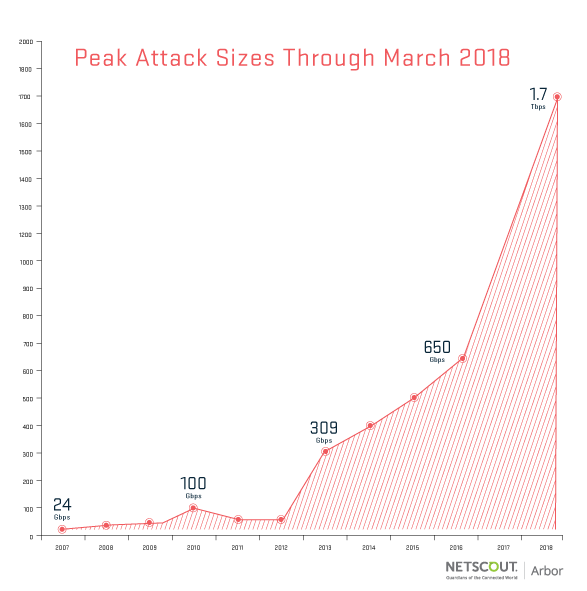
On March 6 news, 1.3Tbps Distributed Denial of Service (DDoS) attack suffered last week following the Github flow speed, network security monitoring company Arbor Networks confirmed that a US service providers are also facing up to the peak flow 1.7 Tbps reflection/amplification attacks.
Although this 1.7Tbps event is similar to the DDoS attack that occurred on GitHub last week, its bandwidth is magnified by more than 51,000 times due to the use of thousands of exposed and misconfigured Memcached servers on the Internet.
It is reported that after the GitHub incident, its customers received a blackmail, threatening them to purchase 50 XMRs (Monero) worth more than $15,000. The hacker’s current article does not specify whether there will be a ransom for this incident.

Arbor Networks stated that while reflection/amplification attacks are not new, the latest attack vectors have evolved into thousands of misconfigured Memcached servers, many of which are still exposed on the Internet and may be exploited against other targets. Launch a large-scale attack.
Arbor Networks expects more such attacks in the coming days. Therefore, to prevent the Memcached server from being misused as a reflector, Arbor Networks urges users to install a firewall and restrict access to the Memcached server from the local network only. In addition, administrators should also consider avoiding external traffic through the ports used by memcached (such as the default 11211 port) and block or limit UDP in a timely manner. If not necessary, it is best to disable UDP support completely.
Source: thehackernews