The new MATA infection chain | Image: Kaspersky
In a concerning cyber-espionage campaign that unfolded in September 2022, cybersecurity experts from Kaspersky identified a slew of fresh malware samples linked to the notorious MATA cluster. What followed was the revelation that prominent corporations in the oil, gas, and defense sectors of Eastern Europe had been targeted since mid-August of the same year.
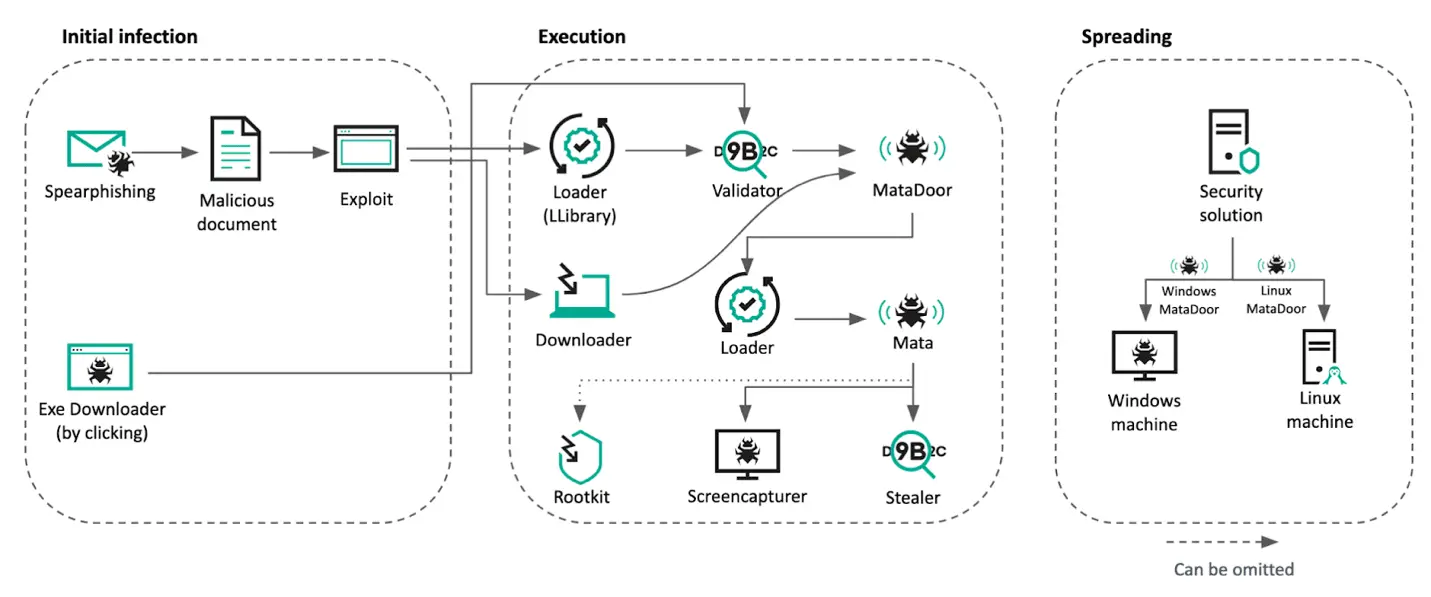
Utilizing spear-phishing emails as their weapon of choice, the attackers successfully duped victims into downloading malicious Windows executables. These deceptive documents were embedded with external links that, when clicked, led to a remote page housing the CVE-2021-26411 exploit. These unsolicited emails carrying malicious payloads persisted until September’s end, meaning the campaign spanned a staggering nine months.

Upon thorough examination of the malware and its functions, researchers discerned the attack’s infection chain, albeit with some obscurities. The culprits exhibited adaptability by merging traditional techniques, evident from earlier MATA campaigns, with evolved malware capabilities. They also incorporated a verification procedure to screen compromised victims, ensuring a meticulous malware delivery system.
A breakthrough moment arrived when two MATA samples were identified with internal IP addresses slated as Command and Control (C&C) server addresses. A unique modus operandi involved the attackers constructing a cascade of proxy servers, particularly if the tainted system was offline. The spotlight shifted when malware was detected on a financial software server, having access to multiple subsidiaries of a targeted firm. The magnitude of this breach was initially underestimated, but it was soon clear that the infection had seeped deep into the organization’s fabric.
The attackers’ journey began with a simple phishing email at a factory, which, once clicked, allowed them to traverse the entire network. Gaining user credentials, they swiftly infiltrated the terminal server and replicated their assault on a grander scale. A crucial element of their success lies in exploiting vulnerabilities within genuine drivers and rootkits. This enabled them to manipulate antivirus systems, amass user credentials, and weave through the network seamlessly.
In a calculated move, the attackers took control of the company’s domain controller. Their ambitions didn’t end there; they accessed the control panels of dual security solutions. With a twofold plan, they first breached a system meant to monitor compliance with security regulations. Their next step was accessing an endpoint protection solution. Both these security platforms, ironically, facilitated the attackers in gathering intelligence on the targeted infrastructure and dispersing the malware more efficiently.
The culmination of their assault was leveraging centralized security management systems, allowing the perpetrators to infect multiple subsidiaries and even seep into Unix-based servers with a Linux-specific MATA variant.
This case serves as a stark reminder of the evolving complexities of cyber threats, emphasizing the need for continuous vigilance, proactive measures, and prompt action in the face of potential breaches.