medusa
Medusa is an extensible framework for Android applications which automates processes and techniques practised during the dynamic analysis of a malware investigation.
Some of the framework’s features are the following:
- Tracing and instrumentation of API calls used by common malware categories
- Tracing and instrumentation of Java and Native functions
- Unpacking (effective for most of the weel known packers, including Qihoo, Secshell e.t.c.)
- Patching (e.g. autoset the debuggable flag)
- Triggering of various system events in order to initiate a malicious behaviour
- Triggering of application’s components (Activities, Services e.t.c.)
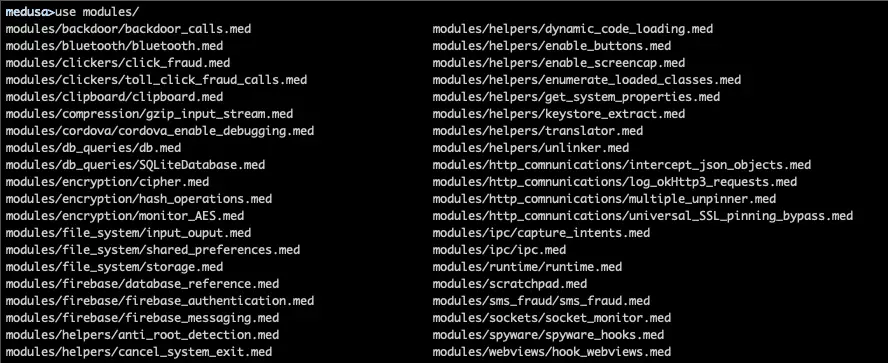
Medusa’s functionality is based on the following scripts:
- medusa.py
Is used to dynamically add or remove tracing of API calls during application’s runtime. The tracing ‘comes’ in a form of modules, where each one of them ‘specializes’ in an abstract aspect. As an example, to trace the cryptographic procedures of the application (e.g. fetch AES keys or the plaintext that will be encrypted), simply inject the AES module and observer the output.
Indicatively some of the functionalities which are implemented so far, include the following:
- SSL pinning bypass
- UI restriction bypass (e.g. Flag secure, button enable)
- Class enumeration
- Hook native functions
- Monitoring of:
- Encryption process (keys, IVs, data to be encrypted)
- Intents
- Http communications
- Websockets
- Webview events
- File operations
- Database interactions
- Bluetooth operations
- Clipboard
- Monitoring of API calls used by malware applications, such as:
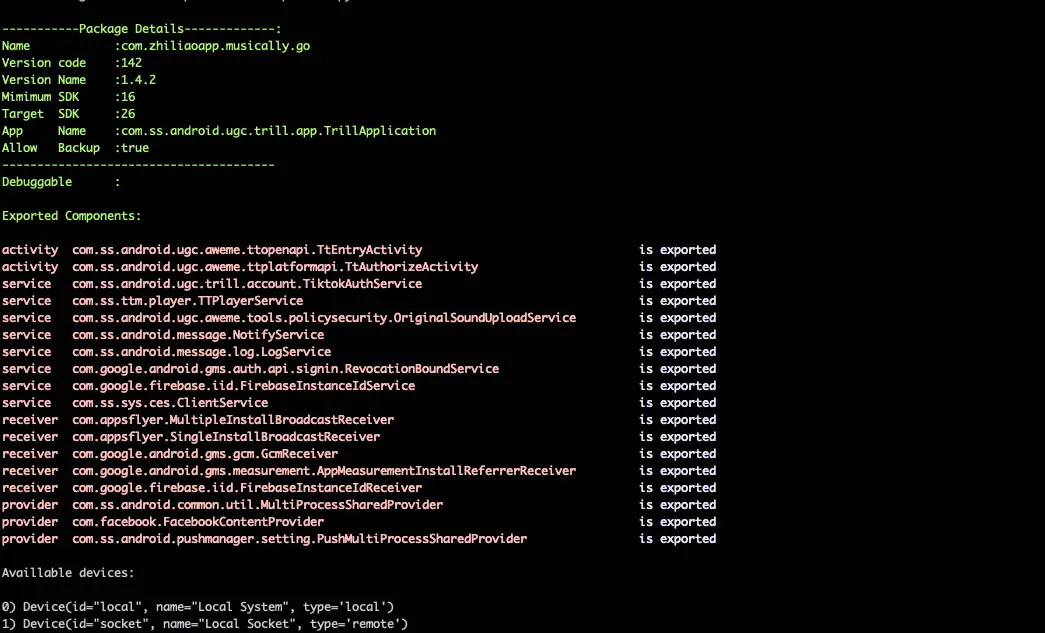
- apkutils.py
Given a manifest or and apk file, the specific script is able to perform the following functionalities:
- Display the application’s components and technical characteristics, including:
- Activities
- Services
- Receivers
- Permissions
- Intent Filters
- Content providers
- Trace application functions
- Trigger an activity, service or an intent
- Automate actions performed during dynamic analysis:
- Change device proxy settings
- Capture screenshots of the device
- Install/Uninstall/kill an application
- Patch (set the debug flag to true) / Sign / Install
- Display the application’s components and technical characteristics, including:
Install
git clone https://github.com/Ch0pin/medusa.git
cd medusa
pip install -r requirements.txt