybersecurity efforts. The advanced obfuscation techniques and modular design of ManticoraLoader, coupled with its ability to evade detection, underscore the need for robust and adaptive security measures.
Related Posts:
- India Post Customers Targeted in Massive Phishing Scam
- Rhadamanthys Stealer: MaaS Malware Hits Oil & Gas
- Cybercriminals Target Indian Android Users with Sophisticated “Malware-as-a-Service” Scam
- PEAKLIGHT Malware: A New Stealthy Memory-Only Threat Emerges
- Financially Motivated Hackers UAC-0006 Resurface with New Attacks Targeting Ukraine