On Feb. 27, Cloudflare and Arbor Networks warned on Tuesday that malicious attackers were abusing the Memcached protocol to launch a distributed denial of service (DDoS) amplification attack that affected many servers worldwide, including Arbor Networks.
memcached is a high-performance, distributed memory object caching system for dynamic web applications to reduce database load. It reduces the number of database reads by caching data and objects in memory, increasing the speed of dynamic, database-driven Web sites. In addition, clients can communicate with the memcached server over TCP or UDP on port 11211.
In this (DDoS) zoom-in action, an attacker sends a request to a target server on port 11211 using a fake IP address that matches the victim IP. While the attacker’s request to the server was only a few bytes long, its response was tens of thousands of times higher than normal, a situation that could result in serious attacks. It is clear from Cloudflare that attackers are abusing unprotected Memcached servers that have UDP enabled. These servers come from around the world but are mainly in North America and Europe, and most of the servers currently hosted by OVH, DigitalOcean, and Sakura.
The largest Memcached DDoS attack currently observed by Cloudflare is 260 Gbps, but Arbor Networks said it has detected 500 Gbps of attack and may even be taller. Arbor Networks noted that the type of queries used in these attacks could also target TCP port 11211, but the possibility of the protocol being misused is not high because TCP queries cannot be truly deceived.
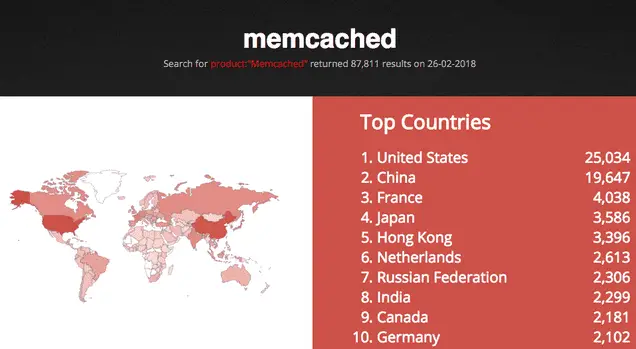
According to attack data monitored by the CDN (Content Delivery Network), there are currently about 5,700 IP addresses associated with Memcached servers, but experts expect a bigger attack in the future as Shodan shows nearly 88,000 open servers. The most exposed systems are currently in the United States, followed by China and France.

Cloudflare recommends disabling UDP support if not necessary and reminding system administrators to ensure that their servers are not accessible from the web. In addition, Internet service providers (ISPs) can also help reduce this or other types of magnification attacks by fixing vulnerable protocols and preventing IP spoofing.
Source: SecurityWeek